Key Takeaways
- A WHOIS lookup is an indispensable tool for extracting domain registration metadata from decentralized data repositories, critical for infrastructure management, security analytics, and continuous domain lifecycle monitoring.
- Deep comprehension of WHOIS fields—from registrant and contact details to status codes and nameserver configurations—empowers engineers to automate domain validation, establish trust boundaries, and diagnose DNS-related failures with precision.
- Accurate interpretation requires understanding field interdependencies and evolving semantics due to growing adoption of RDAP, which impacts data consistency, privacy handling, and parsing logic across integration pipelines.
- Interpret registrant and contact fields for robust ownership verification: Registrant, administrative, and technical contacts identify domain controllers and accountable parties; misattribution due to obfuscation or redaction risks delayed incident response and legal ambiguity.
- Analyze nameserver data to map DNS delegation and infrastructure topology: Nameserver entries indicate authoritative DNS points critical to resolution paths, supporting redundancy planning, failover strategies, and DNSSEC validation.
- Leverage domain status codes to automate lifecycle and compliance operations: Values like
clientTransferProhibited,pendingDelete, andredemptionPeriodsignal contractual constraints and operational states that safeguard domains from unintended transfers or expiration races. - Use key date fields for temporal validity, renewal triggers, and forensics: Creation, update, and expiration timestamps serve as authoritative anchors for archival workflows, renewal automation, and security incident timelines, while informing caching and IP reassignment strategies.
- Recognize WHOIS protocol limitations that drive RDAP adoption: WHOIS responses are unstructured with variable field formats; RDAP’s JSON schema offers richer, more reliable parsing but requires hybrid tooling during migration phases to preserve backward compatibility.
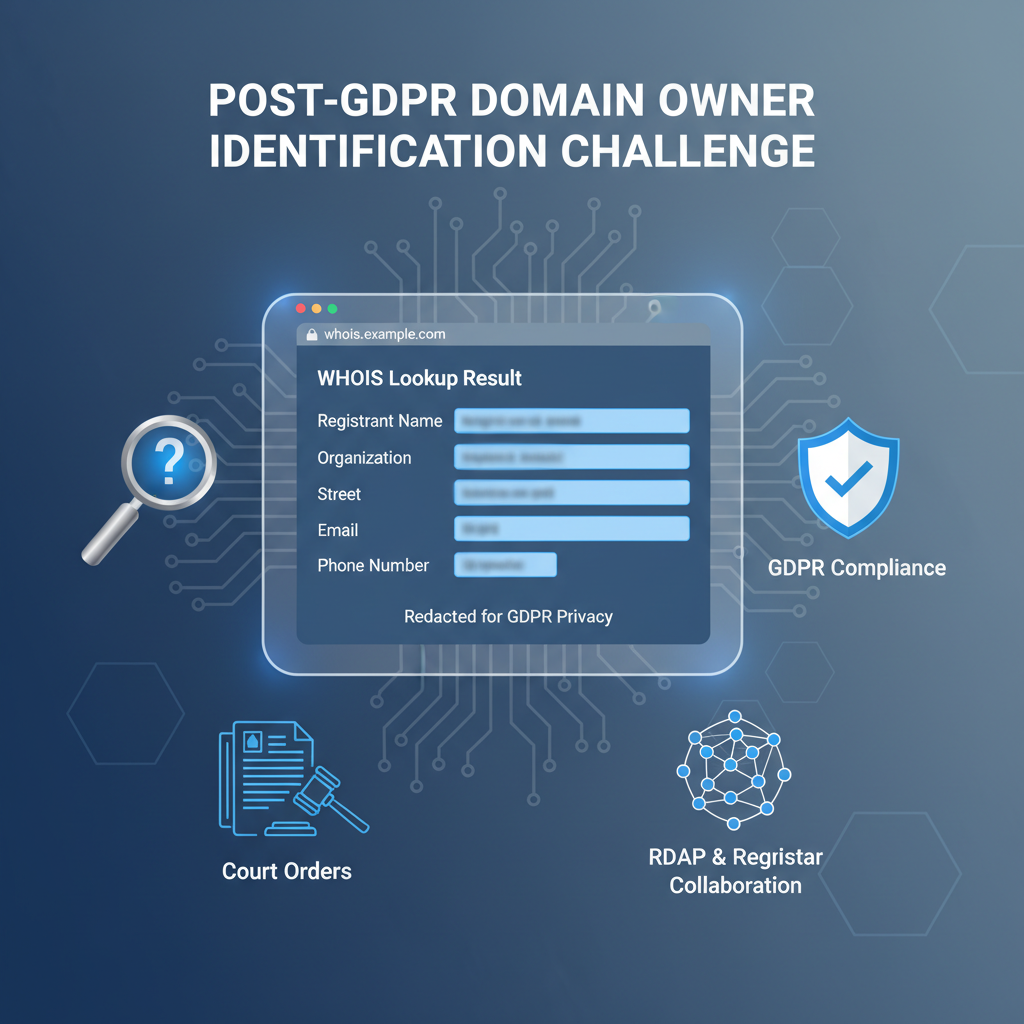
- Account for privacy and data redaction impacts on completeness and trustworthiness: GDPR and domain privacy proxies anonymize or suppress WHOIS fields, necessitating alternate verification via heuristic correlation, registrar APIs, or DNS-based proofs in security and investment analyses.
