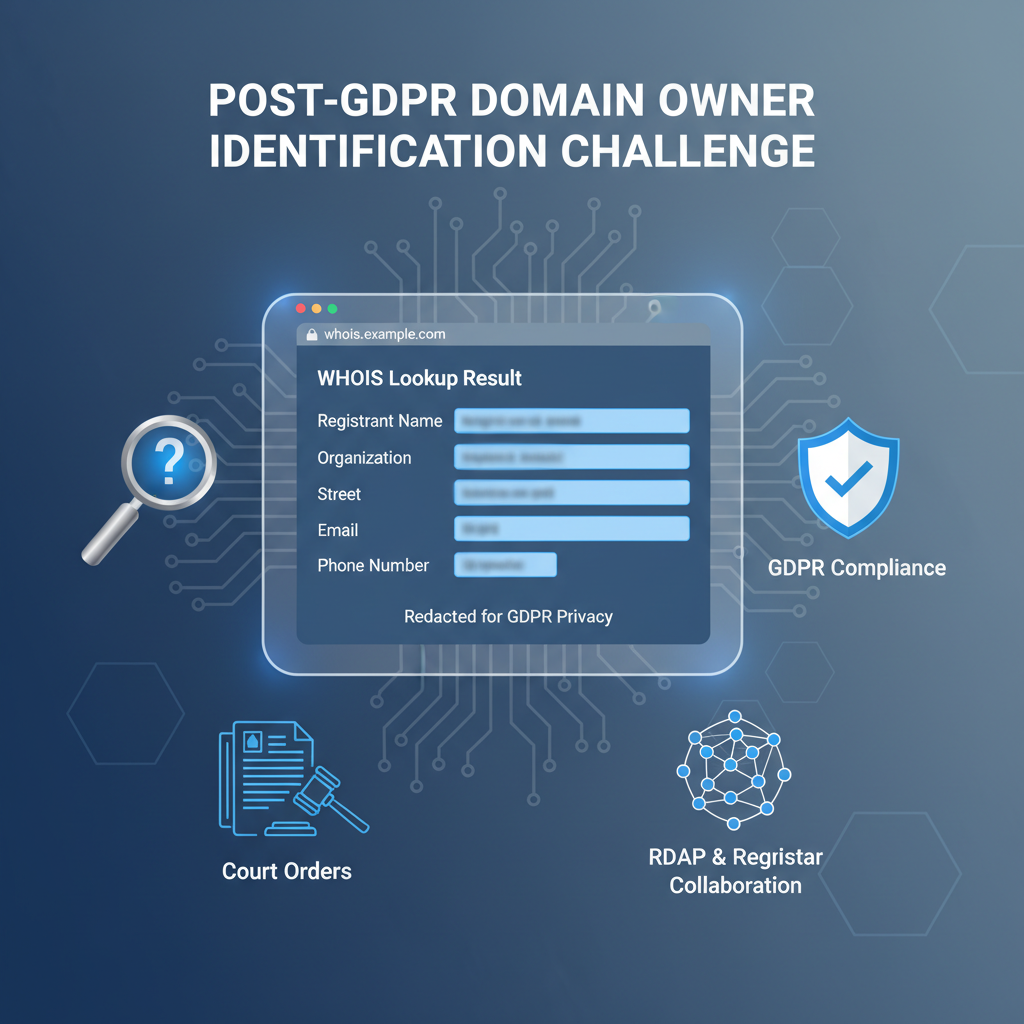
Can You Identify Domain Owners After GDPR? Legal Methods Explained
Introduction Since the enforcement of the General Data Protection Regulation (GDPR), the traditional WHOIS protocol no longer provides...

How GDPR Affects Domain Ownership Lookup for Businesses
Introduction Public WHOIS services no longer provide unfettered access to domain ownership data due to GDPR’s stringent privacy...
