Key Takeaways
WHOIS operates as a foundational yet intricate protocol ecosystem for domain registration metadata management, enabling controlled and transparent retrieval of domain ownership and registration details. Engineers integrating domain-related functionality must grasp the complex architectural layering of WHOIS—spanning ICANN’s policy governance, distributed registries maintaining authoritative zone data, and registrars directly managing registrant records—to design reliable systems for domain validation, security enforcement, network attribution, and lifecycle automation. This foundational understanding is crucial to mitigate inherent trade-offs involving data freshness, consistency, latency, privacy compliance, and structural heterogeneity characteristic of WHOIS infrastructure.
- Hierarchical WHOIS architecture necessitates coordinated operation among ICANN, Registries, and Registrars: ICANN defines and enforces overarching policy frameworks and accreditation standards; registries maintain top-level domain authoritative data and WHOIS service endpoints; registrars act as direct registrant interfaces. This multi-layered model imposes complex, asynchronous data synchronization and coordination challenges impacting the currency and reliability of WHOIS information.
- WHOIS data originates at domain registration and is stored across decentralized registries: Such decentralization inherently introduces propagation delays and eventual consistency phenomena, meaning WHOIS queries can return stale, incomplete, or conflicting data depending on update intervals and caching strategies.
- The WHOIS protocol operates over TCP port 43 using simple textual queries and responses: While this simplicity delivers universal accessibility, it yields unstructured, often inconsistent data formats with limited support for machine readability or live update notifications, constraining integration into event-driven or high-throughput domain management workflows.
- Public WHOIS data visibility is intensely shaped by privacy regulations like GDPR: Redaction, privacy shielding, or gated access enforce partial concealment of registrant personal information, impairing data completeness, complicating automated verification processes, and necessitating fallback heuristics or premium API services for full data access.
- Domain lifecycle events—expiry, lock/unlock status, transfer approvals—directly influence WHOIS record states: Systems monitoring these states must accommodate asynchronous updates, transient inconsistencies, and possible data gaps during rapid state transitions.
- Registrar and registry coordination governs domain transfers using authorization codes and domain locks reflected in WHOIS metadata: Automating these workflows requires precise synchronization across disparate WHOIS data sources and careful handling of propagation delays and security checks.
- WHOIS lookups supplement security operations such as IP-to-domain mapping, reputation scoring, and blacklist verification: However, reliance on redacted, stale, or heterogeneous WHOIS data can reduce visibility, accuracy, and responsiveness in threat intelligence pipelines.
- Scalable WHOIS integration demands strategies including caching, rate limiting, query prioritization, and fallback mechanisms: These approaches manage protocol rate limits, distributed system latency, and heterogeneous implementation behaviors to uphold system availability and data integrity in high-volume environments.
- Diverse WHOIS implementations across registries and top-level domains introduce data schema variability and access policy heterogeneity: Handling this complexity requires robust normalization, error handling, and reconciliation layers within tooling architectures.
- Integrating WHOIS with DNS and domain redirection data requires nuanced interpretation: Misattributing WHOIS ownership versus operational DNS delegation or redirection can lead to erroneous access control, security judgments, or routing decisions.
This comprehensive foundation prepares the reader to explore detailed technical workflows for domain registration, WHOIS data propagation, protocol interactions, and practical guidance for constructing reliable, legally compliant WHOIS integration in scalable domain management and security solutions.
Introduction
While WHOIS superficially appears as a straightforward directory service for domain ownership, its underlying architecture embodies a complex, distributed system orchestrated among ICANN, registries, and registrars. This ecosystem manages volatile, sensitive registration data under competing demands for transparency, privacy, and operational scalability, emerging as an indispensable source for domain validation, security enforcement, and network attribution.
Understanding WHOIS requires grappling with inherent trade-offs between data consistency, query limitations, and privacy-driven redactions that directly shape automation reliability and threat intelligence completeness. This article unpacks WHOIS’s end-to-end flow—from domain registration and decentralized data storage to querying protocols—highlighting key technical pitfalls and design considerations engineers must address when embedding WHOIS lookups within scalable domain management, security tooling, or infrastructure automation frameworks.
Fundamentals of How WHOIS Works
WHOIS is a specialized query protocol designed to reveal metadata associated with registered Internet domain names—including ownership, administrative contacts, billing information, and domain lifecycle states such as expiry and lock status. Its primary function is mapping domain names into registrant data elements that underpin domain accountability, validation, and abuse mitigation.
