Introduction
Domain spoofing remains a persistent and insidious blind spot within contemporary security architectures, as attackers exploit fundamental weaknesses embedded in DNS and email protocols to impersonate trusted brands at scale. Beyond rudimentary look-alike URLs, sophisticated techniques such as typosquatting, DNS manipulation, and exploitation of incomplete or misconfigured SPF, DKIM, and DMARC email authentication frameworks create attack surfaces that evade conventional filtering mechanisms, undermining trust in digital communications. This reality prompts an urgent technical challenge: how can software engineers and security practitioners detect and intercept domain spoofing activities proactively, preventing them from escalating into large-scale phishing campaigns or fraud operations?
The complexity magnifies when domain spoofing converges with related threats like domain hijacking and squatting, complicating attribution and response efforts by obfuscating ownership records in WHOIS databases. These tactics require continuous monitoring of domain registration lifecycles and transfer states—including nuances involved in migrating domains across popular providers such as Namecheap, Hostinger, or AWS Route 53—that can introduce vulnerabilities mid-transition. This article dissects the underlying technical mechanisms of domain spoofing, details practical detection methodologies including similarity algorithms and blacklist integration, and elucidates critical trade-offs engineers must consider when architecting resilient defenses suitable for high-scale, real-world deployments.
By advancing an understanding that spans registration intricacies to DNS-level manipulations, engineers can better architect systems that maintain brand integrity and uphold end-user trust amidst an evolving threat landscape.
Fundamentals of Domain Spoofing
Defining Domain Spoofing and Related Concepts
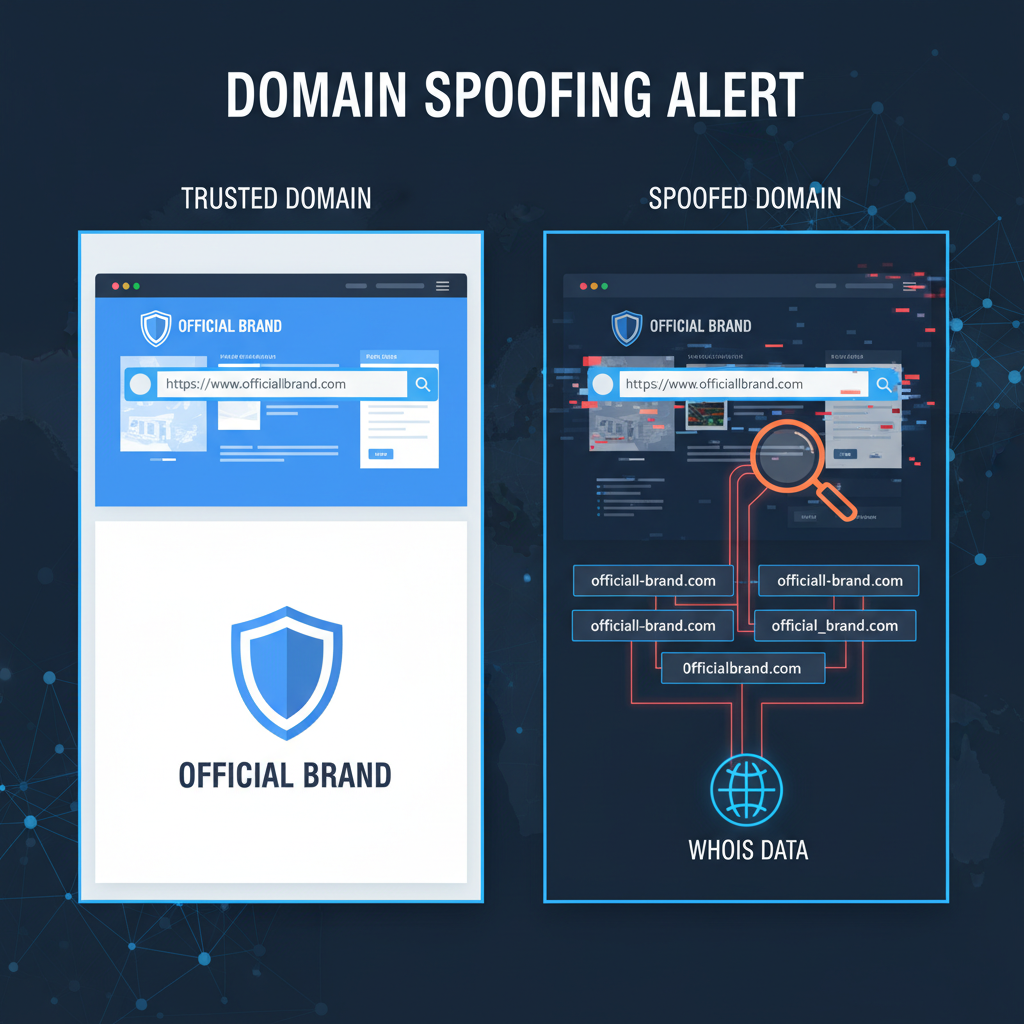
Domain spoofing constitutes the deliberate and malicious registration or manipulation of domain names designed to impersonate trusted brands, organizations, or entities, thereby deceiving users into interacting with seemingly legitimate sources. At the heart of this threat lies exploitation of the hierarchical structure and delegation mechanisms of the Domain Name System (DNS), which attackers leverage to create domains closely resembling well-known trademarks or web properties. Unlike broader phishing attacks that chiefly rely on social engineering or malware payloads, domain spoofing zeroes in specifically on the domain layer, fashioning deceptive digital identities at the DNS resolution level.
