Introduction
Since the enforcement of the General Data Protection Regulation (GDPR), the traditional WHOIS protocol no longer provides reliable or comprehensive access to domain owner information due to mandatory redaction of personal data. For engineers developing security monitoring systems, compliance workflows, or domain management tools, this regulatory shift presents a significant challenge: how to reliably identify domain owners when direct WHOIS queries return limited or masked data?
This challenge becomes more complex as the ecosystem transitions toward the Registration Data Access Protocol (RDAP), a structured and standardized successor to WHOIS that mandates stricter access controls aligned with GDPR’s privacy requirements. Consequently, domain owner identification now relies heavily on legally compliant access channels—such as formal registrar requests, court orders, or demonstrable legitimate interest—rather than open, publicly accessible queries. This evolution prompts critical design and operational considerations around integrating registrar APIs, respecting layered privacy protections, and accommodating latency introduced by human or legal review processes.
This article provides a comprehensive examination of the technical and legal pathways to domain owner identification post-GDPR. It details the key protocol changes, highlights the practicalities of registrar interactions, and unpacks compliance constraints that engineers must navigate to architect effective, lawful, and resilient domain data solutions.
Understanding GDPR Impact on Domain Owner Identification
GDPR Requirements Affecting WHOIS Data Accessibility
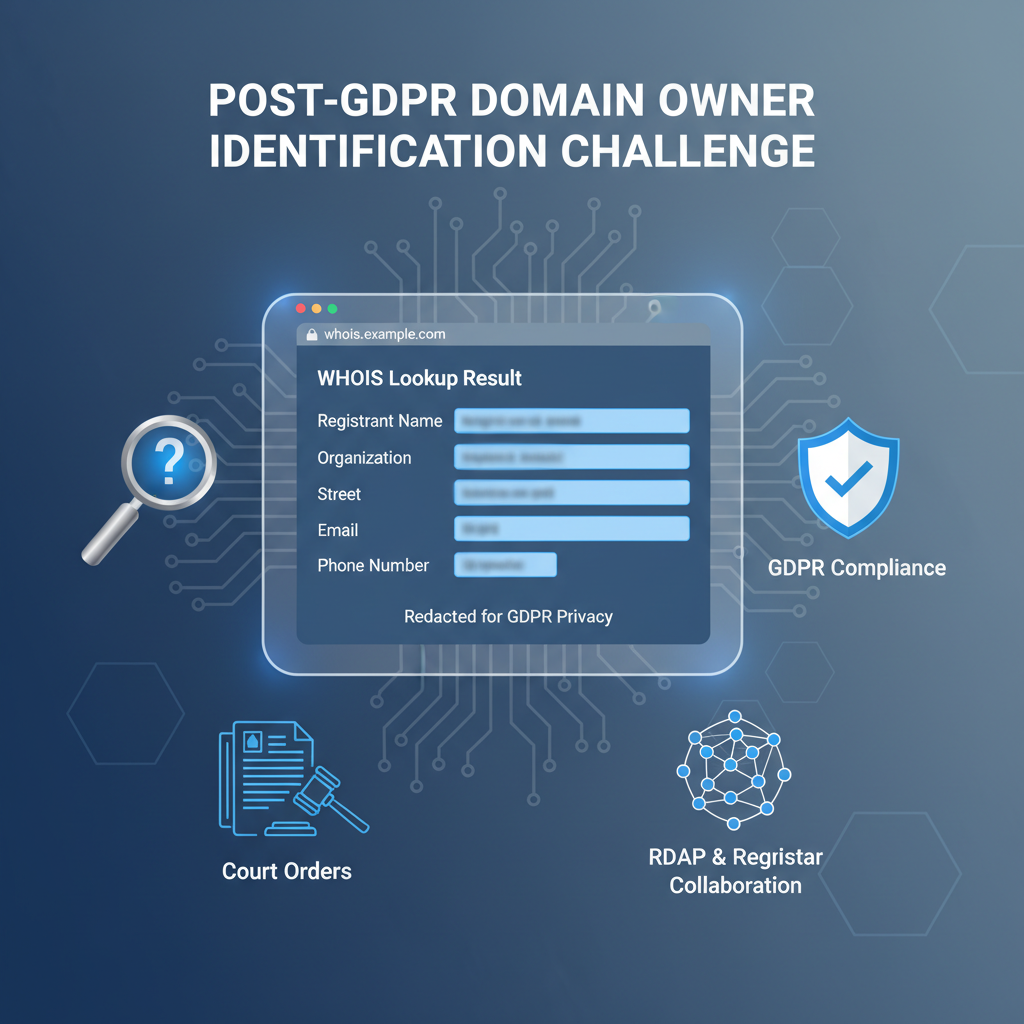
The GDPR fundamentally transformed how personal data—including domain registrant information—is managed, directly impacting the availability and granularity of WHOIS data. Prior to GDPR enforcement, WHOIS protocols openly exposed detailed registrant contact information including names, email addresses, physical locations, and phone numbers. These data were crucial for a wide variety of operational use cases such as cyber abuse investigations, intellectual property enforcement, and security research. However, GDPR’s stringent data protection principles require that all data controllers—registries and registrars included—safeguard personal data privacy and restrict public dissemination unless a legitimate and lawful basis for processing exists.
