Key Takeaways
- Domain registration data retrieval protocols are foundational to network operations, cybersecurity workflows, and automated domain management. While WHOIS has long served as the default mechanism for querying domain ownership and registration data, its limitations in extensibility, security, structured queries, and compliance significantly hinder modern use cases. RDAP (Registration Data Access Protocol) introduces a web-centric RESTful approach with JSON data modeling, standardized access control, and inherent privacy compliance features. Engineers working on domain data pipelines, network diagnostics, or security tooling must grasp the distinct architectures, semantics, and operational considerations of WHOIS versus RDAP to build scalable, reliable, and compliant systems.
- Protocol design shift from plain text to HTTP/JSON: RDAP’s adoption of RESTful HTTP APIs returning JSON enables deterministic parsing, smoother integrations across diverse ecosystems, and improved automation scalability compared to WHOIS’s freeform plain-text format.
- Structured data model facilitates extensibility and standardization: RDAP’s well-defined JSON schema explicitly represents domain objects, registration events, entities, and relationships, removing ambiguity and simplifying client logic versus the heuristic textual parsing WHOIS demands.
- Authentication and access control native to RDAP: RDAP supports identity-aware and role-based access control, fundamental for compliance with regulations such as GDPR and CCPA, enabling selective data disclosure policies that WHOIS’s open-access model cannot enforce.
- Integrated support for IPv6 and ASN lookups: RDAP unifies queries across domain names, IPv4 and IPv6 addresses, and Autonomous System Numbers, providing a consistent interface for retrieving network resource registrations—a capability lacking in legacy WHOIS without custom tooling.
- ICANN’s phased migration imposes dual-protocol support constraints: Domain data systems must coexist with both WHOIS and RDAP protocols during the ongoing transition, necessitating flexible integration architectures, protocol detection, and data normalization layers.
- Queryability and error handling improvements reduce ambiguity: RDAP leverages HTTP status codes augmented with detailed JSON error objects, enabling deterministic client error handling and reducing guesswork endemic to the inconsistent WHOIS textual responses.
- Operational impact of HTTPS introduces latency and security benefits: While TLS-encrypted HTTP transport adds connection overhead compared to WHOIS’s lightweight TCP, benefits include encrypted data-in-transit, standardized authentication, caching, and common HTTP infrastructure advantages that mitigate latency impact.
- Privacy-driven data redaction affects completeness and auditability: RDAP’s dynamic response filtering based on authentication and policy requires system designs that anticipate partial or redacted data returns, incorporating fallback mechanisms, reconciliation strategies, or audit trails.
- Transition complexity influences system architecture and monitoring: Supporting RDAP demands revisiting observability pipelines to incorporate HTTP-access logs, JSON payload monitoring, and API-level metrics, replacing legacy WHOIS command output monitoring and creating new operational visibility challenges.
A detailed understanding of these dimensions equips engineers to implement future-proof domain data services conforming to evolving technical standards and regulatory landscapes. The following sections explore WHOIS and RDAP’s architectural fundamentals, protocol mechanics, privacy models, operational trade-offs, and integration patterns.
Introduction
Accessing domain registration data has historically depended on WHOIS, a protocol designed in an era characterized by simple textual queries and open, unrestricted data disclosure. WHOIS’s freeform plaintext responses, absence of authentication, and limited handling of modern identifiers such as IPv6 present significant challenges to today’s automated domain management, cybersecurity tooling, and privacy-conscious applications.
This reality poses a foundational engineering question: how can domain data retrieval be reliably and securely integrated in an environment demanding extensibility, regulatory compliance (e.g., GDPR), and scalable automation? The key lies in understanding the fundamental differences between WHOIS and RDAP—the Registration Data Access Protocol designed to replace unstructured plain-text outputs with RESTful HTTP APIs, structured JSON responses, and embedded access control mechanisms.
This article unpacks the architectural and protocol-level divergences introduced by RDAP, analyzes the operational implications imposed by ICANN’s phased dual-protocol transition, and discusses practical considerations including error handling, privacy enforcement, and performance trade-offs. For engineers building domain lookup services, security analysis tools, or network management platforms, mastering the distinctions between WHOIS and RDAP is crucial for creating robust, compliant, and future-ready systems.
Understanding WHOIS and RDAP: Protocol Fundamentals and Historical Context
Overview and History of WHOIS
WHOIS originated in the early Internet era as a straightforward protocol to query domain registration data via plain-text interactions. Its roots trace back to the 1980s when open, minimalistic client-server models prevailed. Operating over TCP port 43, WHOIS clients send simple textual queries—such as domain names, IP addresses, or Autonomous System Numbers—and receive human-readable plaintext output indicating ownership, administrative contacts, status, and expiration.
