Key Takeaways
- WHOIS is a foundational, decentralized protocol for querying domain registration and ownership data, critical for verifying domain ownership, troubleshooting DNS issues, enforcing security policies, and managing domain lifecycle events.
- A deep understanding of WHOIS data structures, access modalities, and privacy constraints—including GDPR compliance—is essential for engineers designing systems that integrate domain registry information, ensuring data integrity alongside legal and operational compliance.
- Functioning as a distributed metadata repository, WHOIS’s implications extend beyond registry transparency to influence DNS management, security monitoring, and identity verification workflows.
- WHOIS operates over a TCP-based query-response model standardized by ICANN, exposing semi-structured domain registration data managed by registrars; however, the protocol’s heterogeneous implementations and rate limiting impose significant design considerations for scalability and reliability.
- WHOIS records typically contain registrant and registrar details, domain lifecycle metadata, and domain status flags, all modeled as key-value pairs requiring normalization across diverse record formats and inconsistent registry implementations.
- Access to WHOIS data occurs through command-line clients, web portals such as ICANN Lookup, provider-specific interfaces, and API endpoints—with critical awareness needed for protocol variations, such as legacy WHOIS (port 43) versus RDAP, as well as error handling.
- Privacy regulations, particularly GDPR, mandate data redaction and support proxy registrations that obscure registrant information, complicating automated ownership validation and enforcement processes.
- Clear differentiation between registrant (domain owner) and registrar (domain seller/operator) data is fundamental for ownership validation, operational communication, and incident remediation workflows.
- Scalability of WHOIS lookups is limited by query throttling, inconsistent data freshness, and infrastructure unreliability, necessitating distributed querying, caching strategies, and fallback mechanisms.
- Domain lifecycle events exposed in WHOIS data underpin domain monitoring, renewal automation, and alerting systems critical for operational governance.
- Operational reliability depends on accommodating heterogeneous WHOIS server implementations, inconsistent response formatting, and network-level instability.
- WHOIS privacy features present a trade-off between personal data protection and operational transparency, often necessitating manual verification or augmented data sources for compliance and trustworthiness.
- Integrating WHOIS data with DNS records and IP lookups enhances domain context understanding but introduces system complexity due to cross-protocol correlation and data inconsistency.
This guide provides an in-depth exploration of WHOIS data structures, protocol mechanics, privacy implications, and practical methods for scalable querying, equipping engineers to build robust, privacy-aware domain management and verification systems.
Introduction
WHOIS forms the backbone for domain ownership verification, yet its inherently distributed and inconsistent architecture often transforms straightforward queries into complex challenges involving protocol idiosyncrasies, rate limiting, and privacy-driven data redactions. Engineers aiming to integrate domain registration data need to recognize that naive mass querying of WHOIS servers is fraught with pitfalls, such as parsing fragmented key-value pairs, handling constrained access quotas, and interpreting privacy-protected fields mandated by GDPR and other legislation.
This raises fundamental questions: What exactly is WHOIS? How does the protocol expose domain registration data, and what practical constraints shape its deployment in modern distributed infrastructure? This guide addresses these by methodically dissecting WHOIS data structures, comparing query methodologies—including command-line clients, ICANN Lookup, and application programming interfaces—and evaluating the operational impact of privacy regulations on data completeness and integrity.
Understanding these trade-offs is essential for designing systems that can efficiently extract, normalize, and validate domain ownership information while skillfully navigating challenges in scalability, accuracy, and compliance with evolving regulatory frameworks.
Understanding What Is WHOIS and Its Purpose
At its core, WHOIS is a distributed query protocol expressly devised to expose registration and ownership metadata for Internet domain names. In contrast to centralized directories, WHOIS operates through a decentralized architecture where multiple WHOIS servers—maintained by registries and registrars—each serve a segment of the domain namespace. Query routing ensures that lookups reach the authoritative source managing the domain in question, enabling precise, domain-specific data retrieval.