It is essential to distinguish domain spoofing from associated but technically distinct vectors:
- Email Spoofing: This involves forging the email sender’s domain or “From” field to make emails appear as if originating from trusted domains, without necessarily controlling those domains. Email spoofing exploits the lack of inherent authentication in the SMTP protocol, allowing adversaries to inject arbitrary domain names into email headers. This separation from domain registration means attackers can impersonate executives or brands via email without owning matching domains, often executing spear-phishing or CEO fraud attacks.
- URL Spoofing: This method crafts deceptive URLs designed to appear linked to legitimate sites but actually funnel users to malicious content. Tactics include subdomain manipulation (e.g.,
paypal.com.attacker.com, where the recognizable brand is a subcomponent, but the registered domain isattacker.com), complex redirection chains, URL encoding tricks, punycode, and homoglyph character substitutions. These techniques target the user interface and browser rendering level, complicating visual detection by end-users. - Typosquatting: Generally viewed as a subset of domain spoofing, typosquatting registers domains close to legitimate ones by exploiting common manual input errors—misspellings, character omissions, substitutions, duplications, or keyboard adjacency analogs. Typosquatting domains often serve as fertile ground for credential theft, malware distribution, or ad fraud by diverting traffic from legitimate sites.
For instance, attackers in 2017 utilized a punycode domain resembling “xn--pple-43d.com”—a visually similar Unicode encoding to “apple.com”—to deploy phishing pages that harvested Apple ID credentials. Similarly, variants like “faceboook.com” or “amaz0n.com” have regularly appeared in large-scale phishing campaigns aimed at consumer and enterprise users.
Disambiguating these tactics is vital because each targets distinct protocol layers and human factors, necessitating tailored detection and defense approaches. Failing to recognize the nuances between domain spoofing and email spoofing, for example, risks overreliance on email filters without concurrent domain registration monitoring or DNS-level defenses.
Common Techniques Used in Domain Spoofing
Domain spoofing attackers use a range of techniques spanning domain registration exploits, direct DNS infrastructure manipulation, and leveraged character encoding vulnerabilities. These approaches balance cost efficiency, scalability, and deception potency.
Typosquatting Techniques
Typosquatting hinges on automating the generation and registration of plausible misspelled domain variants at scale. Attackers employ heuristic models simulating human typographical errors, such as:
- Omission: Missing a character (e.g., “gogle.com” vs. “google.com”)
- Permutation: Swapping adjacent letters (“googel.com”)
- Substitution: Replacing characters with nearby keyboard keys or visually similar characters (e.g.,
m → n,l → i) - Duplication: Repeating characters (“gooogle.com”)
- Character replacement: Using digits or symbols instead of letters (“faceb00k.com” uses ‘0’ instead of ‘o’)
Mass registration services and lax registrar vetting amplify the scalability of typosquatting campaigns. From a cost-benefit perspective, even low-cost registrations become profitable given the potential traffic hijacking and monetization via ad fraud, credential phishing, or malware deployment.
Notably, the Mirai botnet exploited typosquatted command-and-control domains closely resembling targeted infrastructure, complicating both network detection and human analysis. Defensive responses include brand monitoring services that preemptively flag suspicious registrations and user education focusing on URL hygiene across diverse platforms such as web browsers, APIs, and mail clients.
DNS Spoofing (Cache Poisoning)
DNS spoofing, or cache poisoning, attacks diverge from domain registration-based spoofing by targeting the DNS resolution process itself. Attackers inject forged DNS records (e.g., A, AAAA, or TXT records) into recursive DNS resolver caches, causing legitimate domain queries to resolve to malicious IP addresses without altering domain registrations.
Exploitation vectors include:
- Leveraging vulnerabilities in DNS software to accept unauthorized DNS responses
- Racing legitimate DNS responses with counterfeit data to poison the cache
- Direct compromises of authoritative DNS zones or resolver infrastructure
The 2008 Kaminsky attack famously exploited cache poisoning to compromise vast portions of the DNS ecosystem. Mitigations rely on cryptographic validation via DNSSEC, which mandates signed responses validated by resolvers, effectively preventing undetected record injection. Operational best practices also include resolver patching, rate limiting, and preferring trusted upstream DNS servers.
DNS spoofing undermines trust mechanisms that rely on DNS integrity, allowing attackers to bypass domain reputation systems and certificate validation. When combined with registered spoof domains (e.g., typosquatted names), compromised DNS caches dramatically raise the effectiveness of phishing or malware delivery schemes in backend infrastructure and end-user environments alike.
Homoglyph Attacks and Punycode Domains
Homoglyph attacks exploit Unicode character sets, registering deceptive domain names that visually mimic existing domains but differ at the binary encoding level. For instance, Cyrillic ‘а’ (U+0430) is visually identical to Latin ‘a’ (U+0061), yet these domains represent distinct DNS entries.
The DNS system’s support for Internationalized Domain Names (IDNs) via punycode encoding enables these attacks by translating Unicode domain names into ASCII-compatible strings (e.g., “xn--80ak6aa92e.com”), which browsers interpret and display. Modern browsers implement defenses by rendering punycode explicitly or warning users when mixed-script domains are detected.