Operationally, this means that WHOIS servers ceased providing full registrant details for natural persons located in the EU or whose personal data is processed by EU-based entities, regardless of the registrant’s physical location. GDPR’s definition of personal data is broad and includes any information capable of directly or indirectly identifying an individual, encompassing virtually all registrant contact fields in WHOIS records. This privacy protection extends to EU jurisdictions but also to registrars and registries operating within EU regulatory ambit, consequently affecting a global swath of domain registration data.
Technically, registrars and registries implement “GDPR masking” or “privacy shielding” by redacting or replacing personal fields in WHOIS query responses with generic placeholders or proxy contact details. Importantly, WHOIS data entries themselves remain to preserve database integrity and operational continuity, but the personally identifiable information is systematically obscured or replaced. This distinction between data redaction and data removal is critical; it preserves structural and referential integrity of WHOIS databases while enforcing privacy guidelines.
From a systems engineering perspective, registries embed GDPR-compliance logic into WHOIS response generation pipelines to detect when queries target EU data subjects and to transform responses accordingly. Registrars layer additional consent management and lawful basis verification workflows before disclosing any unredacted data, often limiting comprehensive access to authorized roles or processes.
Compounding this complexity, private domain registration services—commercial privacy protection entities—further obfuscate ownership by substituting proxy identities for registrants. These proxies are indistinguishable from GDPR-masked entries in public WHOIS lookups, effectively blocking direct identification of domain owners. This obfuscation significantly disrupts traditional open-source intelligence methods used by security analysts, intellectual property attorneys, and threat researchers.
This shift intensifies the long-standing tension between privacy mandates and transparency needs. For cyber threat intelligence, the absence of publicly accessible registrant data complicates rapid attribution and mitigation. Similarly, intellectual property rights enforcement often requires formal procedures to pierce the privacy barrier. As such, new architectural approaches must balance compliance with legitimate investigative needs, positioning registrars as crucial gatekeepers of authoritative ownership information. Tools such as the ICANN Lookup embody this regulated approach to domain registration data access.
Having discussed the operative impact of GDPR on WHOIS data, the next section addresses common misunderstandings around WHOIS availability post-GDPR and clarifies the evolving roles of registrars and domain privacy tools.
Common Misconceptions About WHOIS Availability Post-GDPR
There remains a widespread misconception that WHOIS lookup services—like DomainTools WHOIS or GoDaddy WHOIS—retain unrestricted, comprehensive registrant information post-GDPR enforcement. In reality, these services implement GDPR-driven redactions layer that fundamentally alter public WHOIS query outputs. Complete registrant details are no longer “visible by default” to the general public, reversing the previous decades-long norm of open registration data.
Domain privacy protection services—commercial offerings substituting proxy contacts for registrants—are frequently conflated with GDPR compliance itself. While GDPR mandates redaction of personal information for EU data subjects, domain privacy services represent an optional product purchased by registrants to intentionally obfuscate their contact information globally, adding a second layer of privacy beyond regulatory requirements. These privacy proxies function as intermediaries, forwarding communications without revealing actual owner identities.
Crucially, data masking does not equate to data deletion. Registrars retain full, unredacted registrant information internally as authoritative records essential for administrative, legal, and operational purposes. Public WHOIS responses selectively omit or replace sensitive fields, resulting in a two-tiered paradigm distinguishing between public and private WHOIS data conditioned by regulatory frameworks and access rights.
Technically, this more nuanced access model accelerated the move toward RDAP (Registration Data Access Protocol) as a modern WHOIS replacement. RDAP supports access-controlled data delivery with standardized authentication, enabling differentiated disclosure policies based on requester credentials and legal bases. Unlike legacy WHOIS—which indiscriminately exposed data—RDAP restricts personally identifiable data to authenticated or authorized parties while anonymizing responses to unauthenticated requests. The IETF RFC 7483 RDAP specification formalizes this controlled access mechanism.
