Key Takeaways
- WHOIS is a foundational protocol for querying domain registration metadata, critical to domain lifecycle management, infrastructure security auditing, and incident response workflows. Understanding the extent and limits of WHOIS data public availability is key for designing compliant systems, balancing transparency with privacy, and integrating WHOIS lookups within security monitoring, asset tracking, and compliance tooling. Engineers must navigate the interplay of protocol conventions, registry policies, evolving privacy regulations such as GDPR, and domain privacy services to ensure robust, privacy-aware implementations.
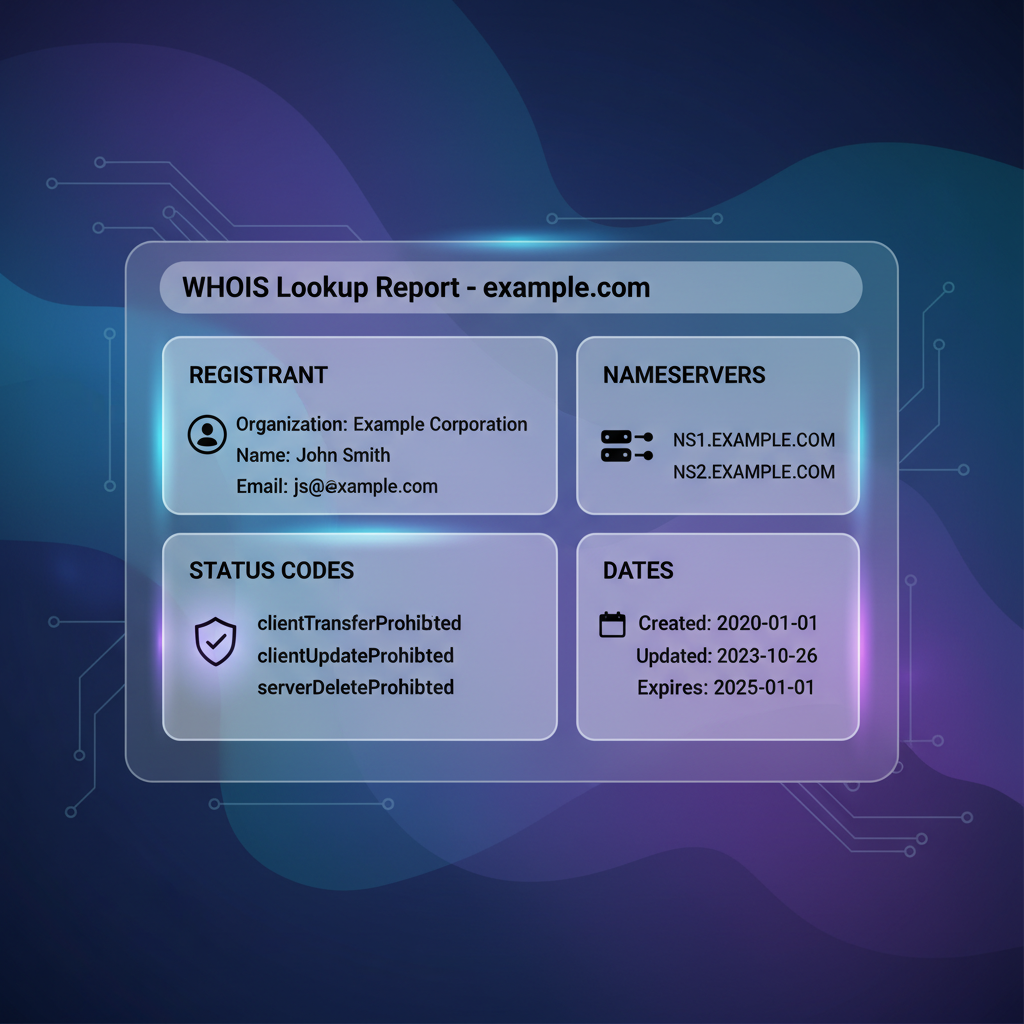
- WHOIS protocol reveals extensive registered domain metadata by default: Standard WHOIS queries typically yield registrant identity details (name, postal address, email, and phone), registrar and registry identifiers, domain status flags (e.g., clientHold, serverDeleteProhibited), and critical timestamps (creation, renewal, expiration dates). These data points directly influence system data models, access control logic, and verification procedures in domain-related services.