From an operational stance, homoglyph domain detection requires Unicode normalization, font glyph analysis, and sophisticated fuzzy string matching algorithms. Attackers exploit this vector to create near-perfect visual impersonations often targeting critical infrastructure and high-visibility brands. A 2019 incident involving the homograph domain “раураl.com” (with Cyrillic characters) successfully phished PayPal users by exploiting visual indistinguishability.
Traditional blacklist and heuristic filters face challenges detecting homoglyph spoofing, necessitating layered defenses including domain verification services, user agent telemetry, and endpoint protections aware of Unicode rendering nuances. Browser vendors’ proactive mitigations remain part of a broader defense ecosystem.
This comprehensive understanding of domain spoofing fundamentals underscores the necessity for multi-layered detection strategies and guides exploration of the operational mechanics of these attacks at scale.
Mechanics of Domain Spoofing Attacks and Phishing Exploits
Domain spoofing operates as a multifaceted technical threat vector wherein attackers fabricate deceptive domain registrations and strategically leverage email and web protocols to convincingly impersonate trusted entities. At the technical core, attackers exploit weaknesses in DNS delegation, domain registration oversight, and email sender authentication frameworks to register or forge domains closely resembling legitimate brands.
These mechanics rest on structural ambiguities in DNS and registrar systems—brand domains are typically registered without semantic validation and proliferate rapidly across registrars, exposing fertile grounds for look-alike domain registrations with minimal friction. Automation APIs offered by registrars increase attackers’ capacity to generate extensive spoofing infrastructures comprising numerous typosquatted, homoglyph, or subdomain manipulative domains.
Key spoofing techniques manifest in:
- Email Spoofing: Forging “From” fields in emails to simulate trusted senders, often combining forged header information with registered deceptive domains to increase credibility in recipients’ inboxes and bypass filters.
- URL Spoofing: Registering deceptive domains that exploit homoglyphs, typographical variants, or subdomain obfuscations to fool users and evade simplistic string-matching filters in both browsers and network appliances.
- Typosquatting: Automated pre-registration of domains reflecting prevalent human input errors, generating landing pages designed for phishing, malware distribution, or advertising fraud.
The subtlety of homoglyph substitution further complicates detection since visually identical domains diverge at the byte encoding level, necessitating enhanced string similarity scoring based on Unicode-aware comparison methods.
These attacks intertwine with social engineering by preying on users’ cognitive trust in recognized branding, increasing phishing campaign efficacy. The attacker’s capacity to blend multiple spoofing approaches—registration duplication, DNS cache poisoning, email header forgery—boosts campaign resilience and evasion against layered defenses.
As a foundational layer, email authentication weaknesses compound the threat, leading to the next section focused on the interplay of domain spoofing and phishing campaigns leveraging SPF, DKIM, and DMARC gaps.
How Phishing Leverages Domain Spoofing
Phishing campaigns hinge on the credibility bolstered through domain spoofing, masquerading as trusted entities to harvest credentials, deploy malware, or exfiltrate sensitive data. The attack lifecycle initiates with bulk registration of look-alike domains engineered through techniques such as visually deceptive character substitutions, homoglyph injections, and typosquatting variants that human recipients—or automated filters—find challenging to parse unaided.
Attackers may register domains like “paypa1.com” (using numeric ‘1’ to replace ‘l’) or “amaz0n.com” (zero instead of ‘o’), which avoid straightforward blacklist triggers yet achieve high click-through rates when embedded in phishing emails or malicious redirects.
After domain registration, attackers configure DNS to point spoofed domains to compromised or attacker-controlled hosting infrastructure serving counterfeit login portals, social engineering pages, or command-and-control endpoints. Concurrently, the attackers prepare email delivery infrastructure—authoritative mail servers or compromised SMTP relays—aligned with their spoofed domains to launch phishing campaigns.
The attack chain comprises domain registration → DNS delegation with authoritative name servers and MX records → email server provisioning with spoof domain identity → mass phishing email dissemination.
Attack success correlates strongly with the target organization’s email authentication posture. SPF, DKIM, and DMARC serve as layered defenses explicitly designed to validate sender legitimacy:
- SPF (Sender Policy Framework): Specifies authorized IPs allowed to send emails on a domain’s behalf via DNS TXT records. Lack of SPF or permissive records allow spoofed emails to bypass origin checks.
- DKIM (DomainKeys Identified Mail): Embeds cryptographic signatures ensuring email integrity and associating messages uniquely with sender domains. Absence or misconfiguration of DKIM lowers trustworthiness of message content.
- DMARC: Builds on SPF and DKIM outcomes to enforce domain-based alignment policies defining how receivers handle unauthenticated mail and collect forensic reports.
Domains with missing or incomplete SPF, DKIM, or DMARC settings become prime vectors for attacker exploitation, as messages from spoofed domains bypass filters and land in inboxes unchecked.
The 2020 Nobelium campaign illustrates this vulnerability. Attackers exploited organizations’ incomplete SPF/DKIM configurations to send emails impersonating Microsoft support, hijacking organizational trust and increasing credential theft efficacy. Similarly, financial institutions with lax DMARC enforcement have faced repeated spoofing attempts that bypass domain verification measures.
Partial misconfigurations introduce nuanced failure modes. For example, SPF records excluding legitimate third-party senders cause authentic messages to fail checks, potentially desensitizing downstream filters and users to failures, ironically enabling spoofed emails to slip through.