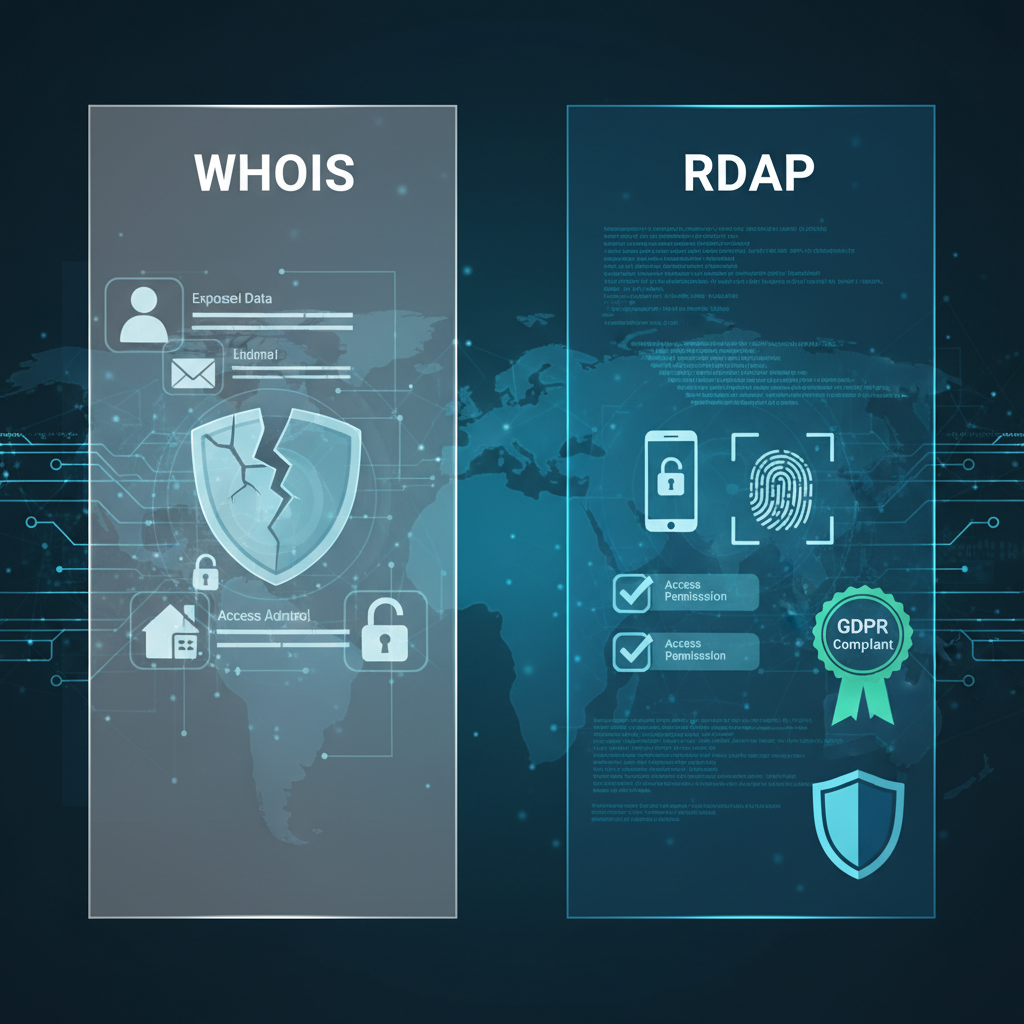
WHOIS vs RDAP: Privacy, Access Levels, and Compliance Compared
Introduction WHOIS’s original plaintext protocol exposes domain registrant data indiscriminately, lacking any built-in authentication or granular access controls....

WHOIS Privacy Protection: How It Works and When You Need It
Introduction WHOIS privacy protection addresses a fundamental tension inherent in domain registries: the public exposure of registrant contact...

Is WHOIS Data Still Public in 2025?
Introduction WHOIS data has traditionally been the cornerstone for discovering domain registration details. However, by 2025, its public...

Why WHOIS Data Is Redacted (And What You Can Still Access)
Introduction WHOIS data redacted by registrars and registries presents fundamental challenges for engineers developing domain management, security, and...