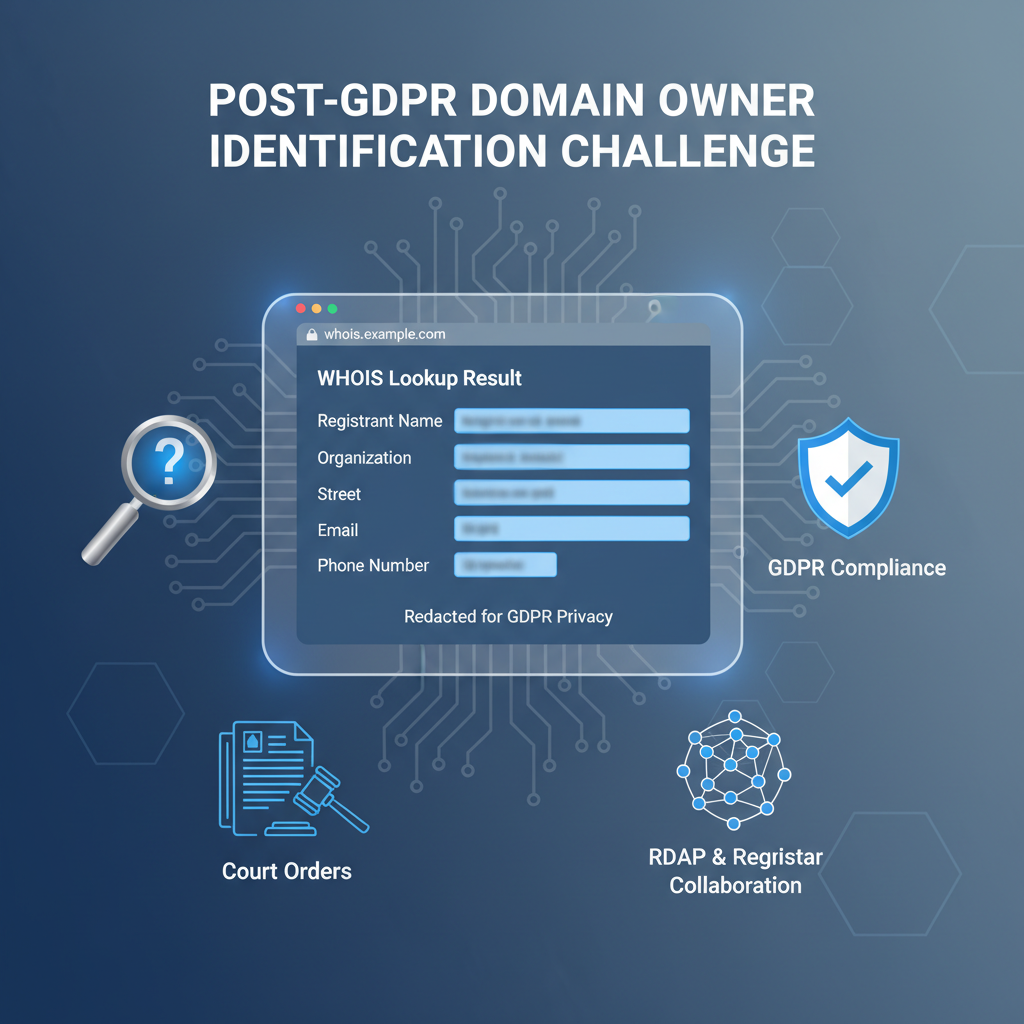
- GDPR mandates selective redaction of personally identifiable information in WHOIS: Since the GDPR enforcement, WHOIS servers linked to European registrants must redact or anonymize personal fields by default, demanding systems handle partial or pseudonymized datasets gracefully. This regulatory landscape affects not only data presentation but also legal compliance, requiring lookup services to treat WHOIS data as a semi-public resource.