- Incorporate IP lookup and reverse DNS for enriched contextual analysis: Combining ARIN IP lookup, reverse IP queries, and WHOIS data reveals hosting infrastructure, abusive endpoints, and network architectures vital for diagnostics and threat investigation.
- Track DNS record history and nameserver changes to detect configuration drifts: Historical DNS data complements WHOIS by exposing domain hijacking attempts or operational misalignments impacting security posture and business continuity.
- Design around WHOIS bulk query constraints and rate limiting: Scalability requires respecting registrar query throttling, deploying caching layers, and applying batching strategies to maintain throughput without service disruption.
- Integrate WHOIS-derived domain security insights into threat intelligence pipelines: Ownership metadata and status data enhance detection of malicious domains, supporting automated blocking, reputation scoring, and forensic investigations.
By dissecting WHOIS lookup fields with engineering rigor, teams can architect precise domain management tooling that reconciles real-world inconsistencies with evolving protocols, delivering resilient system integrations. The following sections elaborate each field’s semantics with practical examples and code-oriented guidance for operationalizing these insights.
Introduction
Domain registration metadata surfaced through WHOIS lookups transcends being a mere contact dump; it forms a foundational input for automation, security enforcement, and DNS fault analysis. However, its structure suffers from fragmentation, variable field semantics, and subtle interdependencies among registrant details, status codes, and delegation data that challenge automation pipelines and risk ownership misinterpretation.
This complexity prompts a crucial inquiry for engineers orchestrating infrastructure or security workflows: what precisely does each WHOIS field signify, and how can systems reliably extract actionable intelligence amidst protocol inconsistencies, privacy restrictions, and the gradual shift towards RDAP? Mastering these datasets unlocks tooling capabilities spanning domain validation, DNS delegation audits, compliance automation, and threat intelligence enrichment.
We proceed by methodically analyzing the WHOIS lookup response, exploring each field’s function, operational caveats, and real-world engineering use cases. This understanding improves domain accuracy, enhances alerting precision, and reinforces resilience against common failure modes in domain-dependent systems.
Fundamentals of WHOIS Lookup and Its Purpose
WHOIS constitutes a foundational query-response protocol designed to expose domain registration metadata vital to network operators, registries, registrars, and security teams. Originating in the early 1980s under DARPA, WHOIS has become embedded in Internet governance as a decentralized service that retrieves registration details about domain names, IP blocks, and ASNs. Its layered architecture delegates authority through multiple WHOIS servers—operated by registries and registrars—accessible via TCP port 43 using simple text-based protocols.
A WHOIS query submits a domain or network identifier to an authoritative WHOIS server, which returns human-readable registration metadata. This distributed system hinges on root zone delegation to TLD registries, which either respond with minimal referral data (thin WHOIS) or maintain complete metadata databases (thick WHOIS). This distinction impacts the availability and richness of the returned data:
- Thin WHOIS: Provides limited registry-level information—typically registrar identity and referral pointers—requiring subsequent queries to the registrar’s WHOIS server for full registrant data. Seen in
.com,.netin earlier implementations. - Thick WHOIS: Contains comprehensive registration records including registrant, administrative, technical contacts centrally maintained by the registry or registrar, enabling single-step retrievals.