WHOIS and GDPR Explained: What Changed and Why It Matters
Introduction WHOIS queries have historically served as a straightforward mechanism to retrieve domain registration data, exposing detailed owner...
Building an Automated Domain Abuse Detection System
Introduction Detecting domain abuse at scale presents a foundational challenge in extracting meaningful signals amidst perpetual domain state...
Registrar Patterns That Signal Suspicious Domain Activity
Introduction Suspicious domain activity seldom reveals itself through overt alerts; instead, it often conceals behind patterns embedded in...

Detecting Domain Abuse with WHOIS + DNS Intelligence
Introduction Detecting domain abuse remains a persistent challenge because neither WHOIS registration data nor DNS signals alone provide...

How Law Enforcement Uses WHOIS Data in Cybercrime Cases
Introduction WHOIS data often serves as the initial forensic metadata layer investigators leverage when dissecting the domain-level infrastructure...

WHOIS History: A Powerful Tool for Fraud Investigations
Introduction Static WHOIS queries capture domain registration details only at a single point—offering a narrow, transient view insufficient...

Brand Protection Using WHOIS and Domain Monitoring APIs
Introduction The threat landscape surrounding brand protection domains has evolved from static, occasionally monitored assets into a fast-moving...
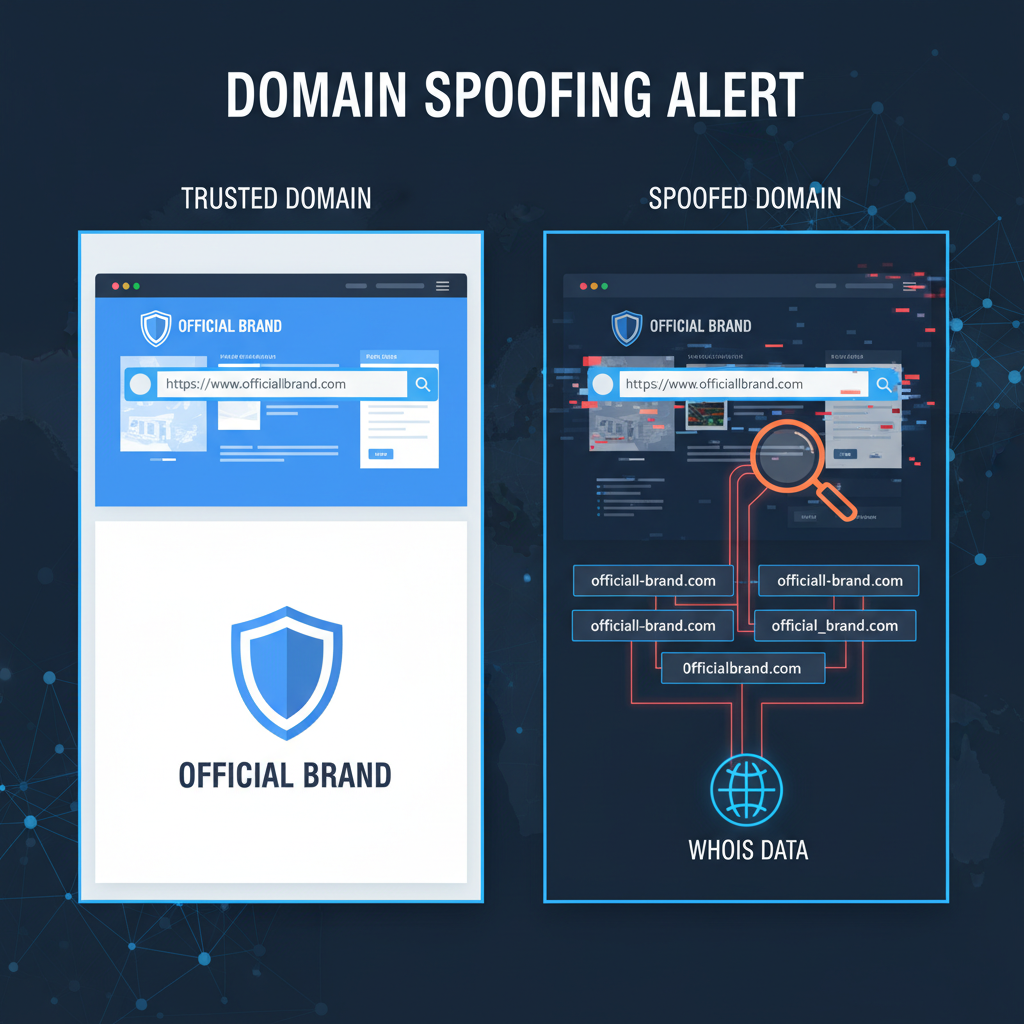
Domain Spoofing Explained: How Attackers Imitate Trusted Brands
Introduction Domain spoofing remains a persistent and insidious blind spot within contemporary security architectures, as attackers exploit fundamental...