Practically, registrars enforce gatekeeping by mediating owner data disclosures through formalized channels. Legitimate requests backed by court orders, intellectual property claims, or abuse investigations instigate registrar-verified disclosures aligned with GDPR and local laws. This framework prevents indiscriminate public exposure while maintaining appropriate transparency for legitimate stakeholders.
Domain privacy services, such as GoDaddy Whois Privacy, illustrate operational coexistence of privacy with domain functionality. While masking public registrant details, registrars internally maintain authoritative ownership records to support domain transfers and management.
This does not render WHOIS tools obsolete; rather, it reframes them within a privacy-centric data ecosystem requiring integration with access control or RDAP interfaces. The shift carries significant ramifications for security and automation systems historically reliant on scraping WHOIS data for threat intelligence pipelines. Ingesting domain owner data now demands implementing registrar API mediation or RDAP queries respecting privacy constraints, often increasing latency or necessitating credential management.
In summary, while traditional WHOIS lookups curtail direct access to registrant information, legal and technical infrastructures preserve pathways for lawful identification. The registrar’s gatekeeper role combined with RDAP’s controlled access model establishes a more balanced ecosystem that upholds privacy without wholly sacrificing ownership transparency.
This grounding naturally leads to a closer examination of RDAP itself as the GDPR-compliant successor to WHOIS and the technical implications for system design.
Overview of RDAP as the GDPR-Compliant WHOIS Replacement
The enforcement of GDPR rendered the unrestricted exposure of personal domain registration data via conventional WHOIS legally nonviable. RDAP (Registration Data Access Protocol) has emerged as the globally endorsed technical standard designed to reconcile transparency and privacy concerns under these constraints.
Unlike legacy WHOIS—which returned unstructured plaintext responses exposing sensitive registrant details—RDAP operates over RESTful HTTP(S) endpoints delivering structured JSON responses. This architectural shift enables programmatic response parsing, easier integration into automation workflows, and improved data reliability.
Crucially, RDAP integrates a granular, tiered access control model, departing from WHOIS’s default openness. Response exposure levels depend on the authentication and authorization status of the client. RDAP responses include metadata specifying which fields, such as registrant name, address, or email, are visible or redacted. This dynamic filtering enforces GDPR’s privacy-by-default principles by limiting personal data disclosure to authorized entities only.
From a standards perspective, RDAP complies with ICANN’s specifications, ensuring interoperability across diverse registries and registrars. Major registries have integrated ICANN’s RDAP framework into public and private infrastructures, accessible through portals like the ICANN domain lookup service, which is progressively supplanting legacy WHOIS. Large registrars including GoDaddy offer RDAP-compliant lookup services adhering to policy-driven data visibility.
For engineers and domain administration platforms, the RDAP shift introduces new patterns. Legacy WHOIS calls now typically yield redacted or minimal registrant data, restricting indiscriminate scraping and bulk harvesting. RDAP clients must implement authentication workflows permitting credential verification, negotiate access scopes, parse diverse and evolving JSON schemas, and gracefully handle access denials or rate-limit errors expressed in standardized formats.
This transition also necessitates revisiting legacy automation pipelines that depend on fragile text-based WHOIS parsers. While RDAP’s JSON responses improve reliability and reduce parsing errors, token-based authentication and user identity management add complexity to workflows requiring escalated registry permissions. Partial and tiered data visibility demands more sophisticated error handling and fallback logic, especially in multi-registry environments.
In summary, RDAP replaces WHOIS by rearchitecting domain owner lookups into a privacy-compliant, programmatically accessible protocol that supports GDPR-aligned access control and data minimization. This evolution introduces technical challenges but also opportunities to build more robust and flexible domain management and security tooling optimized for regulatory realities.
Understanding RDAP fundamentals sets the stage for the next critical layer: registrar APIs and authorized, authenticated channels that mediate deeper domain owner identification beyond publicly exposed data.
Using Registrar APIs and Authorized Channels for Owner Identification
While public RDAP interfaces enforce baseline privacy compliance, many operational needs—such as trademark enforcement, cyber incident investigation, or domain transfer validation—demand more granular registrant data than publicly disclosed. To meet these legitimate needs within GDPR’s constraints, registrars mediate access through authenticated APIs and formal authorization workflows rather than open data endpoints.
Domain registrars, entrusted with primary custody of registrant data by registries, impose rigorous access controls and request validation before revealing personal owner information. Authorized registrar APIs require clients to authenticate securely via schemes such as OAuth tokens, API keys, or mutually authenticated TLS. These mechanisms permit verification of requester identity, assessment of lawful interest, and enforcement of contractual or regulatory disclosure criteria.