At a technical level, WHOIS queries are traditionally performed over TCP port 43 using a legacy plaintext protocol. Clients send simple ASCII queries, usually the domain name, and servers respond with freeform textual data encapsulating registration attributes. While lightweight and widely supported, this protocol suffers from lack of structured data and real-time notification mechanisms, requiring heuristic parsing and limiting integration into reactive or event-driven systems.
Architecturally, WHOIS is implemented atop a federated infrastructure with distinct roles:
- Registrants provide detailed identity, contact, and technical information via registrars.
- Registrars serve as direct intermediaries managing domain registrations, processing updates, and engaging with registrants.
- Registries operate authoritative databases at the TLD level, maintaining zone files and authoritative WHOIS server endpoints.
- ICANN governs policy, accreditation, and compliance standards, setting WHOIS service obligations while navigating privacy laws such as GDPR.
This multi-tier system guarantees data integrity by layering registrant input, registrar maintenance, registry validation, and ICANN policy oversight, though at the cost of asynchronous synchronization and data freshness challenges.
In practice, WHOIS data drives several critical use cases:
- Domain validation workflows: WHOIS underpins authentication of registrant identities and domain ownership verification during registration, transfer, or dispute escalation. For example, automated systems at registrars like Namecheap or Hostinger leverage WHOIS to validate ownership before enabling domain status changes or transfers.
- Security and abuse mitigation: WHOIS aids identification of malicious actors by revealing registrant patterns, domain status flags, and ownership histories. Security teams incorporate WHOIS alongside DNS and threat intelligence feeds to detect phishing domains, spam sources, and malware infrastructure. Correlating WHOIS data with real-time domain churn helps in rapid incident response. Recommended references include the DomainTools overview on WHOIS and security use cases.
- Network forensics: WHOIS supports infrastructure attribution by linking domain names to IP allocations and hosting entities. Analysts fuse WHOIS with BGP and DNS data to identify command-and-control infrastructure, trace attack vectors, or uncover resource reuse by threat actors.
Contrary to common oversimplification as just a “whois lookup” tool, WHOIS is a foundational distributed governance mechanism enabling global domain namespace accountability. Its protocol simplicity belies extensive ecosystem coordination, data accuracy enforcement, privacy compliance layers, and technical interoperability challenges. Functions like “domain expiry checker” or “domain blacklist check” rely on this distributed architecture, illustrating the practical complexities and engineering concerns involved.
Understanding these fundamentals leads naturally into examining the key administrative actors—ICANN, registries, and registrars—whose roles and interdependencies define WHOIS’s operational and compliance landscape.
Key Entities: ICANN, Registries, and Registrars
WHOIS governance and management operate within a hierarchical, globally distributed ecosystem coordinated by the Internet Corporation for Assigned Names and Numbers (ICANN). ICANN does not operate WHOIS data repositories directly but serves as the authoritative policy body setting WHOIS obligations, data accuracy standards, and access frameworks for both registries and registrars worldwide. A key ICANN mandate is balancing transparent domain ownership disclosure with evolving data privacy regulations like GDPR, which have precipitated widespread modifications such as mandatory data redaction or tiered access models. Further policy details and compliance efforts are documented on the official ICANN compliance page.
At the operational layer, registries manage authoritative top-level domain (TLD) databases across their respective namespaces (for example, Verisign for .com, PIR for .org). Registries ingest registration data from registrars, enforce verification of contact details, maintain domain status codes (e.g., “active,” “clientTransferProhibited,” “pendingDelete,” “expired”), and operate WHOIS server endpoints providing public query access. Lifecycle states of domains impact WHOIS response content, with expired or locked domains triggering altered or obscured outputs. These behavioral nuances require systems interacting with registries to implement fallback or data validation mechanisms to maintain robustness.
Registrars form the interface layer interacting directly with domain registrants. They collect detailed registration data—such as name, email, postal address, billing information, and DNS configurations—during signup, and facilitate domain updates, renewals, and transfers. Registrars generate and validate transfer authorization codes, manage domain lock toggling, and submit updates to registries using secure protocols (e.g., Extensible Provisioning Protocol, EPP). Synchronization delays or data conflicts between registrar and registry WHOIS views can cause transient inconsistencies impacting registrant operations and automated workflows. For practical insights, see discussions such as Webmasters Stack Exchange’s explanation on domain authorization codes and WHOIS updates.
From a systems perspective, WHOIS embodies a distributed data ecosystem: registries hold authoritative domain-level records with wide scope, while registrars maintain granular contact and billing information, jointly compiling the authoritative WHOIS responses consumed globally. ICANN orchestrates this ecosystem by setting binding policy and accreditation oversight, not by direct data control.