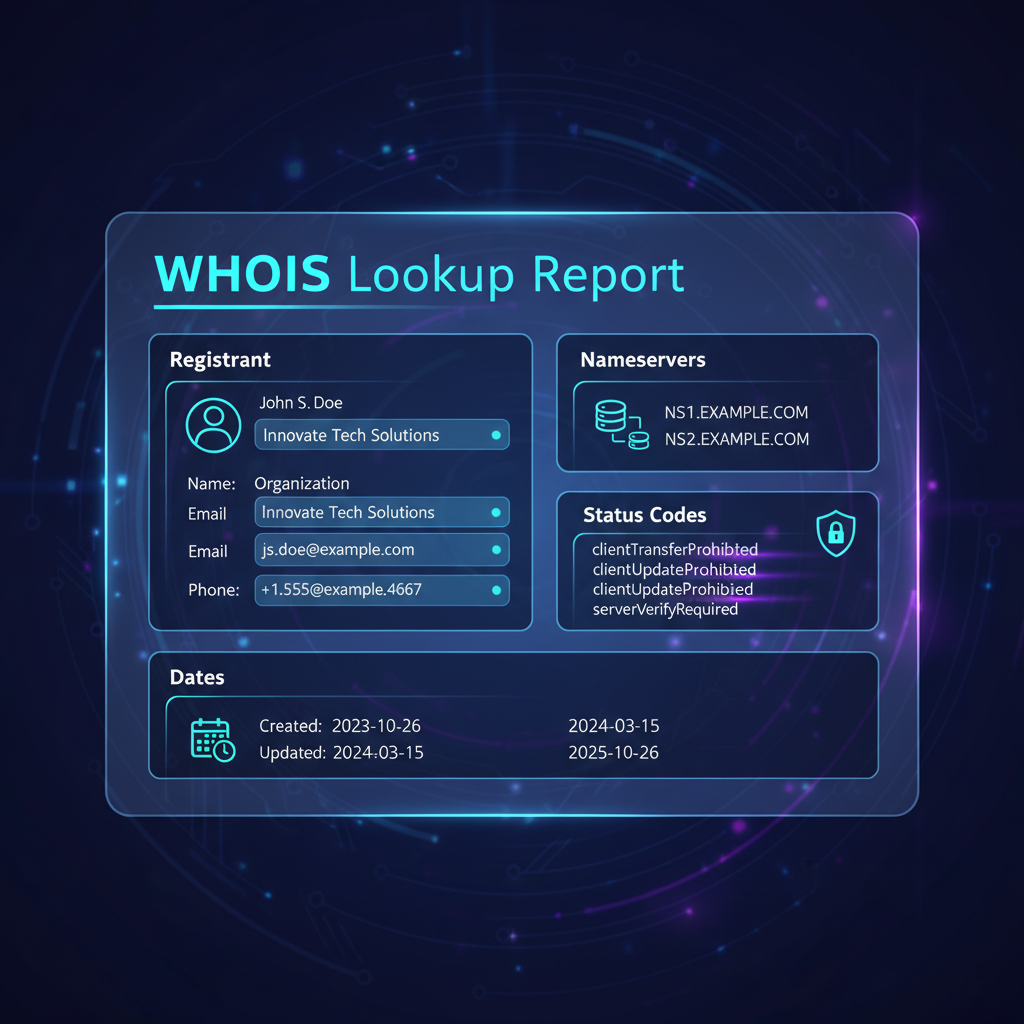
How Cybercriminals Abuse Newly Registered Domains
Key Takeaways Newly registered domains represent a critical vector exploited by cybercriminals due to their inherent lack of...