The fundamental purpose of WHOIS is to provide transparency and accountability in domain name management. Every domain—ranging from generic top-level domains (gTLDs) like .com and .net to country-code top-level domains (ccTLDs) such as .uk or .de—carries associated metadata detailing domain control, configuration, and lifecycle events, including creation, modification, and expiry dates. This information supports domain owners in verifying registrations, registrars in managing renewals and transfers, cybersecurity teams in threat investigations, and law enforcement in digital ownership attribution.
WHOIS data availability and structure reflect regulatory and governance frameworks established by entities like ICANN (Internet Corporation for Assigned Names and Numbers). ICANN provides guidelines standardizing required data collection and publication while granting registry operators limited discretion in formatting and presentation. This decentralized policy leads to variability in data formats and field completeness across TLDs, complicating automated parsing and system integration. For authoritative policy details, see ICANN WHOIS Data Reminder Policy.
A critical distinction within WHOIS records is between registrant and registrar data. The registrant is the individual or legal entity that owns or controls the domain. This may be a person, company, or organization responsible for domain use. Registrant information typically includes contact details—postal addresses, email, and phone numbers—though privacy protections can result in redaction or masking. Conversely, the registrar is the accredited organization that facilitates domain registration, maintains domain records, and interacts with registries to manage ownership and DNS records. Registrar metadata includes identifiers, contact points, and often billing or technical contacts.
WHOIS records encompass a rich set of domain management and operational fields, including:
- Domain status codes: Indicating current states such as active, locked, pending transfer, or expired, crucial for automating lifecycle workflows.
- Creation date: Timestamp of initial domain registration.
- Expiration date: When domain registration lapses unless renewed.
- Updated date: Time of the latest record modification.
- Name server listings: Authoritative DNS servers responsible for resolving the domain.
- Administrative and technical contacts: Designated roles for managing administrative and technical domain responsibilities, enabling coordination during incidents or configuration changes.
Notably, registry policies influence variations in these fields. ccTLDs might enforce localized contact requirements or stricter data privacy, while some gTLDs may have more verbose record formats. This heterogeneity mandates flexible and adaptive parsing logic in automated systems.
Understanding the WHOIS landscape and typical data structures forms a necessary foundation before addressing the protocol mechanics and practical access methods discussed next.
How WHOIS Works and Common Access Methods
Building on the fundamentals of WHOIS data structure, it is essential to understand the underlying protocol mechanics and typical access methods, as these dictate both engineering design choices and operational constraints.
The WHOIS protocol uses a simple client-server model over TCP port 43. A WHOIS client opens a TCP connection to the authoritative WHOIS server responsible for the domain’s registry or registrar, sends a plaintext query (typically the domain name terminated by a newline), and receives a plaintext response containing the domain’s registration data. Despite its simplicity, this model operates across a decentralized network of servers, each authoritative for a specific namespace slice.
Given the diversity of authoritative WHOIS servers—such as Verisign for .com domains or Nominet for .uk—client applications or lookup services must intelligently route queries. Strategies for routing include:
- Direct querying, where clients connect directly to a known authoritative server, often configured by hard-coded server addresses or DNS SRV resolution.
- Referral chaining, where initial WHOIS responses contain pointers to registrar-level WHOIS servers for more detailed information, requiring iterative client connections.
- Centralized lookup services like ICANN Lookup, which aggregate data from multiple WHOIS sources, abstract referral logic, and present unified results.
Common WHOIS access modalities include:
- Command-line WHOIS clients: Ubiquitous in Unix-like environments, the
whoisutility connects over port 43 to issue direct domain queries, providing lightweight and scriptable interfaces favored by system administrators and security analysts. Examples include runningwhois example.comto retrieve raw registration data. - Browser-based lookup portals: Websites such as ICANN Lookup, GoDaddy WHOIS, and Network Solutions provide user-friendly UIs that often employ backend aggregation and normalization, implementing rate limiting and caching to handle high traffic volumes gracefully. These tools may offer historical data, bulk lookup, and formatted outputs.