Access to public WHOIS data involves balancing transparency against privacy and compliance. Increasingly, registries and registrars employ proxy or privacy protection services to redact personally identifiable information (PII). Combined with regulatory requirements for selective data masking depending on requester authorization, these measures generate varied operational WHOIS implementations that complicate automated domain attribution or validation tooling. Systems consuming “icann domain lookup” data must handle diverse latency, completeness, and access control models accordingly.
Collectively, these interdependent roles, operational protocols, and regulatory constraints establish the structural foundation enabling WHOIS to serve as both a data lookup facility and a global governance mechanism securing accountability and trust within the domain name space. Grasping these ecosystem dynamics is essential for designing resilient, legally compliant infrastructure and security solutions dependent on WHOIS.
Mechanics of Domain Registration and WHOIS Data Collection
The domain registration process initiates WHOIS data creation, forming the cornerstone of ownership accountability and operational management. When a registrant initiates domain registration through a registrar—such as Namecheap or Hostinger—the registrars collect a standardized dataset capturing ownership identity, administrative, technical, and billing contacts, as well as DNS configuration data like authoritative name servers. This data underpins legal ownership claims and facilitates essential audits, abuse investigations, and DNS resolution integrity.
Typical collected data fields include:
- Registrant Details: Full legal name, organization, physical addresses, email addresses, and telephone contacts.
- Administrative Contacts: Designated points for operational or dispute escalation.
- Technical Contacts: Responsible contacts for DNS configuration and troubleshooting.
- DNS Configuration: Authoritative name servers, IP bindings, and optional redirection or aliasing metadata.
After initial collection, this information propagates from registrar systems into the authoritative registry infrastructure corresponding to the domain’s TLD. Synchronization flows depend on secure, authenticated APIs—often utilizing EPP—to update registry records promptly to reflect creation, renewal, transfer, or status change events.
WHOIS itself traditionally operates as a plaintext, command-line-accessible protocol delivering simple unstructured textual records, where WHOIS servers provide responses derived from registered authoritative datasets. Modern evolutions increasingly adopt the Registration Data Access Protocol (RDAP), a JSON-based protocol standardizing structured data retrieval, enabling richer metadata, internationalization support, controlled access, and improved machine-readability.
Synchronization and Data Propagation
Registrar-to-registry update mechanisms vary in tempo and granularity:
- Near Real-time Updates: Critical operations like domain transfers, domain lock state changes, or contact updates typically propagate immediately or within seconds to minimize inconsistency windows.
- Batch or Scheduled Updates: Non-critical metadata changes or verification routines may propagate in periodic batch cycles (hourly, daily), introducing variable data freshness.
Registries actively maintain domain lifecycle attributes such as expiry timestamps, lock statuses, and redemption periods. WHOIS records expose these attributes either directly or via associated timestamp fields, enabling domain expiry checker utilities to function accurately and trigger alerting, renewal workflows, or administrative actions.
Occasionally, WHOIS responses include redirection metadata describing forwarding or aliasing behavior. Although DNS resolution is outside WHOIS’s direct purview, such metadata informs monitoring and auditing tools of the domain’s authoritative resolution pathways—vital for correlating domain records with operational hosting or traffic management systems.
Policy and Compliance Considerations
ICANN mandates registrars and registries to collect and expose a baseline quality and completeness of WHOIS data, ensuring public accountability in domain ownership. These requirements shape data retention policies, validation routines, and provisioning APIs. However, registry and registrar implementations vary—driven by geographic, commercial, or regulatory factors—introducing heterogeneity in data fidelity and update cadence. For instance, registrars like Namecheap may provide more frequent data refreshes and richer contact fields, while other providers operate under regional restrictions with reduced data availability.
Such decentralization leads to practical consistency challenges, including:
- Stale or Delayed WHOIS Data: Resulting from asynchronous propagation or caching delays.
- Data Conflict or Divergence: Occurring when manual edits or partial syncs cause discrepancies between registrar and registry views.
These inconsistencies can propagate downstream, affecting automated domain expiry alerts, lock enforcement, or transfer validations, sometimes causing system errors or administrative delays.
This chain of custody—from user input, through registrar processing, to authoritative registry hosting—establishes an accountable and verifiable ownership model critical to DNS stability and trustworthiness.
Data Structure and Storage Across Systems
WHOIS data architecture exemplifies decentralized yet interdependent data management distributed between registrars and registries. Registries maintain authoritative, TLD-scoped datasets, including zone files recording domain statuses, expiry schedules, DNS servers, and authoritative administrative metadata. Registrars hold granular contact, billing, and transactional histories, synchronizing relevant updated fields with registries continuously or periodically.