Using WHOIS to Identify Malicious Domains in Real Time
Introduction Malicious domain registration is rarely random; it leaves discernible footprints in WHOIS metadata that, when captured and...

How WHOIS Data Helps Detect Phishing Domains
Introduction Phishing attacks critically rely on the rapid creation and disposal of malicious domains that vanish before defensive...
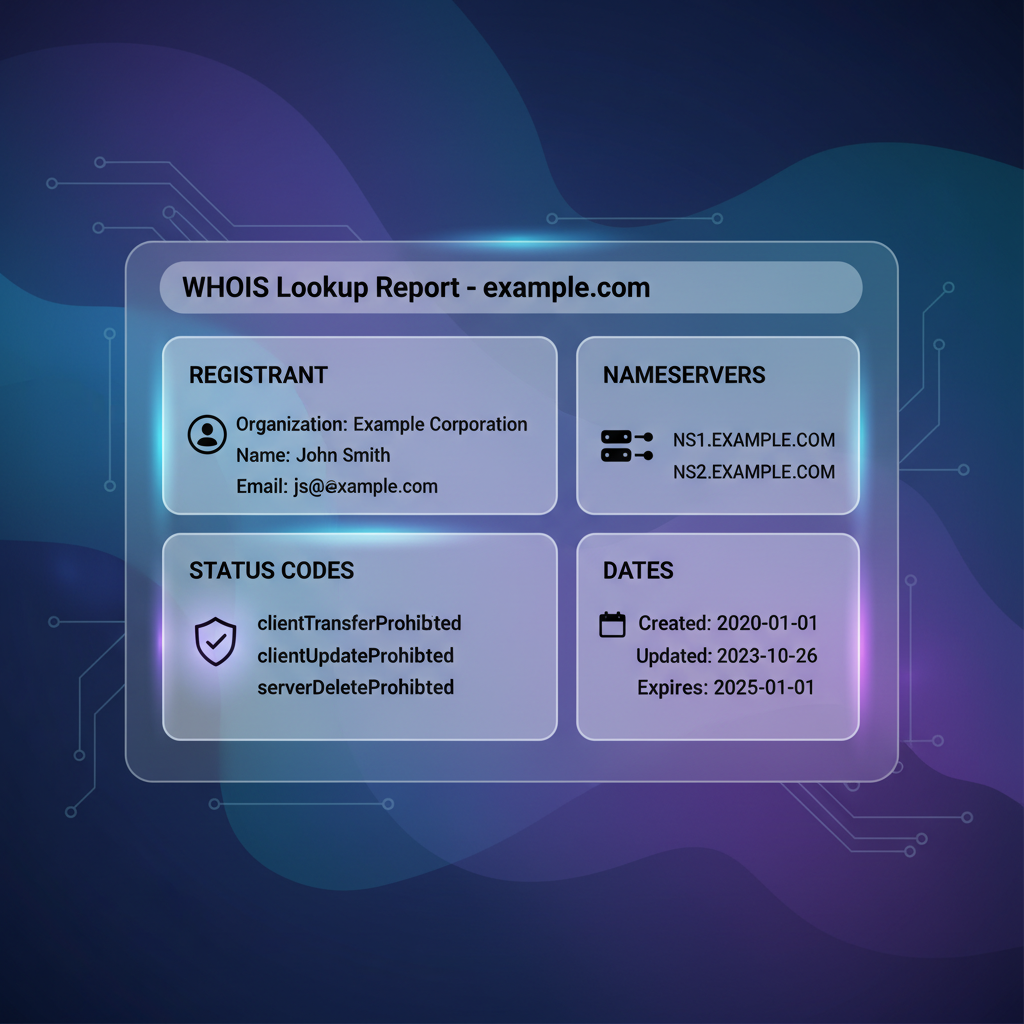
Is WHOIS Data Public? Privacy, GDPR, and Redacted Records Explained
Key Takeaways WHOIS is a foundational protocol for querying domain registration metadata, critical to domain lifecycle management, infrastructure...