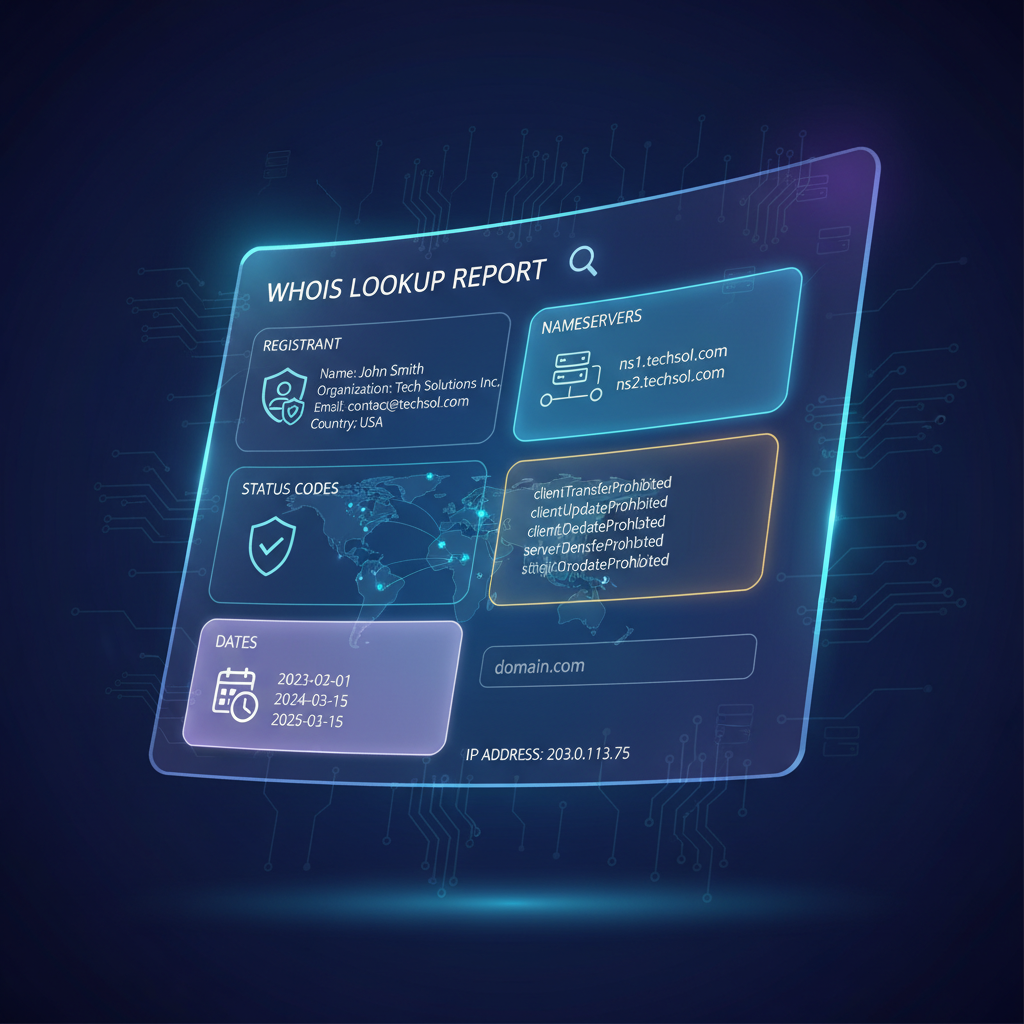
The exposed metadata includes several critical categories underpinning domain governance and infrastructure oversight:
- Registrant Information: Legal entity or individual that owns the domain, including name, organizational affiliation, postal and email addresses, and phone numbers. Establishes accountability and legal responsibility.
- Registrar Details: The accredited entity managing domain registration sponsorship, including registrar name, IANA ID, and contacts essential for dispute resolution and coordination.
- Administrative and Technical Contacts: Points of contact specifying roles responsible for domain administration and technical support, critical for incident handling and configuration management.
- Nameservers: Authoritative DNS servers delegated for the domain, pivotal in query resolution and DNS infrastructure integrity.
- Registration Status Codes: EPP-based status flags such as
clientTransferProhibitedorpendingDeleteindicate current operational states, controlling lifecycle events and enabling enforcement of domain policies. - Important Dates: Lifecycle timestamps including creation, expiration, and last modification dates guide renewal processes, ownership verification, and auditing workflows.
Together, these fields empower stakeholders—including security teams, system operators, and registrars—to inspect domain ownership, confirm authorization, and monitor DNS health. However, variations in registry/registrar implementations and local policy restrictions induce inconsistencies in field naming, completeness, and formatting.
Addressing WHOIS limitations, the Industry introduced the Registration Data Access Protocol (RDAP) (RFC 7480), a RESTful HTTP API that returns well-formed JSON data. RDAP enhances machine readability, enforces access control, supports privacy filtering, and extends metadata in a standardized schema. Adoption remains uneven, but RDAP fundamentally improves the reliability of domain registration data consumption.