- WHOIS privacy services function as proxy or masking layers: Domain owners often employ domain privacy services offered by registrars (e.g., Namecheap, GoDaddy) that systematically replace registrant contact details with proxy or forwarding contacts. System designs must accommodate the reconciliation challenges between the authoritative registrant data and the published masked records, including proxies’ update mechanisms and abuse reporting workflows.
- Redacted WHOIS records retain operationally relevant non-PII metadata: Even when registrant details are obscured, WHOIS responses usually continue exposing domain lifecycle dates, registrar identifiers, nameservers, and status codes. These fields underpin domain verification, lifecycle monitoring, and DNS debugging processes, sustaining operational transparency without compromising registrant privacy.
- WHOIS accessibility varies by registry and TLD policies: Different registries enforce distinct WHOIS publication standards and rate limits. Some restrict queries aggressively or impose limits to mitigate abuse, impacting caching strategies, load balancing, and reliability of automated lookup systems integrated into monitoring pipelines.
- Legal exceptions and compliance frameworks provide widened WHOIS data access: Law enforcement, trademark enforcement agencies, and courts can access more complete WHOIS data under secure, auditable conditions. WHOIS system designs must integrate tiered access controls and detailed audit logging to comply with jurisdictional and contractual disclosure requirements.
- WHOIS privacy introduces data integrity and correlation challenges across sources: Proxy masking and redactions produce inconsistent records across WHOIS queries and threat intelligence feeds, complicating data correlation and entity resolution. Systems must adopt probabilistic matching and heuristic analysis, understanding the resulting uncertainty while avoiding false positives.
- WHOIS lookup tooling requires robust handling of partial and mixed data completeness: Implementations must differentiate full, partially redacted, and proxy-protected WHOIS responses to maintain smooth user experiences and accurate parsing logic. This involves adaptive data extraction, fallback strategies, and nuanced UX workflows informing users of varying data visibility.
These considerations establish the technical context underpinning the evolving dynamics of WHOIS data visibility, privacy regulatory impacts, and domain privacy mechanisms. The article progresses to dissect individual WHOIS data elements, the influence of GDPR and other privacy laws, detailed operations of privacy services, and practical strategies for building resilient WHOIS data access and interpretation workflows under these complex conditions.
Introduction
WHOIS data has traditionally been presumed fully public; however, the reality is far more nuanced—especially for engineers developing domain management systems, infrastructure monitoring, and compliance tooling. The introduction of GDPR notably reshaped what personal information WHOIS lookups can disclose, compelling system designs that gracefully accommodate redacted or proxy-masked datasets without breaking vital functionality. Concurrently, registries and domain privacy services layering additional protection introduce further variability and complexity, including inconsistent data structures and query rate constraints, challenging reliable WHOIS integration.
Thus, the question “Is WHOIS public?” demands precise unpacking: what data does WHOIS expose by default, what privacy-driven redactions or proxies intervene, and under what legal or operational contexts do exceptions apply? Understanding this interplay is essential for building tooling that balances transparency, user privacy, and regulatory compliance. This article articulates the technical implications of GDPR and WHOIS privacy proxies on data visibility, identifies the metadata scope that remains accessible, and guides engineers on establishing resilient, privacy-aware WHOIS lookup architectures amid this evolving environment.
Fundamentals of WHOIS Data and Its Public Nature
Structure and Purpose of WHOIS Data
WHOIS is a critical, distributed internet infrastructure protocol, primarily managed by domain registries and registrars to provide structured metadata about domain registrations. A typical WHOIS record encompasses key data fields that span registrant identity (individual or organization), administrative and technical contacts, registrar and registry references, domain status codes (e.g., clientHold, serverTransferProhibited), timestamps (creation, last update, expiry), and authoritative nameservers. This structured metadata supports numerous automated domain lifecycle operations and governance mechanisms.
Functionally, WHOIS underpins domain ownership verification—enabling registries and registrars to authenticate transfer requests or renewals—as well as security and operational workflows. Network operators leverage WHOIS queries during abuse investigations, botnet infrastructure tracing, and incident response to identify responsible parties. Registries rely on accurate metadata to enforce policy compliance and support dispute resolution processes. Thus, WHOIS serves as a foundational source of truth for domain provenance.