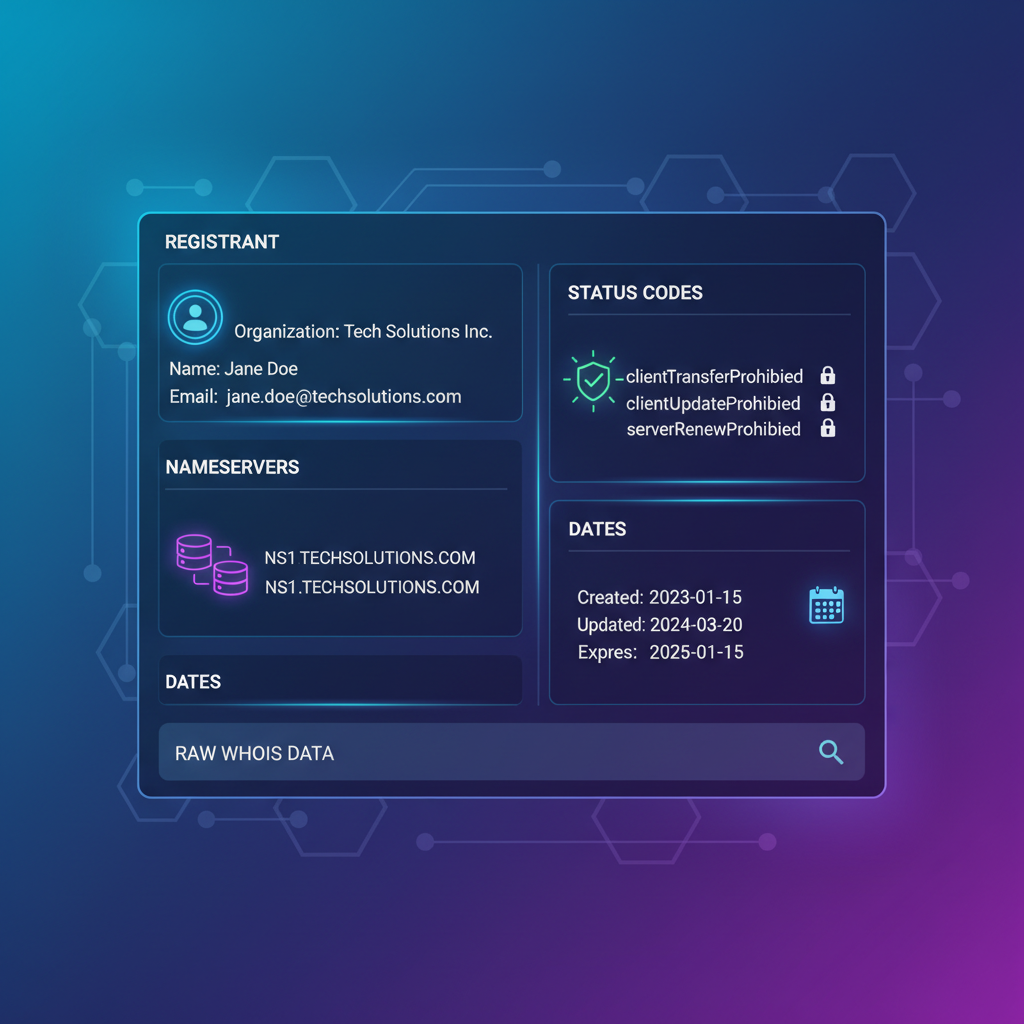
WHOIS vs RDAP: What’s the Difference and Why It Matters
Key Takeaways A detailed understanding of these dimensions equips engineers to implement future-proof domain data services conforming to...