- API-driven access: Programmatic WHOIS APIs enable integration into domain management systems, SIEMs, and threat intelligence platforms. These APIs abstract away protocol heterogeneity by providing structured JSON or XML responses, facilitating automated bulk lookups and change monitoring at scale.
However, several technical complexities arise:
- Lack of standardized response formats: WHOIS servers emit unstructured or semi-structured text, with inconsistent labels, field order, and formatting, necessitating custom parsers for each registry or registrar. Open-source parsing libraries exist but are inherently limited by this diversity. For protocol details, see RFC 3912 — WHOIS Protocol Specification.
- Rate limiting and throttling: To prevent abuse, many WHOIS servers impose strict query limits per IP address, connection, or time window, requiring clients to implement retry and backoff logic or distribute queries across IP pools.
- Data redaction mandated by privacy laws: GDPR and related regulations have resulted in widespread masking or anonymization of personal registrant data, reducing the completeness of WHOIS responses.
- WHOIS privacy services: Proxy or privacy protection substitutes registrant contact details with third-party service information, complicating ownership verification and abuse handling.
Related, but functionally distinct, are DNS and IP address lookups performed via tools such as nslookup or dig, which resolve domain names to IP addresses or query name servers. These tools do not replace WHOIS, as they address domain resolution and network configuration rather than registration metadata. Nonetheless, integrating WHOIS data with DNS and IP information often produces richer analytical insights.
Operational realities emphasize the importance of designing WHOIS systems that handle parsing heterogeneity robustly, respect query limits, and cope with privacy redactions, leveraging caching and distributed architectures to scale effectively. The transition from understanding WHOIS data to addressing parsing and normalization issues follows naturally from these protocol and access layer complexities.
WHOIS Record Data Structures and Available Information
Transitioning from protocol mechanics, we now delve deeply into the schemas and content of WHOIS records themselves. Understanding the typical data structures, their variability, and data semantics is vital for engineers tasked with consuming, normalizing, and operationalizing WHOIS information within production systems.
Types of Data Available in WHOIS Records
A WHOIS record is fundamentally a structured collection of key-value pairs that disclose details about domain registration, ownership, and lifecycle state. The primary data categories include:
Registrant Data:
The registrant represents the legal entity or individual controlling the domain. This section comprises identity fields such as full name, organization, postal address, email, and phone numbers. However, registrant data completeness varies by TLD and is heavily influenced by privacy regulatory compliance; fields may be partially or wholly redacted or replaced with proxy contacts. Parsing registrant data reliably requires flexibility to handle absent, masked, or variant field labels, as well as differences in language or format.
Registrar Details:
The registrar is the accredited entity responsible for the domain registration process. Relevant information includes registrar identifiers (e.g., IANA ID), WHOIS server URLs, and contact data such as abuse or technical contacts. Registrar data is typically better standardized than registrant data and plays a critical role in operational workflows—particularly for renewals, transfers, disputes, and abuse mitigation.
Domain Lifecycle Metadata:
WHOIS records include temporal and status metadata characterizing the lifecycle status of the domain, such as:
- Creation Date: When the domain was initially registered.
- Expiration Date: The domain’s registration expiry date if not renewed.
- Last Updated: The date when the WHOIS record was last modified.
Domain Status Codes:
These codes reflect operational constraints on the domain, facilitating management and security controls. Examples include:
clientTransferProhibited: Prevents unauthorized transfers, a common anti-hijacking measure.redemptionPeriod: A grace period following expiration allowing domain recovery.pendingDelete: Final stage before permanent deletion.
These statuses conform to EPP (Extensible Provisioning Protocol) domain states administered by registry backends. See IETF RFC 5731 for detailed EPP specifications.
Name Server Listings:
The authoritative DNS servers assigned to the domain, essential for resolving domain names to IP addresses.
Administrative and Technical Contacts:
Specified individuals or teams responsible for managing administrative and technical issues related to the domain, providing essential points of contact during incidents or configuration changes.