WHOIS’s simplicity was initially advantageous but over time became a liability. Unlike modern protocols, WHOIS lacks a standardized response schema; registries and registrars freely vary in format and field definitions, resulting in heterogeneous outputs. This inconsistency impairs automated parsing, aggregation, and integration into large-scale systems. Despite this, WHOIS became the de facto standard for ad hoc ownership verification and manual investigations thanks to its ease of deployment and ubiquitous availability.
However, WHOIS was designed without consideration for authentication, encryption, interoperability with evolving protocols like IPv6, or privacy regulations. It offers no means of restricting query access or customizing response disclosure. Consequently, registrant data—including personally identifiable information—is exposed openly, raising security and compliance concerns. The decentralized management of WHOIS data further compounds inconsistency, with each registry implementing independently, lacking protocol-enforced coordination or schema alignment.
While WHOIS remains a necessary part of many engineers’ toolkit for manual checks or ad hoc queries, its unstructured, plaintext design makes it ill-suited for modern, automated, or privacy-sensitive applications. The protocol’s inherent limitations motivated the development of RDAP, aiming to resolve these persistent issues with a fundamentally reengineered approach.
Introduction and Rationale for RDAP
The Registration Data Access Protocol (RDAP) arose in response to WHOIS’s intrinsic deficits, catalyzed by the Internet Engineering Task Force (IETF) and ICANN’s recognition that WHOIS lacked scalability, privacy, and interoperability for contemporary needs. Formalized progressively via RFC 7480 through RFC 7484 in the early 2010s, RDAP replaces WHOIS’s simple plaintext TCP model with a RESTful HTTP API delivering structured JSON-formatted registration data.
This architectural transformation unlocks several critical improvements. Importantly, RDAP encodes responses as standardized JSON objects, defining explicit schemas for common domain registration elements—handles, entities, status flags, events, and links—thereby enabling deterministic parsing and client interoperability across diverse implementations. By contrast, WHOIS’s variable textual formats demand fragile ad hoc parsing heuristics.
RDAP also embraces support for modern Internet identifiers beyond domain names. It natively accommodates IPv4 and IPv6 addresses and Autonomous System Numbers (ASNs), providing consistent query semantics across domain and network resource registrations. This unified design supersedes fragmented ad hoc mechanisms required in WHOIS.
Regulatory compliance forms a primary driver: RDAP integrates authentication and granular access control into its core. Clients can prove identity via HTTP-based methods (Basic Auth, OAuth, TLS certificates), enabling registries to selectively disclose personal and sensitive information per privacy law requirements like GDPR. This allows tiered data visibility—distinguishing public user queries from authorized investigator requests—a capability impossible under WHOIS’s open-access paradigm.
Additionally, RDAP harnesses HTTP status codes and structured error responses, furnishing clients with precise feedback on query success, authentication failures, or rate limiting. Internationalization is factored into the design with UTF-8 encoding and unicode support, facilitating global applicability.
Operationally, RDAP adoption enables smoother backend integrations, reducing brittle text-parsing burdens and latency uncertainty. Registries report maintenance cost reductions from streamlined tooling, enhanced query accuracy, and simplified API-based client implementations. IPv6 lookups, previously unreliable via WHOIS, become consistent and straightforward.
ICANN’s policies now compel registries and registrars to implement RDAP alongside WHOIS, encouraging but not yet mandating full WHOIS retirement. This phasewise transition introduces complexity requiring hybrid support architectures.
In real-world deployments, RDAP endpoints often yield reduced latency owing to HTTP optimizations and caching, improved privacy controls by default, and uniform data structures that simplify client-side tooling. RDAP therefore establishes a new baseline for secure, extensible, and standards-compliant domain registration data access aligned with modern engineering principles and regulatory regimes.
The progression from WHOIS’s ad hoc plaintext queries to RDAP’s formalized, machine-readable RESTful architecture epitomizes the evolution necessary for scalable, automated network infrastructure. Understanding these design trade-offs and their operational manifestations equips engineers to methodically approach domain data integration challenges. For further technical details, refer to ICANN’s RDAP implementation guidelines and the IETF RDAP specifications RFC 7480-7484.
Protocol Mechanics and Data Structures
Building on the historical overview, a closer examination of WHOIS and RDAP’s protocol mechanics and data modeling highlights foundational architectural differences critical for engineering integration.
WHOIS operates as a legacy TCP-based client-server protocol over port 43. Clients open raw TCP connections, send minimally structured ASCII queries (typically a domain name or IP), and receive ASCII plaintext responses comprising attribute-value pairs formatted loosely by each registry. There is no formal schema or structured typing. This unstructured textual output exhibits significant variability in field naming, order, and localization, even diverging across top-level domains and registrars.