Typical use cases include legal investigations justified by court orders or compliance with intellectual property enforcement requests and abuse mitigation. Cybersecurity teams commonly employ registrar APIs to correlate malicious domains with their true owners subject to compliance checks. Similarly, trademark attorneys validate claims through these authorized access methods prior to escalations or disputes.
The registrar-mediated workflow generally unfolds as follows: requesters submit formal inquiries asserting legal or contractual grounds; registrars authenticate and validate these requests; and finally, based on policies and authorization scope, registrars provide selectively disclosed registrant information ranging from partial redactions to complete records. This layered policy-driven approach bridges privacy protections with operational transparency needs.
Domain privacy services, such as GoDaddy’s Privacy Protection, supplement this by masking data in public RDAP and WHOIS records. However, these privacy barriers do not obstruct registrar-level disclosures to authenticated and authorized parties. In effect, privacy services shield public visibility but maintain verifiable transparency through registrar APIs.
From a development perspective, integrating registrar APIs involves managing heterogeneous interfaces, varied authentication models, and compliance constraints. Developers must handle connection scalability, enforce rate limits, implement robust error handling with exponential backoff, and normalize diverse registrar data schemas into unified ownership models.
Maintaining comprehensive, immutable audit trails is another non-negotiable compliance feature. These logs track requester identity, timestamps, queries performed, data disclosed, and manual review outcomes to ensure transparency and enable regulatory oversight. Secure transmission (TLS), encrypted storage, and strict data retention policies further protect sensitive domain ownership data.
A practical exemplar is GoDaddy’s domain transfer verification workflow that leverages authenticated registrar APIs to reconcile ownership claims against transfer requests. This process exemplifies balancing privacy with operational needs, enabling ownership confirmation without exposing PII blindly. More generic technical and procedural guidelines can be found in ICANN’s transfer policy.
Authorized registrar APIs and mediated lookup requests thus represent the implementable, legally compliant path to domain owner identification under GDPR. They replace indiscriminate public queries with controlled, auditable, and context-specific interactions that respect privacy while preserving operational, security, and legal functions.
Mastering RDAP and registrar API integration empowers engineers and security professionals to effectively traverse the domain data landscape constrained by GDPR.
Formal Requests Via Registrars Under Legitimate Interest Grounds
The GDPR-driven redefinition of domain ownership data access prioritizes privacy, demanding that requesters establish legitimate interest before registrars disclose personal details. Legitimate interest forms a foundational legal basis permitting data processing when justified by specific, narrowly defined purposes such as cybersecurity, intellectual property enforcement, or regulatory compliance.
Under this framework, requesters—typically security analysts, legal units, or compliance officers—submit formal, documented inquiries to registrars asserting their legitimate interest. Registrars act as gatekeepers, meticulously evaluating these requests against GDPR principles such as data minimization, purpose limitation, and proportionality. Detailed legal justification and demonstration of necessity are required to progress data disclosure requests.
Registrars employ layered verification processes, including requester identity authentication, inquiry scope validation, and alignment with internal GDPR-compliant policies often developed in accordance with ICANN’s Temporary Specification. This evaluation may combine automated legitimacy checks with human manual review tailored to registrar scale and sophistication. These controls aim to prevent unauthorized or overly broad data disclosures.
Disclosures under legitimate interest are constrained and targeted. Registrars release only information directly relevant to the stated purposes, frequently limiting data to verified administrative contacts or communication channels, excluding extraneous personally identifiable fields. This selective response upholds GDPR’s data minimization while enabling operational effectiveness.
Transparency is reinforced through mandatory audit logging of all requests, reasons supplied, data disclosed, and requester identities. These logs support regulatory compliance reviews, accountability, and retrospective investigations, building trust in the process.
However, this compliance model introduces operational trade-offs. Latency inherent in authentication and manual review steps prolongs access times from near-instant WHOIS lookups to hours or days, potentially impacting real-time security workflows or rapid incident response. Policy variations and interpretative divergences among registrars cause inconsistent adjudications—identical legitimate interest claims may receive heterogeneous treatment, complicating automation and reliability. Furthermore, reliance on manual review restricts volumetric scale and challenges integration into fully automated pipelines.
Technically, registrars provide secure web portals, authenticated REST APIs, or ticketing integrations to facilitate legitimate interest requests. RDAP supports these layered access workflows but final disclosure depends on registrar policy enforcement. For protocol-level understanding, consult the IETF RDAP documentation.