Distinction Between Registrant and Registrar Data—Schema Implications
Differentiating registrant from registrar data is critical: registrant data asserts ownership and legal control, while registrar data identifies the service provider managing registration. This separation supports distinct verification workflows—ownership validation versus administrative coordination and remediation.
In WHOIS responses, registrant sections usually contain personally identifiable information (PII) subject to privacy laws, whereas registrar sections contain organizational metadata with standardized and more stable contact points. Effective WHOIS parsers must extract these blocks independently and maintain their semantic distinction for accurate cross-referencing in downstream applications such as threat intelligence or compliance auditing.
Variability Across TLDs and Data Field Mandates
TLD registries define their own policies on mandatory, optional, or redacted WHOIS fields, creating a non-uniform data landscape. Legacy gTLDs like .com or .net may require detailed registrant info but allow masking via privacy services; newer gTLDs can have varied requirements, with some enforcing stricter transparency policies.
ccTLD registries often impose local rules mandating specific physical addresses or locale-specific contact details, further fragmenting standardization. Consequently, WHOIS parsers must be TLD-aware and employ modular template or configuration mechanisms to correctly interpret the diverse field sets and formats.
Challenges and Edge Cases in WHOIS Data Usability
- Formatting inconsistencies: Legacy plain text responses lack structured schemas, producing variances in field labels, delimiters, and ordering. Parsing must tolerate these irregularities.
- Missing or proxy data: GDPR-driven redactions or privacy services omit or replace registrant PII. Automated systems must anticipate incomplete records, requiring fallback mechanisms or human-in-the-loop validation.
- Registry-specific variations: Different registries may use distinct keywords, embed multilingual comments, or vary in field availability, complicating generic tooling.
- Data freshness delays: WHOIS databases may undergo delayed synchronization or batch updates, causing temporary inconsistencies that impact real-time workflows.
Addressing these demands robust error handling, multi-source validation, and privacy-respecting design patterns in production WHOIS ingestion pipelines.
Relation Between WHOIS Data and IP Address or DNS Lookups
Understanding WHOIS relative to DNS and IP queries uncovers their complementary but distinct roles in domain and network management, essential knowledge for engineers integrating multi-source data.
WHOIS as a Domain Ownership Database Versus DNS Resolution Systems
WHOIS primarily concerns itself with domain registration ownership and metadata, maintained collaboratively by registries and registrars. Its queries interrogate database-like repositories rather than dynamic routing infrastructure.
DNS, by contrast, is a high-availability, distributed directory system designed to rapidly resolve domain names into IP addresses or other resource records. DNS lookups traverse hierarchical caches and authoritative servers to produce near real-time resolutions. For detailed operational insight, see the Cloudflare DNS Learning Center.
From a systems architecture perspective, WHOIS data resides in relatively static registration databases, optimized for ownership tracking, while DNS data is dynamic and tuned for performance and scale in resolution services.
IP Address Discovery and Relation to WHOIS Data
Commands such as ipconfig (Windows) or ifconfig/ip addr (Linux) reveal network interface IP configurations for a host—ephemeral, local addresses independent of domain ownership. These data points operate at the OS and network stack level, distinct from the domain ownership metadata maintained in WHOIS.
Thus, querying IP address info on a host does not substitute WHOIS data, though correlating IP ownership via reverse WHOIS or tracking domain-IP mappings enriches investigatory context.
Complementary Uses of WHOIS Data with DNS and Reverse IP Lookups
WHOIS, DNS, and IP queries often intersect in tooling for security, operations, and diagnostics:
- Security analysts might begin tracing suspicious activity from an IP address, use reverse DNS to identify associated domains, and then query WHOIS for ownership and registrar details critical for abuse takedown or policy enforcement.
- Incident responders verify WHOIS ownership metadata to assess domain legitimacy when domains surface in threat intelligence or network scans.
- Domain status flags in WHOIS support detection of hijacking attempts or unauthorized transfers, complementing DNS and IP monitoring.
However, ownership association at the IP layer is complicated by CDNs, shared hosting, and proxy infrastructure, which decouple domain registrant identity from transient IP usage. Engineers must treat WHOIS and DNS/IP data as complementary layers—ownership metadata versus resolution and addressing resources.