From a technical standpoint, the WHOIS ecosystem includes the legacy port 43 TCP query protocol as well as modern RESTful API endpoints offered by many registrars and third-party service providers. However, the exact record formats, field availability, and redaction policies vary by registrar, registry, and TLD policies, resulting in parsing and normalization challenges in system integration. These must be handled robustly to ensure consistent extraction of critical data fields across diverse WHOIS sources. Detailed descriptions of WHOIS operation and protocol behavior are available in authoritative references such as the WHOIS protocol documentation.
The inclusion of personally identifiable information (PII)—such as registrant emails, phone numbers, and physical addresses—introduces a key tension. While transparency supports trust and operational coordination, privacy considerations and regulatory frameworks increasingly demand protective mechanisms such as domain privacy services or selective redaction to mask sensitive registrant details. Balancing operational transparency with privacy mandates drives protocol evolution, policy enforcement, and registrar practice variations. The ICANN Governmental Advisory Committee’s documentation on WHOIS and data protection offers in-depth insight into this complex intersection.
Recognizing this architecture clarifies why WHOIS was originally fully public by design but must now evolve to harmonize transparency with privacy and regulatory requirements.
Default Public Accessibility of WHOIS Records
Originally, WHOIS was designed as an openly accessible directory service, allowing anyone to query a domain’s ownership and administrative data without restrictions. This openness aligned with early internet principles favoring transparency to foster trust, simplify operational coordination, and enable verifiability—akin to a public telephone directory linking domain names to responsible parties.
Technically, the WHOIS protocol operates over TCP port 43 with standardized query-response semantics. Clients send a domain name query string, and servers reply with plain-text formatted records listing registrant and domain metadata. This raw access ensured universal reachability from compliant WHOIS clients or web-based interfaces, reinforcing WHOIS as a public-facing resource. Consequently, prior to privacy regulations, all registrant and contact data were exposed to query initiators indiscriminately.
This open design faced challenges as privacy regulations evolved, notably the European Union’s General Data Protection Regulation (GDPR), restricting public disclosure of personal data without lawful basis. Registries and registrars responded by instituting redaction policies systematically masking or replacing registrant PII in public WHOIS records. Consequently, WHOIS queries for privacy-enabled domains often return placeholder information or generic privacy service contacts instead of original registrant details. The detailed dynamics of these changes are explicated in professional analyses such as DomainTools’ overview of WHOIS privacy impacts.
Nonetheless, WHOIS data remains partially public under these constraints. Core technical metadata—including domain status codes, registrar identifiers, nameservers, and dates governing domain lifecycle—remain visible to support operational needs such as DNS troubleshooting, dispute handling, and network debugging. This selective transparency preserves accountability without exposing personal data unnecessarily.
Domain privacy services offered by registrars, such as Namecheap’s or GoDaddy’s WHOIS privacy options, illustrate operational mechanisms balancing transparency with privacy. These services register domains on behalf of clients, replacing personal details with proxy contacts and managing forwarding of legitimate queries through controlled channels. This setup protects registrants from spam or harassment while allowing lawful inquiry routing.
Legal and registry-authorized entities—including law enforcement and trademark protection agencies—retain avenues to obtain unredacted WHOIS data under defined procedures. This layered access model embodies the critical design trade-off: maintaining open accountability while limiting indiscriminate personal data exposure. For domain system architects and engineers, this nuanced reality guides privacy-aware workflow design and tooling integration strategies.
Hence, the direct answer to “Is WHOIS public?” is conditional: WHOIS is a publicly accessible protocol and service by design, but data exposure depends on legal mandates, registry policy, and domain privacy protections that collectively shape data visibility and usage constraints in today’s internet ecosystem.
This foundational understanding paves the way to explore how privacy regulations like GDPR and domain privacy services impose selective data redactions and proxying, adding new complexities engineers must address when interfacing with WHOIS data.