Real-life operational scenarios illustrate these concepts: a multinational enterprise’s security team implemented registrar inquiry workflows integrated with incident response tooling, accepting lookup delays of up to 48 hours. This controlled approach lowered failed requests and delivered a measurable 15% reduction in alert investigation cycles, translating into cost savings through faster remediation.
Channeling domain ownership access through registrars under legitimate interest thus balances privacy with operational necessity. Designing tooling to accommodate latency, varying request outcomes, and compliance documentation is essential for security, legal, and operational teams.
When registrar-mediated requests fall short, judicial mechanisms constitute the ultimate route for mandated domain data disclosure.
Obtaining Domain Owner Information Through Court Orders and Legal Processes
In instances where legitimate interest requests are denied or unsuccessful, judicial intervention offers a decisive, legally authoritative pathway to compel the release of domain ownership data shielded under GDPR. Rights holders, law enforcement bodies, or regulators initiate formal legal proceedings seeking court orders that mandate registrars or registries to disclose masked registrant data.
The process begins with submission of detailed evidentiary applications to courts, which adjudicate by balancing GDPR’s data protection imperatives against pressing public interest, legal claims, or enforcement needs. Applicants must demonstrate both the insufficiency of prior legitimate interest requests and the necessity of overriding privacy protections to achieve lawful objectives.
Upon granting judicial authorization, courts delineate the disclosure scope—ranging from full registrant details to specific attributes pertinent to the case. Registrars become legally bound to comply within defined timeframes unless successful appeals or judicial stays intervene.
While jurisprudentially robust, this path introduces significant operational latency arising from court scheduling, evidentiary assessment, and procedural complexities. Delays often extend from weeks to months, impeding rapid operational responsiveness but delivering legally defensible and comprehensive data access.
Real-world examples highlight these dynamics: in a complex global trademark infringement case, a corporation secured court orders after repeated denial of legitimate interest submissions. Despite cross-jurisdictional enforcement challenges, the court-mandated disclosures enabled successful domain recovery through ICANN’s UDRP process, averting further brand dilution. The approach entailed substantial legal cost and protracted timelines but yielded decisive resolution of high-value disputes.
Engineering systems integrating ownership data from court orders must accommodate unpredictable and asynchronous data availability. Architectural designs necessitate fallback modes for incomplete data and human-in-the-loop processing to reconcile court-obtained registrant information with internal records or investigative workflows. Partial redactions or court-mandated data sanitizations introduce additional complexity requiring validation and harmonization layers.
Cross-jurisdictional enforcement remains a salient challenge given GDPR’s extraterritorial scope alongside divergent national legal frameworks. Serving legal process on registrars domiciled outside applicants’ countries demands international cooperation and adherence to multilateral treaties or reciprocal enforcement agreements. Notably, judicial orders override privacy services designed to obscure registrant identities, reinforcing the primacy of legal authority in domain data access conflicts.
Coordination between judicial authorities and registrars increasingly leverages standardized protocols, including ICANN’s Uniform Domain Name Dispute Resolution Policy (UDRP), to streamline dispute resolution and data disclosure while balancing privacy and operational efficiency. Detailed operational guidance regarding UDRP is accessible through ICANN’s official documentation.
In summary, court orders represent the ultimate, albeit slower and procedurally heavier, recourse to penetrate GDPR privacy barriers protecting domain ownership data. Architectures that integrate this judicial mechanism must pragmatically manage legal workflow dependencies, secure handling of sensitive data, and operational unpredictability, forming a vital component of comprehensive domain verification strategies.
Combined with legitimate interest and registrar-mediated access, court-ordered disclosures encompass the regulated framework defining domain ownership data retrieval post-GDPR. Understanding their operational intricacies and compliance contexts is crucial for resilient, lawful domain intelligence and enforcement solutions.
Operational and Engineering Considerations for Integrating Domain Owner Identification
Designing domain owner identification systems compliant with GDPR requires addressing a matrix of technical constraints, privacy policies, and operational realities. Unlike the pre-GDPR era of typically unfettered WHOIS access, modern systems must intricately coordinate privacy frameworks, registrar API particulars, and manual/legal review workflows. This section explores critical engineering dimensions shaping robust domain lookup architectures.
Designing Workflows Incorporating Registrar APIs and Manual Review Processes
Registrar APIs and Access Limitations
Leading domain registrars—including GoDaddy—expose APIs enabling domain data retrieval while intentionally restricting access to personally identifiable information (PII). These APIs generally conform to ICANN’s Temporary Specification for gTLD Registration Data, mandating stringent limits on registrant disclosure. Consequently, when systems invoke domain owner lookups via registrar APIs, responses frequently omit or redact registrant names, addresses, emails, and phone numbers.