Therefore, phishing exploits centered on domain spoofing reveal how attackers manipulate DNS and email protocol deficiencies to circumvent security layers, underscoring the necessity of integrated defenses combining domain validation, cryptographic authentication, and real-time monitoring.
Given this tight coupling of domain spoofing and phishing, it becomes essential to understand how domain hijacking and squatting augment this threat landscape to form more persistent and evasive attacker infrastructures.
Interplay Between Domain Hijacking, Squatting, and Spoofing
Domain spoofing rarely operates in isolation; attackers often entangle it with domain hijacking and squatting tactics to complicate detection, attribution, and takedown efforts, generating resilient malicious ecosystems.
Domain Hijacking occurs when attackers gain unauthorized control over authentic, registered domains by exploiting weaknesses in registrar account security, engaging in social engineering, credential theft, or leveraging registrar policy loopholes. Control over the bona fide domain enables attackers to conduct spoofing campaigns while bypassing heuristic detection that targets look-alike domains, as emails, TLS certificates, and web traffic emanate from legitimate sources.
For backend services, domain hijacking can lead to persistent man-in-the-middle attacks or API endpoint fraud disguised under authorized certificates, significantly raising the bar for defenders.
Domain Squatting involves proactive registration of myriad domain variants incorporating typographical errors, homoglyphs, or domain suffix alterations in anticipation of user typos or security scanner false negatives. This reservoir of squatted domains facilitates flexible spoofing campaigns by cycling domains to evade blacklists and takedowns.
For high-scale distributed systems or data pipelines, squatting introduces risks where automated service integrations may resolve or fetch resources erroneously from spoofed domains, leading to data leaks or pipeline contamination.
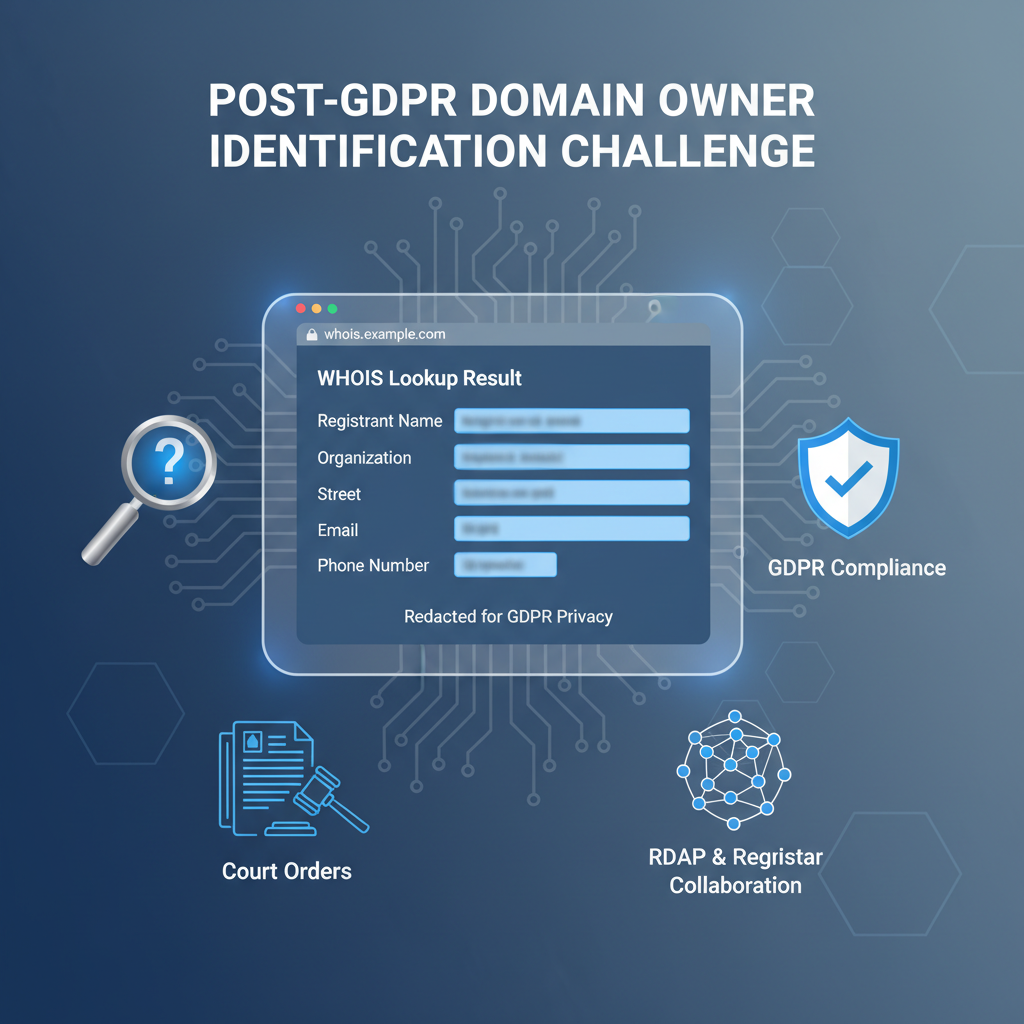
WHOIS data analysis remains a cornerstone for forensic investigation but faces limitations:
- Ambiguity and Obfuscation: Registrant details are frequently falsified or incomplete. Attackers use generic or privacy-protected registrant information, limiting meaningful attribution.