Architecting Integrated Lookup Toolchains and Limitations
Operational platforms commonly integrate WHOIS lookups with DNS and IP data through unified dashboards, automating data correlation to simplify investigative workflows. Examples include ICANN lookup, GoDaddy WHOIS, and Network Solutions tools offering aggregated data views.
Yet, privacy regulations and proxy services restrict WHOIS data fidelity, often returning anonymized or generic proxy contacts that limit transparency. These challenges necessitate supplemental data sources, subscription services, or enhanced validation layers to maintain effectiveness.
Architecting such integrated systems requires reconciling differing freshness, structural complexity, and privacy constraints across WHOIS, DNS, and IP data sources to provide robust and actionable domain intelligence.
Impact of Privacy Laws and WHOIS Data Redaction
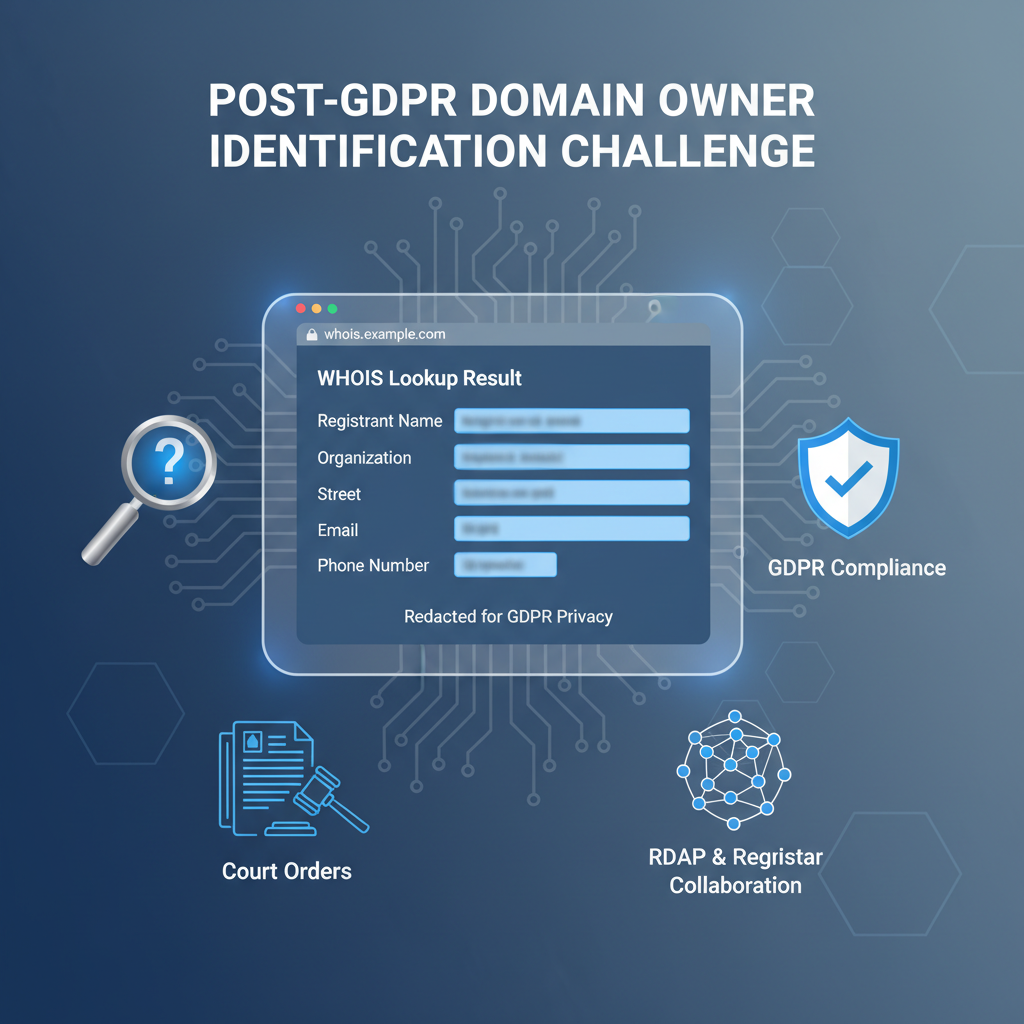
WHOIS was originally conceived as an open directory protocol exposing comprehensive registrant contact details. However, landmark privacy regulations such as the European Union’s General Data Protection Regulation (GDPR) have mandated widespread changes, profoundly reshaping WHOIS data disclosure practices.