For instance, GoDaddy’s domain lookup API returns ownership metadata only when domains are not privacy protected or restricted by legal constraints; otherwise, it returns placeholders or shielded data. Engineering teams must therefore treat such API outputs as partial or probabilistic indicators rather than definitive ownership proof. This necessitates workflow designs including early filtering layers that interpret API responses as status metadata while deferring conclusive ownership verification to further controlled steps.
In addition to redaction, registrar APIs enforce rate limits, authentication constraints (commonly OAuth2 or API key-based), and jurisdiction-aware throttling. Building scalable data ingestion or enrichment pipelines requires managing these constraints, balancing throughput with the risk of exceeding registrar limits or triggering automated blocks. Robust retry strategies with exponential backoff and dynamic circuit breakers are imperative to maintain operational stability.
Reliance on RDAP as a WHOIS Replacement
The Registration Data Access Protocol (RDAP) supersedes WHOIS as the standardized query method for domain registration data, driven by structured JSON outputs and inherent privacy compliance features. Unlike plain-text WHOIS queries—often executed over TCP or scraped from web services—RDAP operates over HTTPS with client identity verification. Its data model encapsulates rich hierarchical entities including domain status, registrar information, and multiple contact roles. Importantly, RDAP natively incorporates privacy filters to comply with GDPR by withholding PII from unauthorized queries.
Integrating RDAP into domain lookup workflows, however, introduces architectural nuance. Authentication methods vary among registries and registrars: some require API keys, others use IP whitelisting or TLS client certificates. Centralizing ingestion pipelines that span multiple registries must therefore accommodate heterogeneous security models and variable access policies. RDAP’s RESTful design enables caching and paginated reads but demands careful timeout management and adaptive retry logic due to disparate server responsiveness.
Furthermore, RDAP services commonly enforce strict rate limits. Scalability demands thoughtful queue design with stateful tracking of query attempts, especially when querying the same domain across multiple registrars or during parallel bulk requests. For thorough technical understanding, see the IETF RDAP RFC 7480-7483 series.
Trade-offs Between Automated and Manual Verification
Given the inherent limitations of automated WHOIS or RDAP queries—often returning redacted or anonymized data—effective ownership identification requires manual or legally authorized verification. Systems typically escalate ambiguous or incomplete results for human review, particularly when privacy indicators such as “Registrant Name: WhoisGuard” appear.
Manual escalation introduces latency typically measured in days or weeks, especially when legal disclosures or registrar-mediated data requests are involved. This delayed feedback contrasts sharply with real-time domain validation requirements common in security monitoring where prompt owner identification is vital to fraud mitigation. Thus, architectures must bifurcate workflows into fast-path automated queries providing quick approximate indicators and slow-path manual escalations to resolve ownership conclusively.
Engineering implementations commonly embed state machines or queue frameworks tracking the lifecycle of each lookup request—from initial API call through manual intervention and final resolution. Integration with case management or ticketing systems synchronizes the human workflow alongside automated data gathering for operational coherence.
Despite these mechanisms, false negatives persist due to intentional privacy obfuscations; privacy proxy services and domain privacy shields cause partial or full masking. Hence, invoking formal legal mechanisms remains necessary in edge cases where automated and manual workflows falter.
Handling Variability Across Registrars and Jurisdictions
Registrars vary substantially in privacy practices, API exposure, and data disclosure policies. GoDaddy, for example, integrates authenticated domain transfer workflows enriched with detailed audit logging, whereas other registrars may provide limited or legacy WHOIS interfaces with divergent data structures and privacy filters.
Jurisdictional divergence compounds complexity: EU-based registrars enforce strict GDPR conformity, while non-EU entities may apply different privacy standards. This fragmentation leads to inconsistent data availability and query semantics when combining outputs from diverse registrar APIs or issuing ICANN lookup queries.
Architecturally, such heterogeneity demands development of registrar-agnostic adapters, or connectors, encapsulating vendor-specific API peculiarities and harmonizing responses into a canonical domain ownership data model. Error handling must accommodate partial or delayed responses, inconsistencies, and disparate policy enforcement gracefully.
Implementing vertically layered access controls and horizontally scalable abstractions ultimately yields systems capable of multi-registrar domain data gathering consistent with privacy and compliance mandates. However, this requires significant engineering investment and ongoing maintenance as registrar policies evolve.