- Privacy Compliance: GDPR and related laws mandate extensive redaction, restricting WHOIS accessibility, increasing the challenge of ownership verification.
- Registrar Data Quality Variance: Disparities in WHOIS data standards across registrars hamstring automated correlation efforts.
To overcome these, defenders deploy correlation heuristics analyzing registrant contacts, DNS hosting IP ranges, domain registration timestamps, and payment metadata to cluster suspicious domains linked to threat actors.
Tools like dnstwist augment this by generating exhaustive domain permutations to preemptively identify squatted or typosquatted domains enabling proactive takedown or blocking.
In complex API integrations and multi-cloud deployments, coordinating WHOIS data with DNS infrastructure and traffic pattern monitoring forms the backbone of adaptive brand protection strategies.
Thus, the triad of domain spoofing, hijacking, and squatting constitutes a dynamically evolving attacker ecosystem, requiring integrated monitoring frameworks spanning WHOIS, DNS, infrastructure telemetry, and incident response.
Detection Strategies for Domain Spoofing
Leveraging WHOIS Data and Domain Registration Analysis
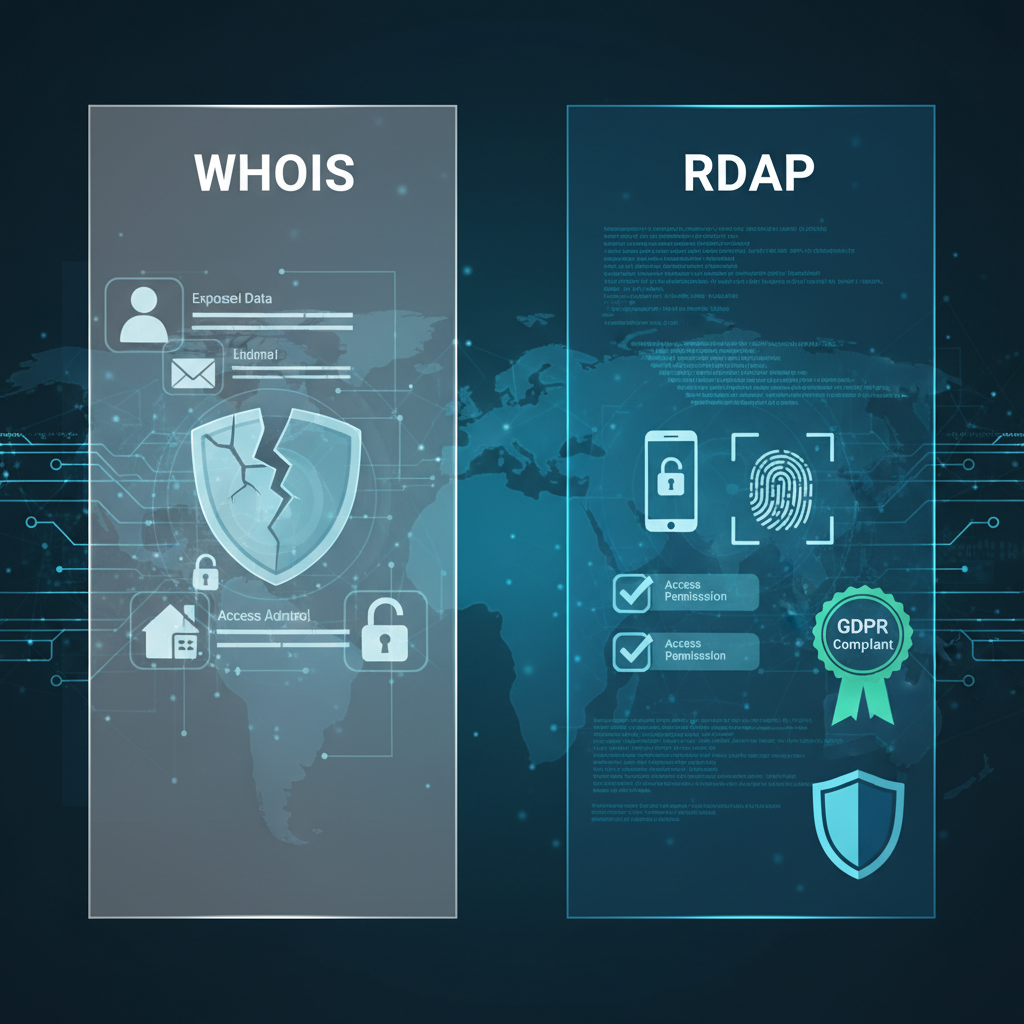
Effective domain spoofing detection initiates with comprehensive analysis of domain registration metadata harvested via the WHOIS protocol. Despite being one of the earliest data sources for registrant information, WHOIS is increasingly constrained by privacy laws like GDPR and the proliferation of privacy protection proxies masking registrant details. Nevertheless, subtle patterns within WHOIS datasets remain valuable for spotting clusters of spoofing domains.
Correlations among registrant fields—e.g., similar or configurable contact emails with minor letter substitutions (such as ‘@example.com’ to ‘@examp1e.com’)—unveil bulk domain registrations characteristic of phishing infrastructures. Similarly, tracking domain registration dates, expiry patterns, and registrar transfer histories reveals operational tactics such as batch registrations or frequent domain transfers designed to mask attacker footprints.