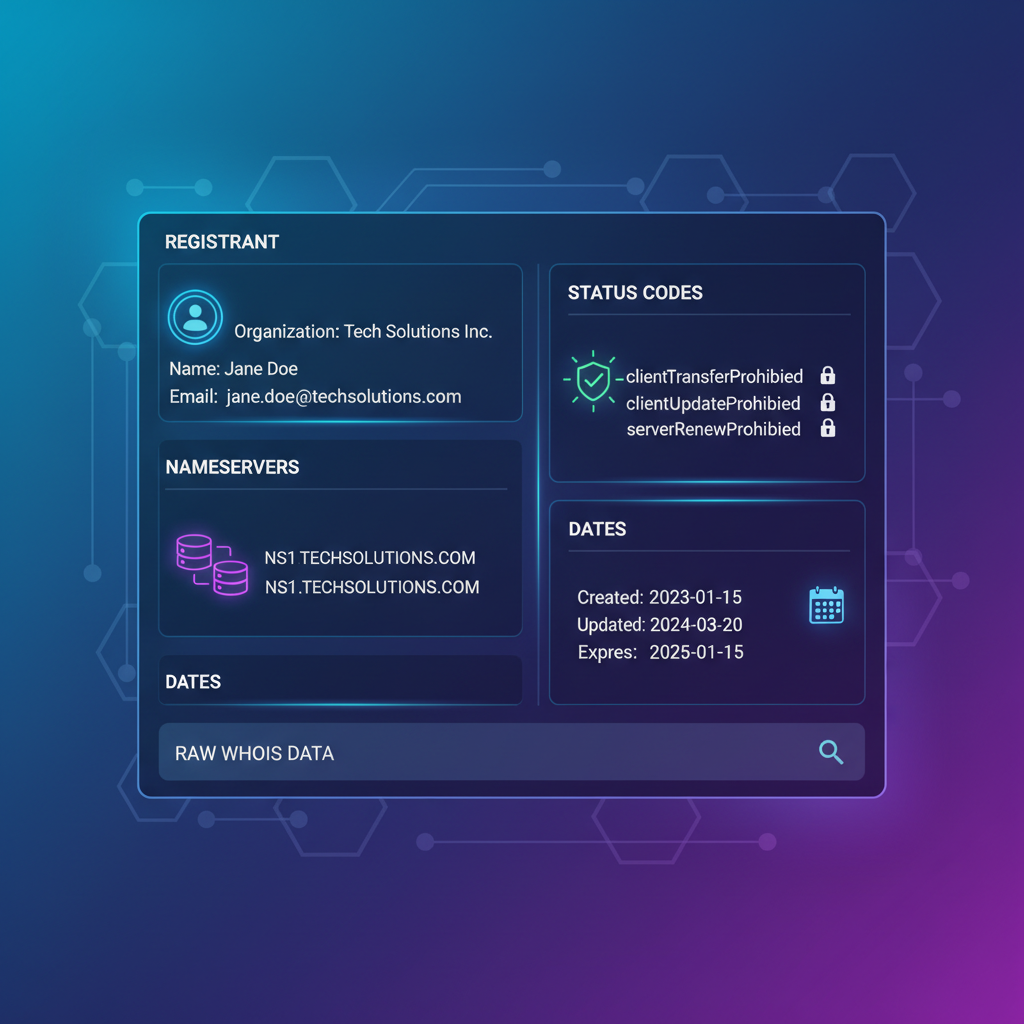
For software clients, this means relying on brittle regular expressions or heuristics to extract desired information such as registrant contacts, domain statuses (e.g., “clientTransferProhibited”), nameservers, or expiration dates. Such brittle parsing is error-prone, especially under variations in WHOIS output, impeding reliable automation and integration at scale.
In contrast, RDAP employs HTTP as its transport protocol and embraces RESTful API design principles. Queries encode target resource types (domains, IP addresses, ASNs, entities) in URL path segments and HTTP GET methods. Responses are JSON documents conforming to explicit, standardized schemas defined in RFC 8525 and related documents. Core JSON objects encapsulate registration data into strongly typed fields such as “handle,” “status,” “entities,” “events,” and “links.”
For example, rather than searching for a free-text “Registrant:” line, the client accesses nested JSON objects representing role-based entities, including standardized vCard-compliant contact info arrays. This structural clarity enables deterministic parsing and straightforward validation, drastically reducing client logic complexity.
Operating over HTTP also unlocks well-understood infrastructure capabilities: HTTP status codes encode success or error semantics precisely (e.g., 200 OK, 404 Not Found, 401 Unauthorized), enabling clients to implement robust error handling based on standardized conventions, something WHOIS cannot provide consistently. Additionally, HTTP caching directives (ETags, Cache-Control headers) enable efficient client-side and intermediate caching—improving scalability and reducing redundant backend access.
Moreover, RDAP supports extensibility through its JSON schema, permitting registries to embed custom properties or vendor-specific extensions without disrupting base interoperability. URL path segmentation accommodates granular queries (by domain, IP, ASN) and provides discoverability features, aiding developer experience.