Impact of GDPR and Privacy Regulations on WHOIS Data Visibility
The enactment and enforcement of the General Data Protection Regulation (GDPR) within the European Union, along with analogous global privacy statutes, drastically transformed WHOIS data availability. Historically, WHOIS databases broadly published registrant personal data to promote transparency and combat abuse. GDPR’s stringent protections for PII reframed WHOIS publication principles to prioritize privacy, triggering domain registries and registrars to adapt data disclosure practices to comply with data minimization and lawful processing requirements.
Regulatory Mandate for Data Minimization and Its Technical Interpretation
GDPR enshrines data minimization as a core principle, compelling data controllers to process only data necessary for specified purposes and refrain from over-exposure. For domain registries and registrars operating within GDPR jurisdiction or managing EU-based registrants, this translated into concrete obligations: publicly accessible WHOIS responses must redact or anonymize personal fields, including registrant names, postal addresses, phone numbers, and email addresses, unless lawful bases such as explicit consent or legitimate interest apply.
Technically, WHOIS server implementations enforce this by:
- Protocol-Level Redactions: WHOIS servers apply filtering rules at query response generation to exclude or obfuscate personal data fields. This involves configurable output templates or regex-based parsers that systematically redact sensitive values before any public dissemination. Such filtering guarantees consistency and compliance across all query responses emanating from that WHOIS endpoint.
- Contact Role Differentiation: To uphold operational integrity, redactions often focus on the registrant contact, heavily masking this data, while retaining selective visibility of administrative and technical contacts. This differentiation ensures that domain management, abuse handling, and operational troubleshooting remain feasible without broad PII exposure.
GDPR thus reframes WHOIS from an unfiltered data source to a calibrated transparency service balancing privacy needs with operational necessities. Core metadata such as domain status, registrar identity, lifecycle timestamps, and nameserver configuration continue to be publicly visible, preserving the ecosystem’s ability to maintain accountability and technical functionality. The ICANN GDPR Implementation Overview provides thorough treatment of these regulatory and operational adaptations.
Real-World Operational Challenges and Variability
While GDPR offers regulatory clarity, practical enforcement across the global registry ecosystem remains variable. Some registries—such as EURid (.eu) and Nominet (.uk)—apply strict, consistent redactions, whereas numerous country-code top-level domains (ccTLDs) exhibit uneven or more permissive policies. This fragmentation creates challenges for engineers and systems relying on uniform, comprehensive WHOIS data for security monitoring, incident response, or domain reputation analysis.
For example, cybersecurity platforms correlating WHOIS registrant metadata with abuse patterns find detection accuracy diminished when personal data is heavily redacted or proxied. Incident response workflows require fallbacks to other intelligence sources or escalation to manually verified channels. These real-world inconsistencies compel engineering designs embracing heterogeneity and partial data, rather than assuming full WHOIS transparency.
Intersection with Commercial Domain Privacy Services
Parallel to GDPR’s legal mandates, commercial WHOIS privacy services have emerged, offering registrants additional obfuscation even where not strictly required by law. These services generally substitute the registrant’s personal data with proxy contacts, providing privacy benefits but complicating attribution and operational visibility for downstream systems. Typically implemented by registrars or third-party providers, these services coexist with regulatory redactions but differ in control, scope, and operational characteristics.
Together, GDPR and commercial proxy services have transformed WHOIS data from an open directory into a layered, privacy-aware information resource requiring technical and policy sophistication to manage effectively. The following sections dissect the mechanisms underlying selective redaction, proxy masking, and their operational implications on domain ownership visibility and WHOIS integration reliability.
Partial Redaction and Proxy Masking Techniques
Implementing GDPR compliance and enhancing registrant privacy necessitate technical methods to redact or proxy WHOIS data elements, balancing secrecy with domain operational transparency. These methods form the technical backbone of today’s domain privacy infrastructure.
Standard Redaction Practices in WHOIS Outputs
Registries and registrars typically apply selective removal or substitution of registrant personal data fields in public WHOIS responses:
- Replacement of Email, Phone, and Addresses: Personal contact fields are frequently replaced with site-wide standardized placeholders such as “REDACTED FOR PRIVACY” or privacy service-specific proxy addresses (e.g., [email protected]). These proxies enable forwarding legitimate inquiries while shielding registrant PII from direct exposure.