Security teams must grapple with heterogenous query interfaces, rate limits, response schemas, and the variable reliability of registrar WHOIS APIs, necessitating adaptive data scraping infrastructures or subscription services providing consolidated metadata. Automation is critical, especially when attackers generate thousands of spoof variants daily.
Besides WHOIS, DNS record analysis supplements detection by revealing configuration inconsistencies such as mismatched A records, irregular MX hosts, or unexpected TXT entries (including missing or malformed SPF/DKIM data). These anomalies often flag impostor domains masquerading using legitimate branding artifacts.
While useful, WHOIS analysis is insufficient alone due to high volumes of legitimate domain registrations and deliberate obfuscation by malicious actors. Detection effectiveness improves substantially when WHOIS insights integrate with DNS record validation, domain similarity scoring algorithms, and machine learning models that consider multi-dimensional inputs.
Operational constraints such as registrar query rate throttling, data freshness, and inconsistent coverage affect detection latency, potentially allowing spoofing domains to remain active for extended windows. Therefore, defenders must implement caching strategies and prioritize high-risk monitoring based on observed brand threat profiles and historical abuse patterns.
Technical practitioners aiming for robust implementations should consider contemporary protocols supplementing WHOIS, such as the Registration Data Access Protocol (RDAP), which offers structured, standardized, and machine-readable registration data, albeit with similar privacy-driven redactions.
Algorithmic and Heuristic Approaches to Detection
To augment WHOIS and registration analysis, algorithmic and heuristic methods systematically identify domains mimicking trusted brands via string similarity, structural mimicry, and contextual metadata evaluation. Generating permutations representing typosquatting, homoglyph substitutions, prefix/suffix additions, and keyboard proximity errors allows security teams to proactively identify suspicious domains prior to detected abuse.
Tools like dnstwist provide practical implementations of these techniques, employing transformations such as character swaps (“googel.com”), homograph character replacements (Latin ‘o’ with Cyrillic ‘о’), and insertion of semantic prefixes (e.g., “secure-paypal.com”). This comprehensive domain permutation generation exposes known threat vectors for preemptive investigation.
However, naive application leads to high false positive rates due to benign domains coincidentally resembling brands or competitors holding legitimate registrations. Integrating these algorithmic findings with curated threat intelligence blacklists—regularly updated feeds listing confirmed phishing and spoofing domains—prioritizes investigative focus and reduces unnecessary alert fatigue.
Advanced detection frameworks incorporate machine learning classifiers ingesting a multi-modal feature set, including domain age, WHOIS attributes, SSL/TLS certificate properties, IP address reputation, Autonomous System Number (ASN) correlations, and passive DNS data derivatives. For example, a newly registered domain exhibiting proxy WHOIS data, weak or mismatched SSL certificates, and co-hosting with known malicious domains signals heightened suspicion warranting prompt action.
Scaling these detection systems requires balancing exhaustive search with computation and alert cost. Exhaustive permutation space exploration may produce tens of thousands of candidate domains per brand, necessitating heuristic pruning, prioritized scanning based on risk heuristics, or focus on critical brand subsets.
Continuous rescanning accounts for the daily emergence of new spoof domains, while alert thresholds must be tuned to avoid operational overload.
Attackers adapt by migrating to new generic TLDs, evading legacy blacklists, employing fast-flux DNS to obfuscate hosting, or employing domain fronting tactics. Differentiating between registered domain spoofing and DNS response tampering (cache poisoning) remains critical, as each has distinct technical detection and response pathways.
In aggregate, an effective domain spoofing detection architecture fuses WHOIS and registration metadata, algorithmic similarity generation, blacklist intelligence, and heuristic or ML models into layered defenses. These systems must be continuously updated to stay resilient to evolving attacker tactics and maintain practical operational overhead.
Mitigation Techniques and Defensive Design Considerations
Configuring DNS and Email Authentication Protocols
Mitigating domain spoofing requires robust deployment and precise configuration of DNS and email authentication mechanisms, which enforce sender legitimacy, protect DNS data integrity, and constrain unauthorized domain use.
SPF Configuration Best Practices
Sender Policy Framework (SPF) records, published via DNS TXT entries, delineate which IP addresses and sending services are authorized to dispatch emails for a domain. Strict SPF policies (e.g., -all) reject unauthorized sends but risk false positives if legitimate third-party senders are omitted—common in ecosystems with multiple vendors sending on a domain’s behalf. Conversely, lax policies (~all or ?all) reduce impact of misconfigurations but expose domains to spoofing abuse.
Implementations should iteratively refine SPF to accurately reflect all legitimate mail sources, modularizing policies with includes and macros to accommodate evolving service architectures typical of distributed SaaS or microservice email flows. Regular audits prevent inadvertent opens that could be exploited via SPF bypass.
Failure modes include overly broad IP ranges or the deprecated +all modifier, which effectively disable SPF checks and invite spoofing attacks. Detailed understanding of cloud provider IP ranges, API gateways, and federated mail flows is necessary for comprehensive SPF policy design.
DKIM’s Cryptographic Signing and Key Management
DomainKeys Identified Mail (DKIM) attaches cryptographic signatures binding email header and body hashes to sender domains, verified using public keys published in DNS. This technique ensures message integrity and authenticity, establishing proof the message originated from the purported domain.