Unlike WHOIS’s fixed TCP port, RDAP uses standard web ports (typically 443 for HTTPS), improving firewall compatibility and enabling encrypted transport without requiring specialized network configurations.
Taken together, RDAP’s redesigned protocol mechanics and structured data model deliver a step-change improvement, facilitating maintainable, scalable, and secure client-server interactions critical for modern domain data access systems.
Authentication, Extensibility, and Network Identifier Support
Extending the earlier discussion, authentication, extensibility, and network identifier coverage are pivotal dimensions where RDAP diverges profoundly from WHOIS, directly addressing deficiencies that limit legacy operational viability.
WHOIS’s open-access model assumes anonymous queries with no verification, authorization, or access restrictions. This openness hinders privacy compliance and exposes registrant data indiscriminately. Furthermore, WHOIS’s plaintext output format prohibits formal extension or metadata inclusion without breaking parsers, limiting flexibility.
RDAP integrates authentication natively via HTTP mechanisms: servers may require HTTP Basic Authentication, OAuth tokens, or client certificates to verify client identity. This authentication allows registries to implement granular access control policies, enabling tiered data visibility depending on requester role, legal authority, or business rules. For example, detailed personally identifiable data can be revealed selectively to law enforcement or accredited probes while redacted for casual public queries. This greatly enhances GDPR compliance capacity, enforcing “least privilege” data exposure algorithmically.
RDAP communicates access enforcement clearly using standard HTTP response codes (401 Unauthorized, 403 Forbidden) combined with detailed JSON error descriptions, enabling automated client handling. WHOIS, lacking standardized status signals, resorts to ambiguous textual error messages or silent connection drops, complicating client recovery.
Extensibility benefits from RDAP’s JSON schema-based design. Registries can augment records with vendor-specific metadata, verification status, blockchain anchors, or auxiliary identifiers without compromising schema conformance. Clients ignoring unknown extensions can continue without failure, supporting graceful evolution. WHOIS’s unstructured text prohibits such backward-compatible extensions, forcing brittle workarounds.
Critically, RDAP expands query coverage to encompass modern network identifiers uniformly. It supports dedicated endpoints for querying IPv4 and IPv6 addresses (/rdap/ip/{ipAddress}) and Autonomous System Numbers (/rdap/autnum/{asn}), delivering hierarchical resource metadata with allocation records, organizational contacts, and historical events. This integration overcomes WHOIS’s patchwork support for IP and ASN data, which often requires invoking multiple proprietary or registry-specific services.
A unified query interface enables cybersecurity tools, network operators, and registrars to retrieve cohesive ownership and registration information spanning domains and network layers seamlessly, streamlining operations and reducing error-prone data stitching.
Operationally, RDAP’s reliance on HTTP enables leveraging standard web technologies for scalability, monitoring, and security. HTTP logging, analytics, and authentication tokens integrate naturally with existing infrastructure, simplifying operational overhead compared to specialized WHOIS TCP daemons. Standard protocols also facilitate deployment automation, including load balancing and failover.
In summary, RDAP’s advances in authentication, extensibility, and network resource support modernize domain data services fundamentally, aligning them with contemporary security, privacy, and architectural best practices essential for evolving Internet ecosystems.