Consider a typical WHOIS response snippet for example.com illustrating key fields:
Registrant Name: John Doe Registrant Organization: Example Corp Registrant Email: [email protected] Registrar: Example Registrar, Inc. Name Server: ns1.example.com Domain Status: clientTransferProhibited Creation Date: 2005-03-15T12:00:00Z Expiration Date: 2025-03-15T12:00:00Z
Each field maps directly to ownership, operational delegation, lifecycle state, or temporal validity, holding precise semantic significance.
WHOIS offers a static snapshot, lacking time-series DNS data. Complementing WHOIS, DNS record history lookup services archive antecedent DNS configurations (A, MX, TXT records), essential for forensic timelines and security incident responses. For example, APIs like SecurityTrails integrate WHOIS with DNS historical data to craft comprehensive domain change narratives.
Challenges and Limitations in WHOIS Data Acquisition
Despite its centrality, extracting authentic, comprehensive, and machine-usable WHOIS data encounters numerous technical and policy-driven impediments.
Data Format Variability stands as the foremost hurdle. While RFCs articulate general expectations, there is no strict mandatory standard enforcing uniform field names, ordering, or syntax across registrars. For instance, registrant organization fields can appear as Registrant Organization:, OrgName:, or Organization: depending on provider. Such heterogeneity demands complex heuristics, enterprise-grade parsers customized per registrar, or continuous maintenance to handle output variations, complicating automation at scale.
Incomplete or Redacted Fields result increasingly from privacy regulations (e.g., GDPR) and commercial privacy protection services. WHOIS privacy proxies replace original registrant info with anonymized contact points, masking real owner details. Though privacy-preserving, this obfuscation curtails identity verification, complicates abuse investigations, intellectual property enforcement, and security incident tracing. Analysts frequently confront dead ends when registrant data refers only to proxy services, impeding rapid incident response.
Rate Limiting and Access Restrictions imposed by registries and registrars curb query rates to prevent abuse and server overload. Techniques include throttling connections per IP, CAPTCHAs, and API key gating, impeding high-volume WHOIS lookup use cases such as bulk portfolio auditing, expansive security scans, or longitudinal research. Workarounds include commercial data agreements, distributed query architectures, and cached third-party databases, temporarily alleviating but not eliminating operational complexity.
Evolving Protocols and Privacy Models introduce additional complexity. RDAP mandates authentication and authorization layers tailored to regulatory privacy compliance, restricting exposures based on requester credentials. While improving compliance, this model complicates previously open WHOIS data access patterns, requiring adaptive tooling that gracefully handles partial or filtered datasets. Simultaneously, RDAP JSON schemas evolve, and inconsistencies remain during hybrid WHOIS/RDAP deployments.
Data Currency and Synchronization Delays adversely affect reliability. WHOIS databases reflect registration changes asynchronously; delays from registrar processes or database syncs, ranging from minutes to days, induce stale records. Consequently, operations that depend on real-time domain status or ownership data risk misinformed decisions or automation failures.
Different operational roles experience these challenges distinctively. Security analysts face blocks when contacting anonymized registrants, risking incomplete threat attribution. CI/CD pipelines integrating WHOIS data encounter fragile parsing brittle to format shifts, causing pipeline failures. Domain investors or brand managers suffer delayed or inaccurate ownership visibility, potentially triggering valuation errors or missed acquisition windows.
Common failure modes include discrepancies between WHOIS-registered nameservers and live DNS zones, ambiguous or missing domain status codes disrupting lifecycle automation, and inconsistent delineation between administrative and technical contacts complicating support workflows.
Importantly, WHOIS data represent registry or registrar authoritative records but do not constitute irrefutable proof of domain ownership; legal and contractual factors influence ultimate ownership claims beyond administrative datasets.
WHOIS remains a predominantly open and free service but limited in scale by rate constraints; RDAP introduces potential tiered or paid access models rooted in regulatory compliance objectives, altering universal data accessibility.
Tracking historical WHOIS changes—critical for ownership transfer detection, domain hijacking signals, or aftermarket activity—involves persistent monitoring coupled with anomaly detection tailored to registrar-specific quirks and synchronization delays. Enhanced situational awareness requires integrating WHOIS updates with DNS history and passive DNS datasets. Domain intelligence providers such as DomainTools offer methodologies and tooling for automated WHOIS surveillance.
Navigating these dimensions elucidates why WHOIS lookup remains indispensable yet operationally complex for security, domain management, and due diligence applications. Recognizing these subtleties enables development of robust, fault-tolerant tooling and informed metadata interpretation. The advent of RDAP underscores an evolution toward structured, privacy-conscious registration data ecosystems.