GDPR imposes strict limitations on releasing personally identifiable information (PII) without lawful basis or explicit consent. Consequently, domain registries and registrars have been compelled to redact or anonymize registrant data fields in WHOIS responses, replacing names, emails, addresses, and phone numbers with neutral placeholders like “REDACTED FOR PRIVACY” or contact information of privacy proxy services. Refer to the ICANN GDPR Compliance Overview for regulatory details.
This fundamental shift has operational implications for systems and teams relying on WHOIS as a domain ownership source:
- Reduced data completeness: Automated workflows encountering redacted registrant fields may fail ownership verification steps or incident triage routines.
- Privacy proxy obfuscation: WHOIS privacy services interpose themselves between registrants and the public WHOIS, complicating abuse handling or legal contact. Incident responders often face opaque chains requiring registrar coordination.
- Geographic and policy fragmentation: Not all registries uniformly implement GDPR-like redactions, creating heterogeneous privacy postures across TLDs and complicating normalization and tooling maintenance.
From an engineering perspective, systems must treat registrant contact data as potentially unreliable or incomplete, integrating additional data sources such as registrar APIs, DNS observations, historical WHOIS archives, or third-party registries to approximate ownership or contact paths. Supporting compliance with query rate limits, data retention policies, and user consent frameworks is also critical.
Balancing privacy protection with operational transparency presents fundamental trade-offs. Engineers must design workflows and verification pipelines that gracefully degrade and incorporate manual review or out-of-band validation when encountering redacted or proxy-masked data.
Overall, the advent of WHOIS privacy compliance marks a paradigm shift—from WHOIS as a direct ownership truth source to one among many signals integrated within a comprehensive domain intelligence framework.
Protocol Quirks, Rate Limits, and Data Inconsistencies
Having addressed privacy-driven data limitations, it is imperative to understand additional operational issues rooted in WHOIS’s original design and current infrastructure realities that impact reliability and scalability.
Created in the early 1980s, WHOIS is a simple TCP-based query-response protocol lacking formalized schemas or structured encodings. As a result, clients connect on TCP port 43 and parse unstructured plain text responses that vary widely between registries and registrars—without required fields, consistent labels, or standard encoding. Different WHOIS servers—such as those governing .com (Verisign), .uk (Nominet), or .de (DENIC)—emit data with varying field names, languages, and formatting conventions.
Parsing this output demands bespoke, registry-specific or locale-aware logic, often relying on complex regular expressions or machine learning techniques to extract relevant data with acceptable precision. Off-the-shelf parsers suffer from false negatives or misclassifications due to the heterogeneity of responses. See IETF RFC 3912 — WHOIS Protocol Specification for official protocol details.
Operational challenges extend beyond format inconsistency:
- Rate limiting and throttling: WHOIS servers enforce strict query limits by IP or user agent to prevent abuse. Repeated excessive queries may trigger temporary blacklisting or blocking. Web-based WHOIS portals augment these with CAPTCHA or other anti-automation mechanisms to mitigate scraping.
- Service reliability variances: WHOIS servers exhibit variable uptime and response consistency; they may truncate responses, time out, or return partial data due to infrastructure or network issues.
- Data quality degradation: Registrant data often lags reality due to stale contact info or delayed updates; lifecycle timestamps may be inconsistent or erroneous due to asynchronous registry processes.
These protocol and infrastructure limitations require engineering strategies such as:
- Scheduled incremental querying with backoff and rate adherence to avoid blacklisting.