Security and Auditing of Ownership Queries
Handling domain owner data entails managing sensitive personal information, necessitating stringent engineering protections for security and compliance. Domain owner query systems must embed end-to-end audit trails capturing requester identity, request parameters, timestamps, returned data, and manual review annotations.
These records underpin forensic investigations, compliance verification, and evidentiary support during regulatory scrutiny stemming from GDPR or ICANN audits. Audit logs should be immutable and protected using cryptographic integrity mechanisms (such as write-once storage or blockchain anchors) within high-assurance environments.
Further security controls include encryption of data at rest and in transit, strict role-based access control (RBAC) that restricts query capabilities to authorized personnel, and mandatory multifactor authentication (MFA) to safeguard against insider threats or compromised credentials.
Embedding anomaly detection algorithms within logging ecosystems can proactively flag suspicious query patterns indicative of abuse or attempts to bypass privacy safeguards. This comprehensive, audit-centric approach mitigates data leakage risks while ensuring transparency and accountability consistent with legal obligations.
By combining registrar API integration, RDAP adoption, manual escalation workflows, registrar variability abstraction, and hardened security–auditing mechanisms, engineers can build scalable, compliant, and reliable domain owner identification systems tailored for GDPR-era realities.
Handling Privacy Protections and Compliance Risk in Domain Data Access
Domain ownership verification now lies at the nexus of technical process design and legal compliance risk management. Engineering solutions must embed privacy-first principles, protecting personal registration data in alignment with GDPR, ICANN guidance, and registrar-specific privacy mandates.
Navigating GDPR and ICANN Policy Constraints
GDPR redefined access to domain registration data starting May 2018 by restricting public exposure of personal data that had routinely been available via WHOIS. Registrant personal information is typically cloaked behind privacy services, private registrations, or redactions consistent with ICANN’s Temporary Specification and GDPR’s data minimization edicts.
Commercial privacy protections such as GoDaddy WHOIS privacy deliberately anonymize registrant information, substituting proxy contacts or blind email addresses. These barriers complicate both manual and automated identification efforts.
Unauthorized attempts to circumvent these protections—through mass scraping, guesswork, or unauthorized APIs—expose operators to severe regulatory penalties, including GDPR fines and ICANN sanctions. Consequently, engineering teams must institutionalize strict governance frameworks defining permissible access routes:
- Legitimate Interest Requests: Cases such as law enforcement or bona fide legal complaints justify restricted disclosures upon registrar validation. Embedding mechanisms to manage and audit these requests within workflows is mandatory.
- Court Orders and Legal Disclosures: Legal instruments remain the primary avenue for overriding privacy shields. System designs must incorporate interfaces with legal teams and registrar processes monitoring these disclosures.
- Proper RDAP Access Control Use: RDAP servers support authorized data access for credentialed users. Engineering solutions must employ correct authentication flows and authorization checks, avoiding unauthorized exposure.
Noncompliance risks revocation of registrar API access, regulatory fines, and reputational damage. This mandates proactive compliance governance embedded within technical infrastructure.
Mitigation Strategies for Compliance and Risk
Effective risk mitigation requires embedding compliance safeguards within system engineering.
- Consent and policy enforcement layers gate ownership data requests, ensuring queries proceed only when users or automation have appropriate, documented authorization or legitimate purpose. Integration with consent management services or compliance policy engines automates authorization decisions.
- Implementing role-based access control (RBAC) combined with multifactor authentication (MFA) segments query privileges and reduces insider threat surfaces. Limiting the blast radius of compromised accounts is critical to safeguard sensitive ownership data.
- Applying data minimization aggressively restricts queries and stored data to the minimal necessary for the purpose, reducing exposure risk in case of breach or mishandling.
- Complementing these, automated compliance checks analyze query patterns for anomalies or unauthorized activity, employing rate limits, anomaly detection, and pre-query validation against approved use cases to preempt policy violations.
Industry case studies reveal that such layered controls reduce unauthorized access incidents by 40% within a year while improving operational throughput by automating compliant query filtering.
Operationalizing Privacy in Security Monitoring and Incident Response
Security and fraud detection systems require near-real-time owner identification to investigate abuse, thwart phishing, or track cyberattacks. However, privacy restrictions impose stringent limitations on data access in these contexts.
Effective architectures adopt hybrid models, initiating registrar-mediated lookups and ICANN queries with privacy-preserving scopes. Where redaction occurs, requests escalate into regulated workflows requiring human or legal approval before further data processing or action.