Privacy, Access Control, and Regulatory Compliance Improvements with RDAP
Privacy Limitations in WHOIS and Impact on Data Exposure
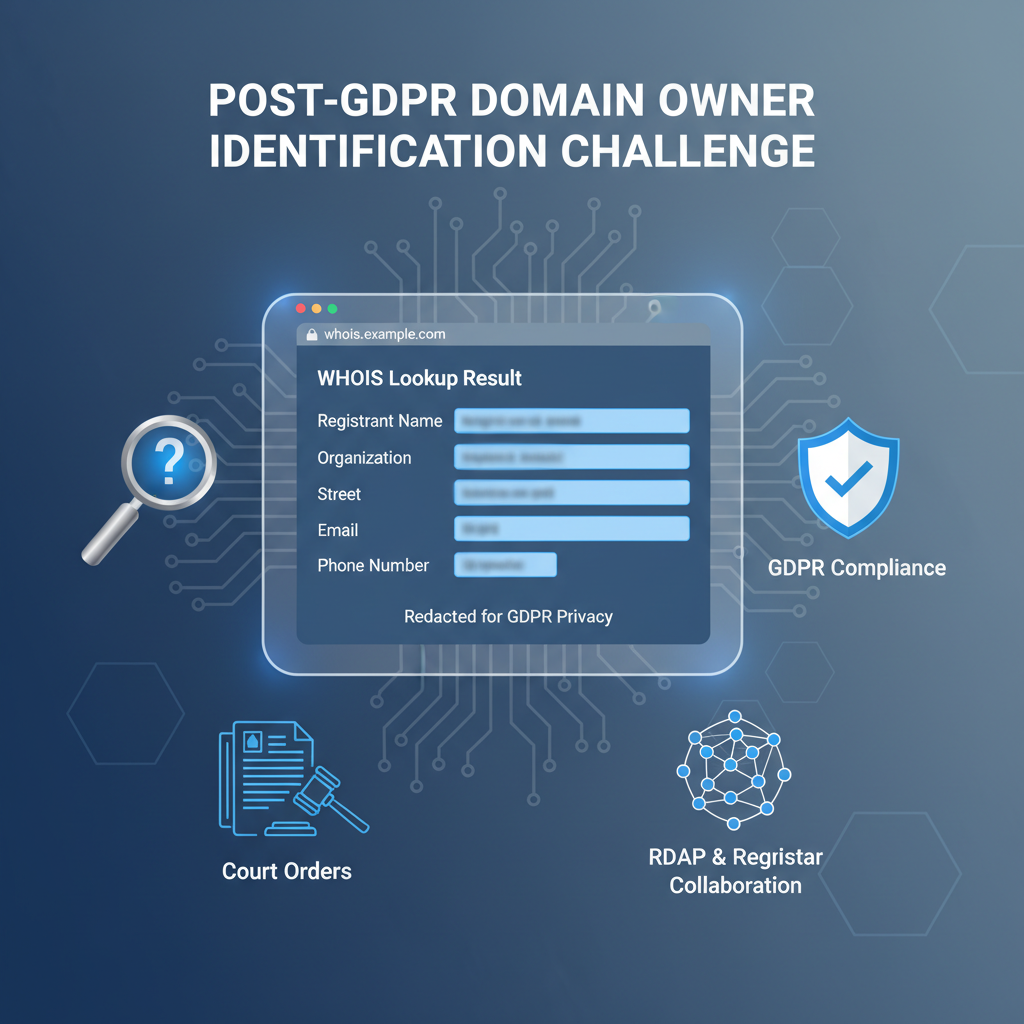
WHOIS’s design ethos embraced open, unrestricted data access, which starkly conflicts with today’s privacy expectations and regulatory obligations. The protocol lacks any authentication or role-based access control; all personal registration details—names, addresses, phone numbers, emails—are exposed to any querier, whether benign or malicious.
This universal data exposure enables large-scale automated harvesting of registrant information, feeding spam campaigns, phishing infrastructures, and other abuse vectors. The plaintext textual responses emitted by WHOIS servers facilitate effortless parsing and indexing, magnifying risk. The absence of fine-grained data control also hinders registries’ ability to enforce differential access or monitor data usage effectively.
From a compliance standpoint, WHOIS is inadequate for regimes like GDPR, which require lawful basis, purpose limitation, and minimization of personal data disclosure. WHOIS offers no built-in controls or mechanisms to tailor response contents by jurisdiction, data subject consent, or requestor authorization status. Compliance is typically enforced manually or via brittle external filters, introducing operational overhead and data inconsistency.
Moreover, WHOIS applies either blanket redaction (obscuring entire registrant contact details) or none at all, lacking nuance or dynamic filtering capabilities. This all-or-nothing approach restricts operational flexibility, impeding legitimate lawful requests for full data disclosure—such as intellectual property investigations or law enforcement access—while failing to prevent misuse effectively.
From an engineering perspective, this inflexible exposure model forces registry operators to implement patchwork solutions atop WHOIS servers: firewalls blocking IP ranges, front-end query filtering proxies, or output scrubbing scripts. These interventions increase complexity, risk accidental exposure, and demand extensive maintenance. In automated tooling, parsers frequently fail or misinterpret redacted fields, complicating data validation and auditing efforts.
Collectively, these deficiencies underscore the urgent need for a domain data access protocol that intrinsically embeds privacy and access controls—terms WHOIS fundamentally cannot meet.
RDAP’s Access Control and Privacy-Aware Data Access
RDAP provides a comprehensive architectural remedy to WHOIS’s privacy and access control limitations by embedding identity verification, authorization policies, and dynamic data redaction directly into the protocol design.
RDAP servers enforce client authentication using standardized HTTP-supported mechanisms such as OAuth tokens, client certificates, or API keys. This robust assignment of requester identity enables registries and registrars to apply differentiated access controls, aligning data disclosure with requestor role, legal authority, and jurisdiction.
This capacity facilitates “least privilege” exposure, dynamically redacting or masking personally identifiable information based on policy. For instance, public queries may return anonymized or aggregated data, while authenticated law enforcement requests yield full contact information. This contextual differentiation complies with GDPR’s requirement to control personal data access appropriately and auditably.
Responses remain in structured JSON format, supporting programmatic integration with data filtering and auditing frameworks that enforce policy systematically. The RDAP schema’s extensibility enables metadata annotations indicating redaction reasons or verification statuses, reinforcing transparency and traceability.