Effective DKIM deployment requires robust key management: key rotation strategies to mitigate exposure risk, selection of cryptographically secure key lengths (2048-bit minimum), and aligning domain signing with organizational sender policies. Complex multi-vendor environments demand careful coordination, as inconsistent signing or forwarding can break DKIM validation, complicating DMARC enforcement.
Operational challenges include DNS record propagation latency affecting key updates and key compromise recovery processes. Failure to address these leads to persistent spoofable vectors allowing attackers to counterfeit legitimate signatures.
DMARC as Unified Policy Framework
DMARC aggregates SPF and DKIM outcomes into a cohesive enforcement policy specifying recipient handling of unauthenticated emails via policies none, quarantine, or reject. Its alignment requirements ensure that the domain in the “From” header matches sender authentication domains, reducing deception through relaxed subdomain policies or third-party forwarding.
A phased rollout beginning with p=none enables collection and analysis of aggregated reports (RUA/RUF), revealing authentication failures and rogue senders without disrupting legitimate correspondence. Progression to stricter policies after thorough vetting minimizes business interruption while maximizing spoofing prevention.
Complexities arise in forwarded email workflows where SPF and DKIM authentication break, requiring interim solutions like ARC (Authenticated Received Chain) protocols, although these remain limited in adoption.
DMARC adoption gaps are often due to organizational inertia, lack of domain-wide policy coordination, or fears of mail disruption. Yet its enforcement significantly reduces spoofing-based phishing risks when consistently applied.
DNSSEC Deployment for DNS Integrity
To protect against DNS spoofing and cache poisoning, DNS Security Extensions (DNSSEC) digitally sign DNS zones, enabling recursive resolvers to verify authenticity and integrity of DNS data. DNSSEC deployment ensures that SPF, DKIM, and DMARC DNS records cannot be silently tampered with or forged.
DNSSEC implementation entails managing key signing keys (KSKs) and zone signing keys (ZSKs) with automated rollovers, as well as propagating DS records at the parent TLD levels. This process can be intricate and error-prone, especially across registrars with disparate DNSSEC support such as Namecheap or Hostinger. Misconfiguration may cause complete domain resolution failures, dramatically impacting service availability.
Despite initial deployment costs and operational complexity, DNSSEC remains foundational to closing gaps exploited in DNS cache poisoning or MITM attacks, reinforcing the entire domain authentication chain.
Common Misconceptions and Combined Enforcement
Relying on SPF or DKIM in isolation is insufficient to prevent domain spoofing. SPF validates sending IPs but can be circumvented by attackers using look-alike domains or header forgery; DKIM guarantees message integrity but depends on secure key management and consistent signing. DMARC integrates these with explicit domain alignment policies, forming a critical triad for comprehensive protection.
When domains are registered or managed via providers like Namecheap or Hostinger, pitfalls include slow DNS propagation, misconfigured TXT records, and incomplete reporting address setup resulting in ineffective DMARC feedback loops. Employing domain spoofing testing tools provides initial risk visibility but requires nuanced interpretation to minimize false positives and operational overhead.
Large-scale enterprises have demonstrated that iterative SPF and DKIM policy refinement paired with effective DMARC enforcement reduces spoofed phishing attempts by over 70% within a single year while decreasing false positive-induced operational disruptions.
Beyond foundational protocols, sustaining protection demands operational vigilance and monitoring for dynamic attacker shifts, framing the next discussion on continuous detection and blacklist management.
Operational Strategies Including Continuous Monitoring and Blacklist Management
The evolving and high-velocity nature of domain spoofing attacks necessitates persistent, automated operational monitoring to detect emerging spoofed and squatted domains targeting organizational brands.
Active Monitoring of Domain Registrations and Transfers
Continuous WHOIS and registry data harvesting enables detection of suspicious domain registration clusters based on shared registrant details, registration timings, or registrar behaviors. Tracking registrar transfer histories and domain lifecycle changes highlights attacker evasion strategies including bulk registrations and domain hopping.
This operational monitoring benefits from integration with internal threat intelligence platforms and automation pipelines providing early warnings before domains become active in attacks.
WHOIS Data Enhancements for Detection and Enforcement
Augmenting monitoring pipelines with WHOIS metadata enriches domain risk scoring models, capturing “low and slow” tactics where attackers register domains sporadically to avoid suspicion. Renewal and expiry pattern analysis aids in predicting domain resurrection attempts by adversaries, critical for sustained brand defense.
Combined with DNS anomaly detection—such as unusual zone record changes or inconsistent MX configurations—this approach has enabled security teams to reduce time-to-detection by approximately 40%, granting valuable lead time for takedown and mitigation efforts.
Challenges in Applying Domain Blacklists
While domain blacklists are powerful mitigative tools embedded within firewalls, mail filters, and endpoint protection stacks, their precision hinges on highly curated intelligence. Aggressive blacklisting mitigates spoof risk but introduces trade-offs including false positives impacting legitimate services, vendor partners, or subsidiaries.
Effective blacklist management requires continuous tuning informed by telemetry, incident trends, and user feedback. Excessively broad blacklists increase operational overhead and user friction, while conservative blacklists risk missing aggressive spoofing techniques.
Continuous Monitoring of DNS and Domain Lifecycle Events
Attackers often mobilize domain transfers or DNS zone modifications mid-campaign for redirection or infrastructure rotation. Zone change alerts, passive DNS monitoring, and transfer notifications form vital inputs for threat hunting platforms, letting security teams detect and respond to domain asset mobility.