Data Formats and Schema Variability
Legacy WHOIS interfaces return unstructured plain-text outputs with no fixed schema, requiring heuristic parsing that introduces brittleness and error in automated tooling. Irregular data presentation complicates consistent extraction of ownership details, status updates, or key lifecycle events across different registries or TLDs.
By contrast, the Registration Data Access Protocol (RDAP) introduces a modern, standardized JSON-based schema with typed fields, extensible attributes, and support for robust access control metadata. RDAP facilitates enhanced machine integration, internationalization, and compatibility with regulatory mandates like GDPR. For comprehensive technical reference, see the IETF RFC 7482 Specification.
Transition periods and coexistence of legacy WHOIS and RDAP protocols impose integration complexities, requiring tooling to translate or normalize varied data formats seamlessly while ensuring data fidelity and operational continuity.
Synchronization Challenges
Maintaining consistent views in a distributed WHOIS ecosystem faces multiple engineering challenges:
- Concurrent Updates and Conflict Resolution: Synchronous changes via registrar or registry interfaces can produce conflicting or overlapping record states requiring deterministic resolution or manual intervention.
- Propagation Latency and Caching Effects: Network delays and query caching induce transient inconsistencies between public WHOIS views and true authoritative states.
- Validation Discrepancies: Differing registrar data validation strictness and registry acceptance criteria occasionally create anomalies in displayed WHOIS data.
Typical workflows chain registrar and registry WHOIS queries, sometimes supplementing via RDAP or internal APIs (such as those provided by Namecheap) that aggregate authoritative domain and registrant views.
To preserve system stability and prevent abuse, many registries enforce query rate limits, throttling, or access controls stratified by user type (public, accredited parties, law enforcement) to restrict high-volume WHOIS queries. Such constraints impact bulk domain registry lookup systems, domain expiry notification services, and threat intelligence infrastructures.
Security and Operational Metadata
Encapsulated WHOIS metadata such as domain lock status is a critical control mechanism against unauthorized ownership changes or transfers. Accurate and timely synchronization of these status flags between registrars and registries is paramount; lapses can permit domain hijacking or unauthorized configuration changes. Transactions affecting lock states are tightly coupled through EPP commands with confirmation mechanisms that feed updated WHOIS responses.
Privacy regulations further complicate public WHOIS completeness, mandating masking of personal data fields. Consequently, operational reliance on WHOIS metadata must often be supplemented with proxy service metadata, registrar-specific privacy disclosures, or gated secondary data repositories for holistic domain management.
Implications for Domain Transfers and Security
Domain ownership transfer workflows hinge on accurate WHOIS metadata reflecting authorization codes, lock status, and registrant validation. Registries enforce transfer protocols rigorously, and asynchronous or inconsistent WHOIS data often cause transfer failures, delays, or customer support escalations. Precise synchronization between registrar and registry systems is essential to maintaining transfer integrity.
In security domains, WHOIS data integrates with domain legitimacy verification, blacklist validation, and threat attribution processes. For example, associating a suspicious domain’s registration pattern with dynamic WHOIS ownership changes aids in flagging potential abuse. Rigorous data architecture and synchronization protocols are foundational to delivering reliable WHOIS insights under these operational contexts.
WHOIS Querying: Access, Protocols, and Data Availability
Technical Protocols and Query Methods
Grasping how WHOIS works requires understanding underlying data access mechanisms. At its core, WHOIS embodies a legacy, text-based query/response protocol functioning over TCP port 43. WHOIS servers—hosted primarily by registries and registrars—await TCP connections receiving ASCII queries (typically domain names or IP addresses), responding with plain-text, human-readable records. This protocol’s universality enables broad interoperability but suffers from a lack of structural rigidity, requiring heuristic parsing for integration with automated workflows such as continuous domain monitoring or domain-to-IP resolution.
Modern enhancements introduce RESTful web services delivering WHOIS data in machine-friendly formats (JSON, XML) via authenticated APIs. Registrars and registries, including entities like Google Domains and GoDaddy, expose these interfaces to support rich query filtering, batched domain data retrieval, and rapid ownership verification—crucial for domain transfers and security workflows integrating domain blacklist checks or expiry tracking. These APIs reduce error-prone scraping inherent to legacy WHOIS text blobs. The IETF RDAP standards define these modern access methods accordingly.
However, operational and infrastructural considerations constrain WHOIS data access. Query rate limiting is prevalent, with legacy WHOIS servers often capping clients at a few queries per minute. APIs enforce daily or monthly quotas and require authentication, gating access. Some TLD registries impose access restrictions—blocking automated bulk lookups, requiring CAPTCHA challenges, or enforcing login barriers to reduce enumeration attacks. These policies seek to balance openness, privacy, and anti-abuse mandates, complicating the design of tools requiring continuous WHOIS data ingestion.