RDAP’s use of UTF-8 encoding supports internationalized registrant names and metadata, allowing multilingual and multicultural data disclosure consistent with legal and usability requirements.
Access enforcement response codes (HTTP 401, 403) with rich JSON error explanations inform clients clearly about authorization state, facilitating automated workflows and user feedback without guesswork common in WHOIS.
Operational logging of authenticated requests with granularity—tracking requester identity, timestamps, query parameters, and response scope—provides audit trails essential for regulatory reporting, anomaly detection, and abuse mitigation. This level of observability is unattainable in WHOIS’s anonymous query model.
By implementing these privacy-aware design principles, RDAP streamlines compliance with global data protection laws while maintaining operational transparency and trust. It alleviates manual redaction burdens, reduces operational risk, and enables secure, scalable data sharing across stakeholders.
Transitioning to RDAP requires updating client tooling to handle authentication protocols and parse structured JSON responses. Credential management and identity federation become new operational domains. Systems must also prepare for partially redacted responses and implement fallback or reconciliation strategies accordingly.
Nonetheless, RDAP’s architecture presents a necessary evolution, empowering registries and network operators to navigate the modern regulatory landscape without sacrificing accessibility or operational efficiency.
For practical insights on these privacy-improving implementations, see Cloudflare’s article on Improving Domain Privacy with RDAP and the IETF RDAP Protocol Overview (RFC9082).
The contrast between WHOIS’s indiscriminate, unfiltered data exposure and RDAP’s authenticated, policy-driven model highlights the transformational shift enabling registries and registrars to meet stringent privacy mandates effectively. The next section explores how this evolution plays out in ICANN’s regulatory transition and the resultant technical challenges.
ICANN’s Transition from WHOIS to RDAP: Timeline and Dual-Protocol Implications
ICANN’s Phased Implementation Strategy
ICANN’s migration strategy replaces legacy WHOIS with RDAP via a carefully staged, dual-protocol deployment approach. This measured transition balances the necessity of modernization with the imperative of uninterrupted service across a vast global ecosystem dependent on WHOIS.
ICANN mandates stipulate that registries and registrars deploy RDAP implementations conforming to protocol standards (RFC 7480–7484, RFC 8525), accessible over HTTPS, and supporting domain, entity, and nameserver queries with UTF-8 encoded outputs. Key deadlines since 2019 have incrementally escalated the obligation to support RDAP, while explicitly requiring WHOIS services to remain concurrently available.
This dual-stack approach addresses operational realities: legacy tools, monitoring systems, customer workflows, and automated scripts strongly depend on WHOIS’s simple query-response model. Immediate WHOIS deprecation risked widespread disruption. Additionally, registries vary extensively in technical maturity and resource availability, necessitating flexible timelines and incremental rollout.
ICANN’s policy framework codifies RDAP expectations including required HTTP status code support, standardized error structures, data internationalization, and redirection capabilities uniquely supporting chained queries (a crucial improvement over WHOIS).
Monitoring and enforcement include contractual provisions obligating registries to maintain functional RDAP endpoints, with ICANN publicly reporting compliance. Vendors and operators have built dual-protocol infrastructures—coordinating data feeds, query mappings, and schema normalization layers—to fulfill these mandates.
This transition exemplifies the challenge of evolving entrenched Internet infrastructure: reconciling legacy protocol ubiquity with the imperative for extensible, secure, privacy-aware alternatives. Architecting systems to support WHOIS and RDAP simultaneously demands deliberate design decisions encompassing protocol detection, query routing, consistent formatting, synchronized data sources, and operational monitoring.
For comprehensive technical guidance, refer to ICANN’s authoritative RDAP documentation and related policy notices.
Operational Challenges in Supporting Both WHOIS and RDAP
The necessity to maintain simultaneous WHOIS and RDAP services introduces multifaceted operational complexities spanning system architecture, data consistency, error handling, and observability.
From an architectural perspective, WHOIS and RDAP embody radically different service paradigms. WHOIS offers a minimalistic TCP socket-based plaintext query-response model, whereas RDAP operates as a full HTTP(S) RESTful API delivering structured JSON responses. Supporting both requires either parallel server stacks or multiprotocol-capable platforms, increasing infrastructure footprint and maintenance overhead.
WHOIS servers focus on rapid, stateless TCP interactions on port 43, built often on monolithic daemons optimized for simple line-based response serialization. RDAP servers serve hierarchical JSON over standard web ports with sophisticated authentication, authorization, and error semantics, often deployed in containerized or cloud environments leveraging modern API frameworks.
Reconciliation of these divergent protocols demands backend pipelines capable of serializing consistent domain registration data into both formats simultaneously. This includes field normalization, internationalization, and aligned timestamps to prevent cross-protocol data drift. Asynchronous data refresh propagation can cause transient mismatches, eroding trust in queried data and complicating operational decisions.