Comprehensive Field-by-Field Breakdown of WHOIS Lookup Data
WHOIS lookup outputs provide a structured snapshot of domain registration metadata vital for ownership validation, operational control, and DNS troubleshooting. Engineers, analysts, and investors benefit from understanding each field’s purpose, standard semantics, and integration points with networking diagnostics.
Registrant and Administrative Contact Fields Explained
Registrant and contact fields in WHOIS denote primary domain ownership and responsibility. Core fields often include the registrant’s name, organization, email, phone, and postal address, serving as provenance markers. In practice, these may be obfuscated by privacy services or redacted under GDPR and regional laws, leading to reduced reliability.
Registrant emails frequently resolve to proxy mailboxes, complicating incident response or ownership verification workflows. Engineering teams must treat these contacts cautiously, often supplementing with external sources or out-of-band verification mechanisms.
WHOIS differentiates contact roles operationally:
- Registrant Contact: The legal domain owner, with ultimate rights.
- Administrative Contact: Manages business-related oversight including transfers and compliance.
- Technical Contact: Handles DNS configuration, technical support, and network troubleshooting.
Operational distinction is critical; technical teams often engage the technical contact for DNS issues, whereas legal or business escalations route to administrative or registrant contacts.
For comparison, MAC address OUI lookups provide hardware vendor attribution with deterministic identifiers, contrasting the fluid, oft-redacted nature of WHOIS contact data. This highlights why WHOIS fields alone cannot serve as definitive asset identifiers for network forensic purposes.
Misinterpretation risks delays when anonymized emails are treated as unreachable or when contact roles blur, misaligning escalation. Thus, WHOIS contact data remains an essential yet inherently incomplete resource requiring layered validation and registrar-specific understanding.
Domain Status Codes and Their Operational Significance
WHOIS status codes encode domain lifecycle states that directly affect registration functionality, transferability, DNS availability, and renewal. These EPP-derived flags represent administrative constraints and operational states critical for automation and troubleshooting.
Key common codes include:
- ok: Domain is fully operational; no transfer or update restrictions applied.
- clientHold: Registrar-enforced suspension often triggered by policy or billing issues; DNS resolution is disabled.
- serverHold: Registry-level hold suspending DNS, often due to legal or contractual enforcement.
- pendingDelete: Domain entered deletion grace period post-expiration, pending release; DNS services stopped.
- redemptionPeriod: Post-expiration renewal window where the owner can restore the domain at incurred fees.
Status codes map directly to domain lifecycle phases—active, suspended, or retired—shaping automation behavior. For example, domains under clientHold cause resolution failures even if DNS entries superficially appear correct, a subtlety often missed in pure DNS diagnostics.
Because tools like TCP-based connection tests may fail due to clientHold, understanding WHOIS status flags is essential to distinguish administrative suspensions from network faults. While hardware-centric tools (e.g., ping or serial number lookups) diagnose connectivity at device layers, WHOIS status flags provide administrative context vital for holistic root cause analysis.
ICANN’s Registry Registrar Agreement (RRA) mandates standard status code usage; engineers implementing domain state-aware systems should reference formal specifications to avoid misinterpretation.
Status codes enable proactive lifecycle automation: services can block transfers for clientTransferProhibited domains, flag impending expirations at pendingDelete, and prevent erroneous renewal actions, thereby stabilizing domain management workflows.
Important Dates in WHOIS Records and Their Use Cases
WHOIS timestamps—primarily creation date, expiration date, and last updated date—constitute temporal anchors for operational decisions.
- Creation Date: Marks domain inception, often used to assess domain age in trust and reputation models. Older domains typically infer higher legitimacy.
- Expiration Date: Renewal deadline; monitoring prevents inadvertent lapses triggering service disruption or exposure to hijacking.
- Last Updated Date: Indicates recent metadata modifications, aiding forensic timelines and change tracking.
Limitations arise from potential delays in updating WHOIS records, batching of data synchronization by registrars, and inconsistent timestamp formats, challenging real-time automation dependent on freshness.
Security teams use expiration monitoring to anticipate exploit attempts related to expiring domains—commonly targeted for takeover or phishing. Investors leverage age data for valuation heuristics, valuing domains with established credibility.
Complementing these dates, live network diagnostics like command-line IP lookups contextualize domain resolving infrastructure changes, correlating WHOIS temporal data with DNS/IP state evolutions.
Integrating WHOIS date monitoring with DNS record history cross-validations enhances accuracy, compensating for WHOIS data staleness and ensuring robust lifecycle tracking.
Nameserver and DNS Delegation Entries in WHOIS Data
Nameserver (NS) listings in WHOIS specify authoritative DNS servers designated for the domain, anchoring DNS delegation infrastructure. These entries serve as critical references during troubleshooting and infrastructure audits.