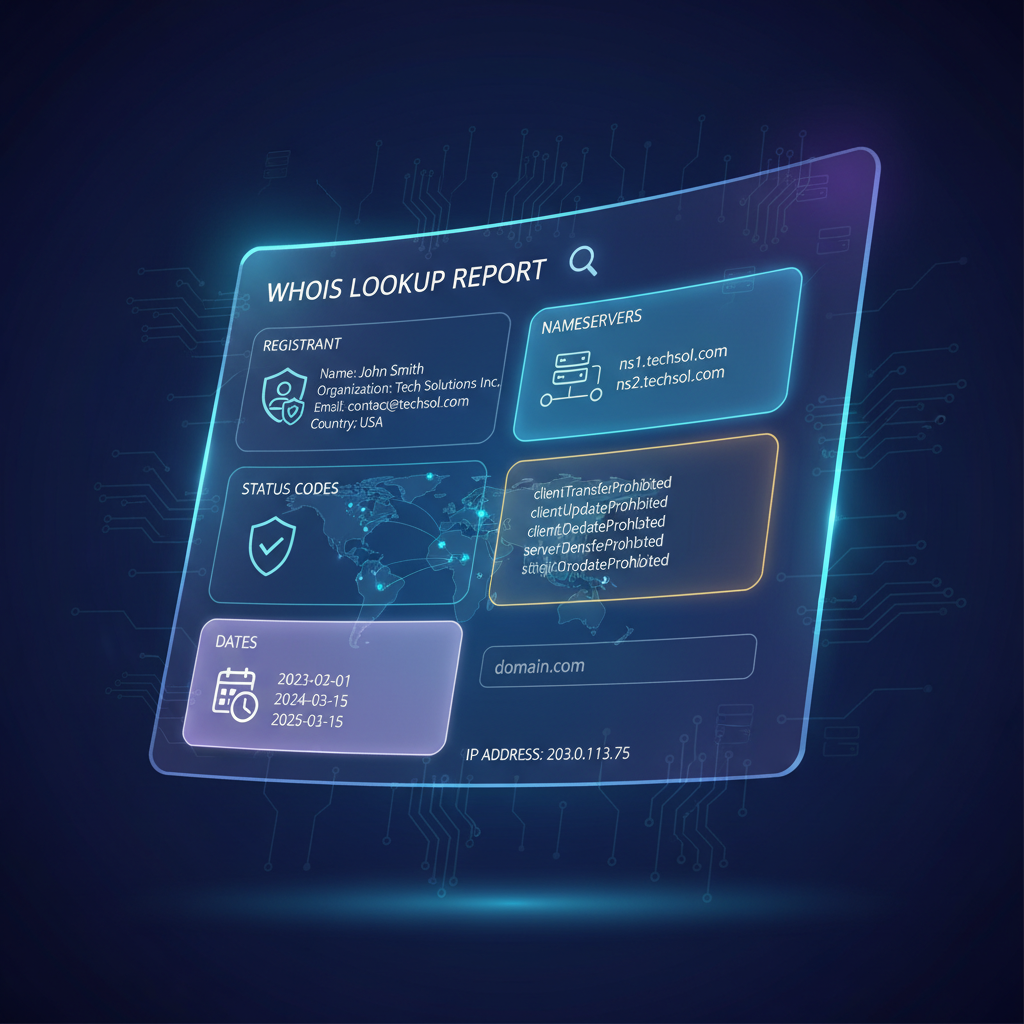
What Information Does a WHOIS Lookup Show? (Field-by-Field Breakdown)
Key Takeaways By dissecting WHOIS lookup fields with engineering rigor, teams can architect precise domain management tooling that...