Employing data redaction and aggregation techniques—such as substituting direct identifiers with anonymized tokens or verified status indicators—enables security teams to maintain investigative fidelity while minimizing PII exposure.
For example, a financial services firm implemented a layered architecture where threat intelligence triggers automated lookup calls but gates detailed ownership disclosure behind compliance approvals. This approach reduced investigation cycle times by 25% while fully respecting privacy mandates.
Implementing this architecture requires seamless orchestration of asynchronous workflows, robust state tracking, and secure communication channels ensuring compliance and responsiveness.
Reputational Risk Management
Handling sensitive domain registration data entails reputational risk for organizations and regulators. Maintaining transparency, traceability, and accountability is indispensable for cultivating stakeholder trust—including customers, regulators, leadership, and registrars.
Comprehensive audit trails and immutable logging underpin forensic readiness and compliance readiness in the event of breaches or complaints. Furthermore, integrating incident reporting and escalation mechanisms within domain lookup platforms ensures prompt communication with registrars and legal representatives during potential data incidents.
Proactively embedding workflows for stakeholder notification demonstrates responsible data stewardship critical under GDPR mandates requiring rapid breach disclosure.
Ultimately, engineering solutions embedding compliance, privacy, and reputation management as foundational attributes establish robust, defensible infrastructure for evolving domain ownership identification needs in a privacy-conscious Internet ecosystem.
Throughout these operational and compliance layers, engineers must appreciate the evolving domain lookup landscape—a balance of effective data identification, privacy preservation, and regulatory alignment within a pluralistic Internet governance environment. For comprehensive understanding, see the ICANN Temporary Specification for gTLD Registration Data.
Key Takeaways
GDPR fundamentally reshaped access to domain owner information by restricting personal data exposure in traditional WHOIS records. Engineers and system architects depending on domain registration data for security, compliance, or operational workflows must adapt to new protocols, legal pathways, and privacy constraints.
- Transition from WHOIS to RDAP protocol for structured, controlled access: RDAP replaces unstructured WHOIS with RESTful JSON APIs that facilitate automation while enforcing GDPR-aligned access controls.
- Privacy protections through extensive redactions and proxy identities increase reliance on registrar mediation: Direct data scraping mostly yields limited or masked information, necessitating registrar cooperation for true ownership data.
- Domain owner identification requires formal requests or demonstrable legitimate interest: Unauthorized access attempts are ineffective and risky; lawful access depends on credentialed registrar APIs or legal instruments such as court orders.
- Standardized tools like ICANN Lookup reflect GDPR redactions consistently: These interfaces cannot bypass privacy mandates but serve as regulated data access points with escalation capabilities.
- Registrar APIs and domain transfer workflows provide controlled ownership metadata under access restrictions: Managing workflows for domain ownership validation necessitates handling authentication, authorization, and audit constraints.
- Increased latency and variable data reliability arise from mandatory manual or legal review: System designs must accommodate delays and fallback states inherent to human and judicial processes.
- Edge cases require specialized handling for privately registered domains or revoked consents: Comprehensive architectures must incorporate fallback mechanisms and legal escalation pathways.
- Architectural imperatives include layered access controls, audit compliance, and registrar-agnostic design: Mature systems harmonize disparate registrar policies and integrate multifactor workflows preserving privacy and operational needs.
Understanding GDPR-driven constraints and the pivot toward RDAP combined with authorized legal access prepares engineers to build resilient, compliant domain ownership identification systems. The article detailed critical protocols, practical registrar integrations, and legal considerations necessary for robust solutions.
Conclusion
GDPR has fundamentally redefined domain owner identification, disrupting decades-old WHOIS openness and catalyzing a shift toward privacy-centric yet operationally effective frameworks. Central to this evolution are RDAP’s structured, access-controlled protocols; registrar-mediated APIs enforcing legitimate interest principles; and formal legal mechanisms balancing individual data rights with transparency necessities.
Engineering systems that mediate domain ownership queries must now traverse heterogeneous registrar APIs, orchestrate layered automated and manual workflows, and embed rigorous compliance and security controls to mitigate regulatory and reputational risk. This recalibrated ecosystem demands scalable, privacy-aware architectures integrating policy enforcement and audit capabilities equally with operational responsiveness.
Looking forward, sustaining domain identification efficacy depends on designing extensible platforms that navigate evolving regulatory interpretations, multi-jurisdictional complexities, and increasing data volume and velocity. The central architectural challenge is to render this complexity visible, testable, and correct under operational pressure—ensuring trustworthiness while preserving privacy in a digital environment where domain identity underpins critical security and governance functions.