A prevalent operational challenge involves mismatches between WHOIS-listed nameservers and those observed in live DNS zone files. Such discrepancies stem from registry update cycles, propagation delays, or erroneous registrar configurations and can impair zone validation, DNSSEC, and resolution reliability.
For instance, stale WHOIS NS data suggesting obsolete delegation can mislead responders investigating service outages, causing wasted effort on non-authoritative servers.
Effective troubleshooting necessitates cross-validation with real-time DNS queries utilizing tools such as dig, nslookup, and host on Linux—providing authoritative NS lists and IP addresses reflecting current delegation.
The difference between WHOIS static registration data and dynamic DNS data requires workflows to treat WHOIS NS fields as heuristics or starting points, not authoritative sources for live DNS state.
- Comparing WHOIS NS entries against active DNS responses to identify misalignments.
- Monitoring for update delays and planning for propagation latency in incident analyses.
- Leveraging DNSSEC validation failures potentially caused by name server mismatches.
Understanding WHOIS NS data’s heuristic nature improves incident responsiveness and informs zone management best practices.
Interpreting and Leveraging WHOIS Lookup Information
Mapping WHOIS Data to Domain Ownership and Validation
At the heart of ownership validation lies WHOIS’s structured contact data, domain statuses, and assigned nameservers. Precise interpretation supports domain management APIs, CI/CD pipelines, and enterprise asset inventories.
Registrant fields, as maintained by registrars under ICANN or regional oversight, include structured contact identifiers—name, organization, postal/email addresses, phone numbers. Yet privacy shielding or incomplete records complicate automation.
Ownership verification systems rely on correlating registrant emails, names, and contacts during control checks. When proxy services mask these fields, fallback mechanisms engage, such as:
- Querying registrar-specific authenticated APIs for extended data.
- Employing DNS-based verification like TXT record proofs to demonstrate control.
- Integrating external databases or contact reconciliation heuristics.
Domain status codes provide operational constraints vital for validation logic. For example, domains flagged as clientHold or clientTransferProhibited indicate suspended or locked states, precluding immediate administrative changes. Systems must incorporate status-aware logic to honor these restrictions and avoid false alarms or disruptive actions.
Nameserver records underpin technical assertion of domain control. Verifying WHOIS-reported NS fields against live DNS queries serves as a consistency checkpoint, identifying spoofed or misconfigured delegations that could signify compromise.
A practical scenario includes security teams cross-validating WHOIS domain data alongside IP ownership via ARIN IP lookup, attributing hosting infrastructure definitively. ARIN offers authoritative IP range assignments instrumental in differentiating legitimate hosting from suspicious infrastructure masked behind opaque WHOIS records.
Degraded or stale registrant data heightens domain hijacking risk, emphasizing vigilant WHOIS monitoring alongside complementary DNS and IP intelligence to preempt unauthorized control changes.
Thus, ownership validation frameworks for distributed systems or CI/CD deployments should combine multipronged heuristics reconciling WHOIS data, registrar APIs, DNS proofs, and IP registry queries, reducing reliance on any single potentially stale or redacted source.
Using WHOIS Data for Security Enforcement and Threat Intelligence
WHOIS metadata forms a pillar of domain-centric threat intelligence, enabling attribution, abuse investigation, and reputation assessment.
Incident responders leverage WHOIS to extract registrant identities, contact patterns, and registration metadata associated with suspicious domains identified via IOCs. Temporal data such as creation and expiration dates distinguish between newly registered domains frequent in phishing campaigns and long-standing domains indicative of trusted assets.
Security orchestration engines utilize these WHOIS facets to dynamically prioritize and triage domain investigations, reducing false positives.
Augmentation occurs through IP reputation and geolocation tools, e.g., iPhone IP address lookup and threat intelligence feeds, merging WHOIS registrations with resolved IP subnet abuse reports. Such fusion enables rapid classification of malicious infrastructure despite registrant anonymity.
Nonetheless, WHOIS data challenges persist: update delays impair real-time effectiveness; adversaries exploit privacy proxies and synthetic registrations to evade detection; and data poisoning risks introduce misleading data to confound investigations.
SOCs interpret WHOIS domain statuses to gauge legitimacy and lifecycle risk; domains in pendingDelete may be deprioritized unless exhibiting rapid churn patterns linked to automated domain generation algorithms (DGAs).
Large-scale detection pipelines apply reputational scoring based on WHOIS-derived age and registrant reputation metrics, but must compensate for data gaps via fallback to RDAP or passive DNS databases. RDAP’s structured queries support enriched metadata retrieval with standardized status and event histories, reducing ambiguity.