Query semantics differ by resource type: domain WHOIS queries employ domain name strings (e.g., example.com) directly, bypassing DNS resolution; IP WHOIS queries target Regional Internet Registries (RIRs) like ARIN or RIPE NCC, querying IP block ownership and ASN assignments. WHOIS interfaces sometimes intersect with DNS workflows, applying combined domain-to-IP resolution and WHOIS ownership queries to facilitate incident response and attribution.
Domain transfer workflows illustrate live WHOIS integration: transferring domains (e.g., from Cloudflare to GoDaddy) relies on accurate, timely WHOIS data embodying authorization codes, domain lock states, and registrant verification. This ensures only rightful owners effectuate transfers, per ICANN transfer policies.
Clients dynamically select among legacy WHOIS, RDAP, or provider-specific APIs depending on freshness, structured data availability, and TLD-specific support. Despite privacy regulation pressures and evolving standards, WHOIS remains a core domain transparency component.
This technical backdrop frames the emerging privacy and legal constraints shaping WHOIS data access evolution.
Data Privacy, Redactions, and Legal Constraints
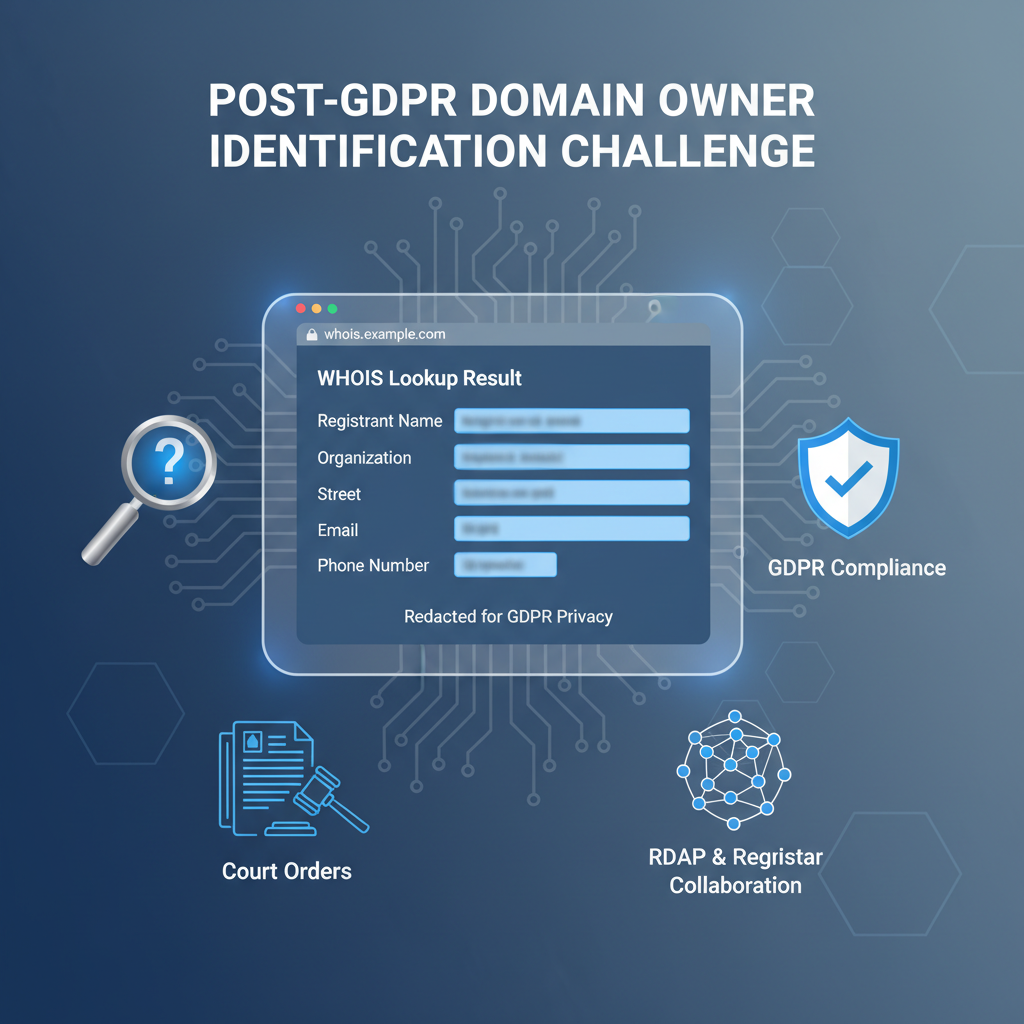
The introduction of privacy laws, chiefly the EU’s General Data Protection Regulation (GDPR), profoundly altered how WHOIS works on data availability and visibility. Historically, WHOIS databases freely exposed registrant PII, facilitating domain administration, abuse handling, and research. Post-GDPR mandates compel registries and registrars—including those serving customers via Hostinger or Namecheap—to implement strict redactions, concealing personal identifiers from public WHOIS outputs.