- Parsers designed with error tolerance, fallback heuristics, and anomaly detection to handle missing or malformed data.
- Local caching of WHOIS snapshots and historical data ingestion to mitigate freshness issues and reduce query volume.
- Correlation of WHOIS data with DNS and IP information to validate or enrich incomplete records.
- Integration of registrar-specific APIs or commercial data vendors for bulk access when available.
For example, a threat detection pipeline that combines adaptive parsing, continuous WHOIS snapshot archival, and concurrent DNS querying can achieve incremental gains in alert quality and operational efficiency despite WHOIS limitations.
In summary, building scalable and dependable WHOIS querying systems demands deep awareness of both legacy protocol constraints and modern operational antipatterns to design resilient, maintainable domain intelligence architectures.
Parsing and Normalizing Heterogeneous WHOIS Data
The decentralized and non-standardized nature of WHOIS data complicates parsing and integration—a challenge at the heart of delivering reliable domain intelligence services. Raw WHOIS responses emerge from thousands of globally distributed registries and registrars, each with idiosyncratic output formats, diverse field nomenclature, and often localized presentation.
Challenges in Parsing WHOIS Data
- Non-uniform field labels: The same conceptual data—the registrant’s organization, for instance—may appear under labels like “Registrant Organization,” “OrgName,” “Holder,” or localized variants.
- Optional or missing fields: Privacy redactions or registrar policies lead to missing or placeholder data, sometimes at random fields.
- Encoding and internationalization: Fields may include Unicode characters, varying between UTF-8, ASCII, or legacy encodings, requiring robust character normalization.
Techniques for Reliable Extraction
Crafting robust WHOIS parsers typically combines multiple strategies:
- Flexible regular expressions: Pattern matching with case insensitivity, whitespace tolerance, and multiple synonyms accommodates diverse field labels and separators. For instance, regexes may match both “Registrar WHOIS Server:” and “Registrar Whois:” variants.
- Template-based parsing: Maintaining a registry- or server-specific template library based on observed response structures allows higher precision and maintainability, with templates encoding expected field positions and line offsets.
- Machine learning for entity recognition: Named Entity Recognition (NER) models, trained on annotated WHOIS datasets, assist in extracting registrant names, addresses, and other entities in unstructured or novel formats, offering robust generalization.
- Hybrid systems with anomaly detection: Combining deterministic parsing rules with anomaly detection modules enables identification of unforeseen formats and supports iterative template updates, facilitating adaptation to evolving server outputs.
Normalization Into Canonical Schemas
Extracted raw data must be reconciled into unified data models to support querying, correlation, and analysis. A canonical WHOIS schema often includes:
- Structured registrant details (name, organization, email, phone).
- Registrar metadata (name, IANA ID, WHOIS server URL).
- Administrative and technical contacts with roles.
- Lifecycle dates (creation, update, expiration) with ISO 8601 formatting.
- Domain status flags reflecting operational state.
- Supplemental metadata such as nameserver IPs and DNSSEC status.
Normalization entails:
- Field unification: Mapping synonyms and variants to standard field names.
- Data cleansing: Removing extraneous whitespace, enforcing UTF-8 encoding, and unifying date formats.
- Conflict resolution: Prioritizing authoritative or recent data when inconsistent inputs occur across multiple WHOIS sources.
- Structured output: JSON or protobuf representations enable seamless interoperability with other infrastructure components.
Implementation Insights
A global domain monitoring service processed over 250 distinct WHOIS formats using a hybrid approach, combining registry-specific parsers and deep learning NER models. This strategy delivered over 90% extraction accuracy and sped parsing by 30%, enabling normalized JSON outputs integrated with DNS resolution services for improved detection of anomalous domain registrations.
Continuous protocol evolution, such as the adoption of RDAP, necessitates flexible parsing architectures with ongoing retraining and modular configuration to sustain accuracy and adaptability.
Managing Rate Limits, Caching, and Data Freshness
With parsing challenges addressed, a crucial operational aspect remains: managing access controls and ensuring data freshness amid WHOIS query rate restrictions and inconsistent update cadences.