Tracking domain migrations to cloud DNS providers like AWS Route 53 exposes potential ownership consolidations or evasive maneuvers, enabling proactive policy adjustments or blacklisting.
Integrating Threat Feeds into SOC Workflows
Leveraging integrated SIEM/SOAR capabilities, security operations centers synthesize blacklist updates, WHOIS alerts, and DNS anomalies to contextualize threat intelligence and accelerate incident response. Correlating domain registration spikes with mail flow abnormalities or end-user complaints reduces phishing incident impact by enabling rapid blocking or takedown.
Operational Vigilance Against Evolving Domain Spoofing Techniques
Attackers continuously evolve, adopting subtler homoglyph usages, multi-level subdomain obfuscation, or leveraging novel TLDs to circumvent detection. Operational teams must maintain expert differentiation across spoofing, hijacking, and squatting, applying distinct investigative and enforcement tactics accordingly.
- Hijacking requires forensic investigations and registrar cooperation for domain recovery.
- Squatting demands proactive domain variant registration and trademark enforcement.
- Spoofing mandates strict SPF/DKIM/DMARC policies coupled with real-time domain monitoring and automated response.
Together, this operational multi-layered defense maximizes resiliency against the ongoing challenges posed by agile adversaries exploiting domain infrastructure.
Key Takeaways
- Domain spoofing represents a significant security threat where attackers impersonate trusted domains through multiple techniques—including email and URL spoofing as well as typosquatting—leveraging brand trust to facilitate phishing and fraud. A deep technical understanding of DNS manipulation, domain registration tricks, and email authentication weaknesses is essential to architect scalable detection and defense systems.
- Understand DNS and email authentication protocols: Attackers exploit gaps in DNS records (SPF, DKIM, DMARC) and deceptive URL construction; rigorous configuration and monitoring of these protocols mitigate spoofing vectors in diverse infrastructure contexts, from API gateways to mail servers.
- Employ domain similarity algorithms to detect typosquatting: Automated tools like dnstwist generate domain permutations reflecting typo patterns and homoglyph substitutions, crucial for preemptive brand protection in registration data and traffic analysis.
- Utilize WHOIS data for attribution and clustering: Despite GDPR-driven redactions and data obfuscation, WHOIS metadata remains vital for linking related spoofing domains, necessitating augmentation with heuristic and anomaly detection techniques.
- Integrate dynamic threat intelligence blacklists: Continual updates and programmatic integration of blacklists into security stacks reduce false negatives, but require diligent tuning to balance operational feasibility and protection coverage.
- Manage domain registration and transfer intricacies: Migrations across popular registrars (e.g., Namecheap, Hostinger, Route 53) demand validation of registration locks and transfer policies to avoid opening spoofing or hijacking vectors mid-transition.
- Design detection systems accounting for domain hijacking and squatting overlaps: Spoofing often coexists with hijacking and squatting, necessitating correlated monitoring of DNS changes, WHOIS shifts, domain lifecycle events, and operational telemetry.
- Incorporate defenses against DNS spoofing: While registered domain spoofing is critical, DNS-level attacks like cache poisoning require DNSSEC deployment and recursive resolver hardening to protect resolution integrity.
- Prioritize proactive domain protection services: Automated renewal, unauthorized change monitoring, and registrar-level policies (as offered by providers like GoDaddy) reduce exposure though add vendor dependency and potential coverage gaps.
- Embed domain spoofing checks within CI/CD and monitoring ecosystems: Continuous verification of owned domains and monitoring for emergent spoof indicators reduce risk, necessitating API-based integration of domain spoofing detection tooling into development and operational workflows.
Comprehension of domain spoofing’s multifaceted nature—from registration subterfuge to DNS and email protocol exploits—equips engineers to architect nuanced detection and mitigation frameworks that safeguard brand reputation and user confidence at scale.
Conclusion
Domain spoofing epitomizes a complex, multifaceted challenge in modern system and security engineering, exploiting DNS infrastructure weaknesses, domain registration laxity, and envelope email authentication limitations to impersonate trusted entities. Distinguishing among the spectrum of spoofing modalities—including typosquatting, homoglyph attacks, DNS cache poisoning, and domain hijacking—is foundational to effective defense design.
Layered strategies combining comprehensive WHOIS and registration metadata analysis with algorithmic and heuristic similarity detection empower organizations to identify deceptive domains before operational impact peaks. Concurrently, rigorous deployment and ongoing management of SPF, DKIM, DMARC, and DNSSEC protocols fortify the protocol-level integrity underpinning trusted communication.
Yet, defensive success demands more than static control configurations; it requires continuous operational vigilance capturing domain lifecycle events, registrar transfers, DNS anomalies, and active threat intelligence integration capable of adapting to attacker pivots. Such dynamic detection and mitigation frameworks must acknowledge the complex interplay between protocol-level failures, infrastructural weaknesses, and user interaction vulnerabilities common to large distributed systems.
As organizations’ digital ecosystems scale and diversify—spanning multi-cloud environments, API integrations, and decentralized teams—the question evolves from whether domain spoofing attacks will occur to whether system architectures make spoofing visible, analyzable, and controllably mitigated under real operational pressures. This imperative shapes the engineering frontier of trust in connected digital infrastructures.