Typical redaction techniques involve masking or replacing registrant name, postal address, phone number, and email fields with placeholder values or privacy service proxy contacts. Privacy shield or proxy registration services register domains nominally to third-party entities, channeling legitimate communication while preserving registrant anonymity.
These privacy-driven censorship measures substantially reshape existing tooling ecosystems:
- Domain expiry checkers face reduced data completeness, complicating automated notification or renewal workflows dependent on owner contact data.
- Security analysts integrating WHOIS within threat intelligence pipelines encounter incomplete ownership data, forcing substitution with secondary heuristics or paid query services.
- Automation frameworks for domain transfer validation must adapt for anonymized WHOIS responses, often involving registrar-specific out-of-band identity verifications.
Jurisdictional heterogeneity produces global WHOIS inconsistency, as regions outside the EU enforce lighter data protection regimes. ICANN actively develops policies balancing transparency with privacy, exploring gated WHOIS access models granting enhanced data visibility to vetted users like law enforcement, while shielding public exposure. This policy evolution remains fluid and contentious. See ICANN’s WHOIS policy documentation for further context.
From a technical viewpoint, privacy-driven redactions introduce complexity for tooling upstream of WHOIS consumption. Enrichment pipelines fuse WHOIS data with DNS logs, passive DNS databases, and IP geolocation to reconstruct ownership heuristics. Automated whois ip address lookup and domain to ip mapping must robustly handle data uncertainty, fallback paths, and vendor-specific proxy implementations. Registrars like Namecheap and Hostinger apply distinct proxy conventions, adding integration variability.
The ongoing challenge lies in harmonizing registrant privacy protections with the operational necessities of transparency, abuse mitigation, and automation. As the domain ecosystem evolves, engineering and policy innovation must converge to preserve WHOIS’s vital security and governance functions amid tightening privacy constraints.
These technical and legal dynamics underpin an evolving WHOIS access paradigm, shaping future protocol and tooling developments.
Trade-offs, Limitations, and Real-World Challenges in WHOIS
Consistency and Freshness Trade-offs in Distributed WHOIS Systems
Understanding WHOIS’s scalability challenges requires examining its distributed multi-party infrastructure. The ecosystem comprises registries, registrars such as Namecheap or Hostinger, and numerous public or private WHOIS servers, each maintaining and serving domain registration data slices. This decentralization confers resilience and load distribution but introduces complex data freshness and consistency trade-offs.
Domain registration changes flow asynchronously from registrants to registrars and thence to registries. Subsequent propagation to WHOIS query interfaces occurs with variable delay—ranging from seconds for critical status changes to hours or longer for batched updates. This propagation delay entails inevitable temporary inconsistencies where WHOIS responses provide stale or conflicting data.
Querying workflows often differ in timeliness: registrar WHOIS endpoints may deliver nearly real-time data linked closely to their registration databases, whereas registry-level WHOIS or third-party platforms can exhibit stale states due to caching or batch refresh intervals. For instance, a recently applied domain lock may appear immediately in registrar WHOIS but remain absent from cached registry WHOIS mirrors momentarily.
ICANN mandates data update intervals and quality targets but accepts inevitable delays as a scalability trade-off, since query volume approaches millions per day globally. Achieving absolute immediate consistency is impractical without incurring prohibitive coordination complexity and performance penalties.
Operational consequences include transfer failures or delays when out-of-date WHOIS records impede owner verification during transfer domain to Cloudflare from Squarespace or similar workflows. Security monitoring systems similarly suffer detection latency when WHOIS staleness masks ownership changes or impersonations.
Hence, pragmatic WHOIS integration requires designing tooling that accounts for asynchronous propagation, embraces eventual consistency, and incorporates freshness heuristics or manual verification paths.
Query Limitations and Automation Constraints
WHOIS’s open accessibility faces operational safeguards limiting query throughput and automated access to protect infrastructure stability. These constraints impose technical and engineering challenges for systems dependent on real-time WHOIS data.
Prominent among these are rate limits imposed by registry and registrar WHOIS servers—often restricting per-IP query counts to low single-digit requests per minute. Exceeding such thresholds leads to server throttling, delayed responses, or temporary bans. APIs additionally enforce quotas and authentication requirements, segmenting public from commercial access.