WHOIS servers enforce policy-driven rate limits geared toward preventing abuse and ensuring equitable resource use. Limits typically restrict queries to ranges like 5–10 requests per minute per IP and impose temporary bans for overuse, sometimes including CAPTCHA or login challenges on web portals.
System Strategies for Rate Compliance
- Server policy awareness: Parsing documented quotas or HTTP headers indicating remaining limits to adapt query rates dynamically.
- Backoff and retry with jitter: Exponential backoff augmented by randomized delays minimizes synchronized retries and reduces server load spikes.
- Distributed query dispatch: Partitioning queries across multiple geographically dispersed IPs and orchestrated containerized agents achieves aggregate throughput while respecting per-IP constraints.
- Tiered query approaches: Authoritative WHOIS servers are queried only as needed for high-fidelity or freshness-critical lookups; cached or secondary data sources serve routine requests, balancing load and responsiveness.
Caching Designs
Caches mitigate rate limits and improve latency:
- Metadata-aware caches: Store raw WHOIS responses with retrieval timestamps and source indicators to enable informed eviction and validity checks.
- Configurable TTLs: Given that domain registration data changes infrequently, TTLs between 24 and 48 hours balance freshness with query reduction. Active incidents or suspicious domains warrant shorter TTLs.
- Delta updates: Leveraging registrar APIs exposing incremental changes reduces full-query frequency, enhancing efficiency.
Addressing Freshness Challenges
WHOIS data propagation can lag due to registry update cycles, asynchronous processing, or caching inconsistencies. Systems thus:
- Monitor query success rates and cache hit ratios to detect potential staleness or server blacklisting early.
- Correlate changes with DNS monitoring and IP address shifts to infer domain activity when WHOIS data is delayed.
- Employ event-driven cache invalidation triggered by external signals such as domain auction listings or registrar notifications to prioritize fresh queries.
Case Study: Scaling Under Quotas
A cybersecurity platform scanning millions of domains daily initially encountered WHOIS query throttling and stale data complaints. Their solution architecture incorporated:
- Multiregion query agents distributing load across 50 cloud regions.
- Layered caching with 24-hour TTL and event-triggered cache refreshes on suspicious domains.
- ML-based anomaly detection flagging malformed or incomplete WHOIS data for immediate re-query.
- Registered API integration for bulk access where supported.
Resulting in an 80% reduction in unnecessary queries, a 40% freshness improvement, and multi-million-dollar operational savings through avoided premium data vendor dependency.
Strong rate-limit management and caching harmonized with adaptable parsing empower scalable, reliable, and timely WHOIS integration, enabling complementary use with DNS and IP data for comprehensive domain intelligence systems. See CNCF Cache Invalidation Best Practices for further insights on distributed caching strategies.
Conclusion
From an engineering lens, WHOIS emerges as a decentralized, protocol-driven system central to domain ownership transparency but challenged by heterogeneous data formats, privacy-driven redactions, and stringent operational constraints such as rate limits and inconsistent server reliability. The critical delineation between registrant and registrar data, coupled with its interplay alongside DNS and IP query mechanisms, underscores WHOIS’s unique role in domain lifecycle and security management workflows.
Successfully building and operating WHOIS integration systems demands navigating regulatory-driven data opacity, designing robust, adaptive parsing frameworks, and architecting resilient query infrastructure with intelligent caching and rate-limit compliance. In parallel, evolving protocols like RDAP promise more structured, machine-readable data outputs, though entrenchment of legacy WHOIS servers guarantees ongoing complexity.
Looking forward, as domain registration ecosystems grow in scale and complexity and privacy concerns intensify, the architectural challenge is to devise WHOIS-centric solutions that remain maintainable, transparent, and verifiable. The central design question engineers must confront is how to balance the competing demands of data fidelity, privacy compliance, scalability, and operational resilience—ensuring domain ownership verification tools remain trustworthy, performant, and extensible in the face of continuous internet infrastructure evolution.