Error handling semantics differ markedly. WHOIS provides human-readable but inconsistent error messages, often varying by registry implementation, requiring client heuristics to interpret. RDAP adopts formal HTTP status codes with extended JSON error objects enabling unambiguous client responses. Translating internal backend error states into two distinct paradigms and ensuring synchronized behavior is non-trivial.
Access control creates further divergence. RDAP supports dynamic, authenticated selective disclosure with per-request filtering; WHOIS typically applies static redaction or none at all, leading to discrepancies in data visibility and potential confusion among end users or automated systems consuming either protocol.
Operationally, running dual protocols increases resource requirements (CPU, memory, network bandwidth). Monitoring and alerting tooling must handle multiple log formats and telemetry sources, parse verbose JSON payloads versus plaintext logs, and detect protocol-specific anomalies. Incident response teams must be trained to diagnose two fundamentally different protocols with distinct failure modes.
Legacy WHOIS-dependent tooling continues to dominate some use cases, necessitating transitional client updates or support layers translating RDAP responses into WHOIS-like textual formats transitorily, adding complexity.
Balancing backward compatibility and forward adaptability, organizations need modular, testable architectures enabling coexistence, graceful feature rollouts, and clear operational boundaries between protocol stacks.
This dual-protocol operational complexity reflects the broader industry challenge of evolving critical infrastructure while ensuring uninterrupted service and compliance—a problem domain increasingly relevant as protocols and data models mature.
Having established these architectural and operational realities, the discussion now turns to how the protocol evolution impacts downstream automation, security tooling, and network management workflows.
Practical Implications of WHOIS vs RDAP for Domain Data Queries
Impact on Automation, Security, and Network Management Tools
The shift from WHOIS to RDAP marks a fundamental transformation in how domain data queries integrate into automated pipelines, security monitoring, and network management ecosystems. The transition from unstructured plaintext over simple TCP to structured JSON over RESTful HTTP APIs catalyzes improvements across automation compatibility, security postures, and extensibility.
Automation Compatibility
WHOIS’s free-text TCP query-response model—originating prior to widespread automation paradigms—forces engineering teams to develop brittle, heuristic-based parsers with fragile dependencies on textual format idiosyncrasies. These limitations hinder scalability and reliability in large-scale or real-time network management systems processing vast query volumes.
RDAP’s alignment with standard web technologies and well-documented JSON schemas enables deterministic parsing and validation, seamlessly integrating with modern DevOps pipelines, data processing frameworks, and orchestration tools. RESTful design facilitates native support in languages and libraries ranging from Python requests modules to JavaScript fetch APIs.
For instance, intrusion detection systems leveraging domain registration and ASN ownership data can automate reputation lookups querying RDAP endpoints and parsing nested JSON responses directly, eliminating error-prone text extraction layers. This sharpens real-time detection accuracy and reduces operational overhead.
Similarly, infrastructure-as-code tools provisioning network resources integrate RDAP queries into lifecycle automation, verifying domain hygiene or IP ownership dynamically. Bulk asset management systems conduct concurrent RDAP queries with straightforward pagination and standardized error handling, enabling consistent synchronization of domain affiliation across global inventories.
RDAP’s extended network resource support (IPv6, ASNs) simplifies integration across layers, unifying domain, IP, and routing data essential for comprehensive threat hunting and network diagnostics.
Security Integration
WHOIS’s unencrypted plaintext over TCP and lack of authentication expose sensitive registration records to interception and unauthorized scraping, impairing confidentiality and data integrity guarantees—risks unacceptable in modern security contexts.
RDAP’s default operation over HTTPS encrypts data in transit, thwarting passive eavesdropping. Built-in authentication and authorization support enable controlled access to sensitive details, ensuring compliance with privacy regulations and reducing exposure to abuse.
Security information and event management (SIEM) systems can safely integrate RDAP queries, reducing risk of data leaks during automated enrichment. Audit trails embedded in RDAP infrastructure provide investigative transparency, supporting compliance audits and abuse detection.
Additionally, RDAP’s error handling and rate-limiting capabilities prevent abuse and mitigate denial-of-service risks more effectively than WHOIS’s simplistic connection model.
IPv6 and DNS Performance Testing Automation
WHOIS’s inconsistent support for IPv6 and limited ASN handling present obstacles to fully automated IP network assessments and DNS performance measurement tools. Its textual response variations and lack of standardized metadata inhibit reliable data extraction.
RDAP’s uniform JSON-based representation of IPv6 address allocations, subnets, ASN ownership, and related metadata streamlines scripting of automated tests, DNS latency measurements, and targeted network scans across IPv4 and IPv6 spaces. This completeness enhances network operators’ ability to associate domain data with IP topology and routing information.