Holistic threat hunting combines WHOIS data with historical DNS records and passive DNS, reconstructing domain lifecycles and trust trajectories, essential for accurate attribution despite current dataset incompleteness.
Integrating WHOIS with IP and DNS telemetry enables automated domain blocking, reputation scoring, and remediation workflows, though continuous data quality management and evolving obfuscation tactics demand constant tooling refinement.
Application of WHOIS Information in Infrastructure Automation and DNS Troubleshooting
Infrastructure engineers embed WHOIS data parsing into domain lifecycle monitoring, deployment automation, and fault diagnosis pipelines. Programmatic WHOIS ingestion detects ownership shifts, anomalous renewals, or status flags impacting DNS availability.
Bulk WHOIS lookup processes enable asset portfolio surveillance, alerting on registration changes, suspicious registrar activity, or status flags indicative of suspension or transfer locks—allowing preemptive incident investigation.
During automated DNS rollouts, WHOIS data—especially nameserver assignments and status codes—serve as authoritative checkpoints validating delegation integrity. Discrepancies trigger fail-safe aborts preventing propagation of inconsistent or malformed DNS data.
DNS fault diagnosis integrates layered queries: WHOIS inspection complements live Linux name server lookups and IP resolution commands. Complex cases involving propagation delays or registrar suspensions often become evident when WHOIS status reveals administrative holds despite DNS zone availability.
Automation scripts relying solely on WHOIS dates or statuses face brittleness from stale data or format shifts. Mitigation involves integrating retry logic, heuristics for cache expiry, and fallbacks to authoritative DNS or RDAP queries maximizing data fidelity.
Extended audits combine WHOIS with reverse IP lookups and IP allocation queries to validate domain-to-host associations, essential for detecting unauthorized infrastructure or anomalies impacting network security.
Platforms like DNSimple WHOIS provide modern REST APIs abstracting underlying WHOIS complexity, supporting scalable integration in continuous deployment and monitoring environments. These services enable real-time validation of domain state and rapid reaction to ownership or configuration changes.
Despite benefits, WHOIS remains only one data plane; resilient infrastructure monitoring augments WHOIS with live DNS telemetry and IP reachability data capturing transient, live conditions unobservable through periodic WHOIS polling. Engineers must design hybrid observability layers balancing periodic WHOIS insights with real-time network state.
By scrutinizing WHOIS data’s structure and operational behavior, professionals engaged in ownership verification, cyber defense, and infrastructure automation develop nuanced, reliable methodologies enhancing accuracy, security posture, and operational stability for domain-reliant systems.
Tools, Protocols, and Standards for Accessing WHOIS Information
Popular Tools and Online Services for WHOIS and RDAP Queries
For decades, engineers and analysts have utilized an evolving landscape of tools for WHOIS data retrieval. Traditional approaches center on simple command-line utilities querying WHOIS servers over TCP port 43 with plaintext requests.
The ubiquitous Linux whois client exemplifies these tools, offering straightforward command-line invocation yielding human-readable outputs sourced from authoritative servers. However, operational drawbacks arise: there is no single global registry of WHOIS servers; clients rely on heuristics or hardcoded mappings to contact relevant servers per TLD or IP range. This uncertainty impacts data freshness, completeness, and consistency.
Many registries enforce strict rate limits or connection restrictions, mandating backoff strategies and retry mechanisms in automated scripts to preserve uninterrupted access and avoid blacklisting.
WHOIS response formats vary considerably between registrars, lacking formal schema standardization. Field labels, ordering, and presence vary widely, necessitating custom parsers frequently brittle and require ongoing maintenance in production pipelines.
Modern web-based WHOIS platforms such as DNSimple WHOIS and commercial variants abstract multi-registry complexities, normalizing data and delivering structured outputs suitable for integration via REST APIs. These services offer single and bulk query capabilities, enabling operations like threat intelligence teams processing hundreds of domains simultaneously.
Bulk querying accelerates telemetry, scaling investigations and portfolio audits previously infeasible by manual means. For example, ingestion pipelines feed domain lists to batch WHOIS APIs to obtain uniform metadata for triage and enrichment in SIEM or SOAR systems.
Concurrent with WHOIS, RDAP-aware utilities—e.g., rdap-client, commercial RDAP API providers—enable structured JSON queries resolving legacy parsing challenges. RDAP responses include comprehensive status codes, event histories, privacy annotations, and hierarchical contact metadata, enhancing automation precision.