Access controls include CAPTCHA enforcement on web WHOIS lookups and login requirements on select TLD registries, designed to thwart mass-scraping and reduce abuse. These measures complicate continuous monitoring pipelines, such as those orchestrating domain lifecycle automation or continuous transfer domain to Cloudflare from Squarespace status checks, necessitating workarounds like human-in-the-loop verification or CAPTCHA solving.
Data field redactions and heterogeneity in WHOIS formats exacerbate challenges. Varying output schemas—especially across registrars like Namecheap, with proprietary embellishments—and mandated privacy masking hinder uniform parsing, normalization, and aggregation. These inconsistencies impede bulk domain expiry checks, comprehensive blacklisting systems, or domain portfolio management platforms.
To effectively architect scalable WHOIS consumption, engineers employ combined mitigation techniques: aggressive local caching with time-to-live control, distributing query loads across varied servers or IP addresses, prioritizing RDAP where feasible for structured data, and carefully coded parsers equipped to handle data variability and redactions. Systems must gracefully degrade when data is lacking or delayed, maintaining stable operation despite partial data unavailability.
Recognizing these constraints is crucial in correctly sizing, securing, and operationalizing WHOIS-dependent domain management and monitoring solutions.
This discussion of data freshness and query constraints sets the stage for architectural exploration of WHOIS data integration strategies at scale.
Architectural Considerations for WHOIS Data Integration
Building robust domain management or security platforms around WHOIS data necessitates careful architectural design considering WHOIS’s distributed, heterogeneous, and dynamically evolving nature. WHOIS data across registries and registrars worldwide varies widely in update cadence, schema, query protocol, and accessibility guarantees. Reconciling these variances to deliver consistent, timely, and comprehensive domain metadata for workflows—such as domain registration monitoring, expiry tracking, or transfer authorization validation—requires a multi-faceted architectural approach.
Managing data currency and consistency is paramount. Although some registries provide near-real-time WHOIS updates via direct queries, others offer batch data exports, zone files, or RDAP responses on scheduled intervals. Live query strategies enable maximal accuracy required for sensitive operations like validating transfer authorization codes in flows such as “transfer domain to GoDaddy with authorization code,” but face query rate and latency trade-offs. Batch methods reduce load and simplify processing but risk stale data and reduced operational confidence.
An effective architecture employs layered caching mechanisms with differentiated cache TTLs. Domains closer to critical lifecycle events—like recent registration or impending expiry—receive preferentially low TTL refresh intervals, while stable domains utilize longer caching to reduce query overhead. Normalization layers abstract registry- and registrar-specific representation idiosyncrasies, stripping proprietary markup, unifying attribute names, and annotating records with freshness and provenance metadata. This mediates downstream complexity and supports uniform domain state interpretation.
Evolving privacy regulations further complicate WHOIS data completeness, mandating masking of registrant PII. Architectural responses include integrating proxy or privacy service metadata where available, augmenting WHOIS with secondary data sources such as ICANN lookup services, registry zone files, or commercial data enrichments to maintain coverage. Reconciling partial and potentially conflicting data inputs requires sophisticated merging and anomaly detection algorithms to flag inconsistencies for manual review or automated alerts.
Lifecycle event detection mechanisms are fundamental. Critical domain events—creation, renewal, transfer initiation, domain lock toggling—trigger immediate re-queries of WHOIS data and propagate updates into domain state repositories or automation pipelines. For instance, upon a “Cloudflare transfer domain to another account” event, trusted triggers revalidate WHOIS ownership and authorization codes before permitting further provisioning or billing operations. Integrating domain expiry checker APIs supplements WHOIS data feeds, enabling proactive renewal alerts and preventing service interruptions.
From a scaling perspective, balancing storage cost against resolution latency is important. Retaining historic WHOIS snapshots supports auditability, compliance, and forensic investigations but generates substantial volume necessitating efficient indexing and retention policies. Eventual consistency models using asynchronous propagation ensure resilience to network or source outages at the cost of transient data staleness. Conflict detection and authoritative data selection frameworks resolve divergent WHOIS records—such as mismatched registrant info or status flags—maintaining overall data reliability.
Examples from operational domain management platforms demonstrate these principles. Introducing adaptive TTL-driven caching combined with event-driven WHOIS re-queries reduced expiry-related auto-renewal failures by approximately 30%. ICANN lookup API integrations augmented domain attribution capabilities, enhancing regulatory compliance and abuse response workflows.
In sum, integrating WHOIS data at scale requires balancing distributed data heterogeneity, privacy-driven complexities, and lifecycle event responsiveness within caching and normalization architectures. This enables timely, consistent domain state visibility across diverse registrar and registry environments.