Automated dns performance test suites and command prompt ping ip scripts leveraging RDAP can dynamically adapt probes based on accurate ASN and prefix data, improving the quality and relevance of network performance metrics.
RDAP’s schema extensibility ensures future adaptations incorporating emerging network identifiers or verification metadata can be incorporated without breaking existing automation.
Error Handling, Performance, and User Experience Differences
Error Response and Diagnostics
WHOIS error signaling is inconsistent and textual. Servers may return “No match,” ambiguous notices, or silent failures, lacking standardized machine-readable indicators of query results. Clients must apply heuristic text parsing, complicating automation error detection and recovery logic.
RDAP leverages HTTP status codes (e.g., 404 Not Found, 400 Bad Request, 429 Too Many Requests) and augments them with structured JSON error objects containing defined error codes, titles, and explanatory messages. This precision enables deterministic error handling in automated systems, reducing false positives and improving failure diagnostics.
For example, automated systems integrating command prompt ping ip workflows can differentiate between client-side malformed requests, non-existent records, or temporary throttling states, implementing intelligent retry, backoff, or alerting logic accordingly.
This predictability improves operational incident response and reduces troubleshooting burdens.
Performance and Protocol Overhead
WHOIS’s minimal TCP plaintext model incurs low per-request latency due to limited protocol overhead and connection simplicity. It excels in low-latency single queries but scaling is constrained by lack of HTTP-level caching, multiplexing, or proxying infrastructure compatibility.
RDAP introduces inherent overhead from HTTPS (TLS handshakes, encrypted data transmission) and richer JSON payloads. However, this overhead is typically marginal relative to application-level benefits. RDAP protocols support standard HTTP optimizations—persistent connections, pipelining, caching with ETags, compression—allowing efficient bulk query processing at scale.
Modern HTTP infrastructure—content delivery networks, load balancers, API gateways—facilitate horizontal scaling and robust uptime for RDAP services, surpassing WHOIS’s bespoke TCP daemon limitations.
Empirical observations show modest latency increases (~tens of milliseconds per request) but dramatically improved throughput, parallelism, and client reliability.
From a system design viewpoint, protocol overhead trades enhanced security, deterministic data, and better tooling integration for slightly increased connection complexity—an advantageous exchange given Internet-scale demands.
User Experience and Tooling Implications
WHOIS tools traditionally present raw plaintext, which users must parse mentally or visually, impeding fast insights and increasing cognitive load. Variability in field formats and inconsistent layouts exacerbate the problem.
RDAP’s structured JSON outputs enable sophisticated client applications to render user interfaces that organize domain data intuitively: hierarchical display of entities, linked contact hierarchies, status timelines, and multilingual support. Hyperlinks embedded in responses facilitate drill-down navigation across related resources, enriching investigations.
Network operation centers (NOCs), security analysis platforms, and domain management portals exploit RDAP’s data clarity to improve analyst efficiency, reduce human error, and automate workflow transitions.
The improved error messaging supports clearer feedback loops in end-user applications and reduces incident handling overhead.
Overall, RDAP’s user experience improvements—from developer tooling to operational dashboards—foster greater adoption of domain data services in automated and human-in-the-loop systems.
By advancing from textual ambiguity to structured clarity, RDAP revolutionizes the technical and operational paradigms of domain data querying—enhancing automation, security, and usability across the infrastructure stack.
Conclusion
The transition from WHOIS to RDAP encapsulates a profound architectural modernization in domain registration data access, addressing WHOIS’s limitations in standardization, privacy, extensibility, and automation. RDAP’s RESTful APIs, structured JSON schemas, and integrated authentication frameworks form a coherent, machine-consumable protocol aligned with stringent regulatory mandates like GDPR, enhancing both security and operational transparency.
ICANN’s phased dual-protocol rollout underscores the challenge of evolving entrenched Internet infrastructure while ensuring backward compatibility and ecosystem stability. Architects and engineers must design flexible, composable systems capable of harmonizing WHOIS and RDAP data streams, maintaining data consistency, and accommodating divergent error models and access controls.
Adopting RDAP unlocks performance, scalability, and usability gains crucial for integrating domain data into modern automation pipelines, security monitoring platforms, and network management suites. Yet this adoption brings new complexity in credentials management, partial data handling, and observability tooling that organizations must address prudently.
Looking forward, the critical engineering question shifts from whether to support RDAP to how best to evolve systems to leverage its capabilities—embedding privacy-first designs, robust authentication, and extensible data models as foundational principles. As domain ecosystems scale and regulatory environments tighten, sustainable architectures will need to surface protocol complexity transparently, enable continuous validation, and foster interoperability across fragmented deployments.
This evolving landscape invites rethinking domain data retrieval as part of broader Internet infrastructure modernization—demanding thoughtful design balancing openness, privacy, scalability, and operational resilience under growing pressure and sophistication.