Due to uneven RDAP adoption and persistent legacy WHOIS dependence, hybrid architectures remain common, requiring tooling capable of protocol detection, fallback, and semantic normalization.
From a reliability lens, CLI WHOIS tools may connect to suboptimal servers, returning incomplete records or outdated metadata. WHOIS lacks standardized status codes and access control, limiting privacy filtering capabilities compared to RDAP. Web WHOIS services applying GDPR-compliant redactions reduce visibility but maintain compliance.
DNSimple and peers implement privacy-aware API overlays, sometimes providing tiered access or authentication to unlock enhanced data, enabling API clients to navigate the tension between regulatory compliance and operational necessity.
The evolution from free-form textual WHOIS outputs to well-defined JSON RDAP responses marks a fundamental shift improving tooling extensibility, robustness, and data fidelity.
Understanding these tool characteristics and trade-offs is essential for system architects and developers building future-proof domain data pipelines.
Transition from WHOIS to RDAP and Implications for Data Access
The transition from WHOIS to RDAP is a significant evolution in domain registration data querying and consumption. WHOIS’s stateless, unencrypted TCP protocol returns free-form text lacking formal, enforceable structure, impeding automated tooling and consistency.
RDAP remedies these deficiencies by adopting RESTful API models over HTTPS, returning structured JSON payloads that encapsulate domain objects, contacts, statuses, and event timelines within rigid schemas. This standardization simplifies deterministic parsing, enabling native JSON querying and schema validation.
Furthermore, RDAP embeds fine-grained access controls satisfying privacy regulations, including GDPR and CCPA. Servers can require client authentication, returning redacted datasets or error codes when data access is unauthorized, thereby aligning domain data sharing with legal compliance. This requires clients implement credential management and handle partial data gracefully.
RDAP also codifies domain lifecycle statuses and standardized event logging—registrations, renewals, transfers, expirations—with timestamps facilitating state machines and event-driven alerting in domain management systems.
Operational implications involve:
- Increased Access Complexity: Authentication tokens, OAuth flows, or API keys introduce new operational burdens for clients. Credentials must be securely managed, synchronized, and permissions audited, contrasting with anonymous WHOIS queries.
- Schema Variance and Field Evolution: Despite standards, registries occasionally diverge in field population or metadata richness, compelling clients to implement robust null handling and fallback strategies preserving data continuity during migration.
- Tooling Overhaul: Legacy CLI WHOIS clients and parsers require redesign or replacement with RDAP-aware libraries capable of JSON parsing and schema validation. This transition provides scalability and reliability benefits but demands upfront engineering investment.
- Backward Compatibility: Many registries maintain WHOIS services alongside RDAP, compelling hybrid tooling capable of protocol negotiation and semantic reconciliation.
The driver behind “whois changes” in domain ecosystems is predominantly regulatory demands and automation scalability, motivating RDAP’s modern replacement status.
Security teams gain auditability and precise domain status information through authenticated RDAP queries. Infrastructure managers and investors benefit from richer metadata and event granularity reinforcing due diligence and asset oversight.
Ultimately, designing domain data integrations demands flexibility to traverse legacy WHOIS unpredictability and RDAP’s structured rigor, a necessary evolution to remain compliant, scalable, and reliable amid growing complexity.
The engineering challenge centers on balancing compatibility, security, and adaptability during the transition, fostering new best practices, robust tooling, and deep domain understanding.
Conclusion
WHOIS remains the pivotal protocol for domain registration metadata access, providing critical insights into ownership, control contacts, domain status, and DNS delegation. Simultaneously, it embodies practical challenges arising from inconsistent formats, privacy-induced redactions, and enforcement constraints limiting automated interoperability and completeness.
The emergence of RDAP heralds a turning point, introducing standardized, structured, authenticated, and privacy-conscious mechanisms for domain data retrieval. This evolution promises improved reliability, richer metadata, and regulatory alignment, essential in increasingly complex and compliance-driven Internet infrastructures.
For security professionals, infrastructure engineers, and domain administrators, mastering these paradigm shifts, understanding WHOIS’s limitations, and strategically integrating complementary data sources like DNS and IP registry lookups are imperative. Building resilient domain validation, threat intelligence, and DNS operation pipelines demands architectures that absorb legacy WHOIS unpredictability while embracing RDAP’s precision.
As systems scale, become more distributed, and regulatory landscapes tighten, the central engineering challenge transitions from mere data retrieval to robust, correct, and compliant metadata consumption underpinning crucial domain-dependent functions. The enduring question is not whether domain data complexity will challenge infrastructure, but how system design equips engineers to render this complexity visible, testable, and actionable under real-world operational pressure.