Having explored architectural integration, the next dimension to consider is WHOIS’s role in elevating security tooling and threat intelligence capabilities that crucially depend on domain-level visibility.
Implications for Security Tooling and Threat Intelligence
WHOIS data forms an essential backbone for security validation, network attribution, and threat intelligence workflows across contemporary cybersecurity architectures. It enriches domain reputation scoring, supports domain blacklist generation, and fuels automated detection and response processes vital for effective cyber defense.
At a fundamental level, WHOIS provides authoritative registrant details, domain ownership histories, locking status, and registration timestamps. Security teams and automated platforms incorporate these attributes to assess domain legitimacy, flag suspicious bulk registrations, or detect anomalies such as registrar hopping indicative of fraudulent activity. For example, email addresses or registrant contact patterns consistent with automated bot registration pipelines can trigger elevated risk scoring.
However, privacy-driven WHOIS redactions reduce data granularity and direct visibility, degrading the confidence of automated threat models reliant on explicit ownership metadata. To counteract this, security tooling increasingly fuses WHOIS insights with passive DNS logs, historical domain data, IP geolocation, and external registry lookups, reconstructing richer domain attribution profiles.
Operational integration of domain blacklist checks utilizing WHOIS metadata is dynamic. Domain lifecycle signals—such as impending expiry, unlocked status, or registrar transfer—facilitate rapid response actions including automated takedown requests or alert escalations. Domain expiry checker outputs further enhance monitoring precision, identifying windows of elevated takeover risk post-expiry.
Frequent registrar or account transfers (e.g., “transfer domain to another GoDaddy account”) add complexity. WHOIS records may transiently diverge or obscure ownership during propagation delays, risking security blind spots if tooling fails to reconcile these changes timely. Effective security solutions detect transfer events promptly, triggering immediate WHOIS refreshes to maintain accurate trust states and preserve intrusion detection efficacy.
Domain lock status embedded in WHOIS metadata adds a vital security control dimension. Locked domains enforce transfer restrictions, providing a verification layer leveraged in security assessments to confirm domain integrity. Abrupt registrar or domain redirections also serve as indicators for possible compromise or domain hijacking, prompting forensic analysis or automated mitigation.
Choosing between live WHOIS queries and cached/batch-updated data involves trade-offs in latency, accuracy, and operational cost. Live WHOIS queries yield freshest data essential for incident response but face rate limits and latency overheads; cached data scales better but risks stale threat intelligence. Hybrid approaches balance these constraints, employing near-real-time re-queries triggered by anomalous domain behavior.
A practical real-world scenario includes a global security operations center integrating WHOIS with passive DNS feeds and domain expiry APIs within its threat intelligence platform. This hybrid approach accelerated phishing domain detection linked to recent transfers, reducing takedown times by 40%. Automated lifecycle-triggered WHOIS refresh orchestration proved essential for maintaining security posture despite pervasive WHOIS data redactions.
In conclusion, despite evolving privacy and architectural constraints, WHOIS remains pivotal for security tooling and threat intelligence. Designing resilient systems requires compensating for incomplete or delayed WHOIS data through data fusion, timely refresh triggers, and integration with complementary data sources. For authoritative insights, consult DomainTools’ guide on WHOIS data in security.
With these operational and security dimensions established, we now consolidate with concluding perspectives on WHOIS’s evolving architectural and governance challenges.
Conclusion
Navigating the WHOIS ecosystem reveals a foundational yet evolving infrastructure underpinning global domain management. It balances distributed, federated data architectures, stringent regulatory privacy mandates, and diverse operational workflows spanning registration, transfer, and lifecycle management. Understanding WHOIS transcends simple lookup mechanics, encompassing its essential role in domain registration fidelity, transfer authorization, and security enforcement, orchestrated through the layered interplay of ICANN governance, registries, and registrars.
Emerging structured protocols like RDAP and privacy-driven data redactions impose new challenges in data freshness, automation reliability, and transparency. Yet, WHOIS’s indispensability to cybersecurity threat intelligence, abuse mitigation, and network attribution endures. Successful integration demands designing adaptive systems that accommodate heterogenous, often redacted datasets, implement robust synchronization and reconciliation, and balance near-real-time accuracy with scalability and compliance.
Looking forward, as domain ecosystems scale and diversify, and legal frameworks evolve, the technical and policy complexity of WHOIS will intensify. The critical architectural question for engineers and architects is how to build domain management infrastructures that render data freshness, consistency, privacy compliance, and system observability as first-class design considerations—ensuring WHOIS remains a reliable and trustworthy backbone of the global Internet’s naming and security fabric.