- Retention of Operational Metadata: Non-personal data—domain status flags, registrar information, creation and expiration timestamps, technical administrative contact details—remain visible, sustaining operational transparency and troubleshooting capabilities.
This selective redaction strategy protects registrant privacy without undermining WHOIS’s role in domain task automation and dispute resolution.
Proxy Registration Services and Their Role
Beyond simple redaction, many registrants employ domain privacy proxy services, which function as substitution layers:
- Upon WHOIS query, proxy contact details replace the actual registrant’s information in WHOIS output.
- Proxy services receive and forward abuse notifications, legal inquiries, or domain-related communications to the true registrant while maintaining the domain owner’s anonymity in public records.
These services are implemented through delineated registry and registrar data pipelines that interpose privacy provider contact fields in registry databases prior to WHOIS query servicing. This provenance obfuscation improves privacy but introduces complexity in attribution, abuse handling, and data consistency management.
Constraints and Potential Failure Modes
- Legal and Regulatory Disclosure: Proxy services comply with legal and contractual obligations to reveal true registrant details upon valid court orders, law enforcement requests, or IP infringement claims. This necessitates maintaining accurate registrant records escrowed securely, complicating backend data governance.
- Blacklisting and Risk Scoring: Some security systems or reputation frameworks treat proxy-masked domains cautiously or blacklist them outright due to enhanced anonymity, negatively impacting user and system trust. Proxy services must engage in rigorous vetting and abuse mitigation to preserve ecosystem confidence.
- Data Consistency and Correlation: Proxy masking disrupts linkage across data sources, impeding threat intelligence correlation and causing entity resolution ambiguities. Engineered heuristics and probabilistic matching become necessary to infer actual registrant associations.
Impact on Operational Ecosystems and Reconciling Privacy with Transparency
The adoption of privacy protection services complicates domain reputation engines, phish detection, and abuse remediation systems reliant on WHOIS metadata. Operators deploy alternative investigative techniques—including behavioral and network telemetry analysis—to compensate for obscured ownership data.
This dynamic illustrates that WHOIS transparency is now a continuum rather than a binary: data ranges from fully public to partially redacted proxy representations, with controlled escalated access for authorized entities. Protocol developments such as ICANN’s Registration Data Access Protocol (RDAP) facilitate tiered, authenticated access to more complete registrant details to balance transparency with privacy constraints.
In sum, partial redaction and proxy masking constitute the practical mechanisms enabling modern domain privacy models, ensuring regulatory compliance and operational functionality co-exist amidst intensified privacy demands.
Operational Mechanics of WHOIS Privacy Services
WHOIS privacy services supplant registrant contact data with proxy or anonymized entries in public WHOIS records, reshaping the traditional transparency model to safeguard user privacy against unsolicited or malicious contacts. When domain privacy is enabled, typical registrant fields—name, postal address, email, and phone—are systematically replaced with privacy service contacts that serve as forwarding gateways. This abstraction protects identity while fulfilling ICANN and registry mandates for reachable and accurate contact points.
Operationally, these services act between registrants and the WHOIS infrastructure. Registrars or third-party providers populate proxy contact data into registry databases and WHOIS servers, maintaining public visibility of critical operating fields (domain statuses, creation dates, DNSSEC flags) unaffected for continuity.
Major registrar implementations show variations:
- Namecheap WHOIS privacy substitutes all registrant fields with dedicated proxy contacts fully controlled by Namecheap’s service, often leveraging forwarding email aliases to anonymize correspondences.
- GoDaddy WHOIS privacy offers layered privacy options, where customers may activate first-party or third-party privacy layers, and some data fields can remain visible or partially masked depending on service level and jurisdictional constraints.
Configurability extends to client-facing control panels enabling registrants to enable or disable privacy services post-registration. Underlying verification systems ensure underlying registrant data remains accurate, supporting renewal notices, abuse processing, and contractual compliance while keeping public records masked.
Compliance with ICANN accuracy requirements is maintained by privacy services through rigorous back-end validation and operational protocols, ensuring proxy contacts are bona fide, responsive points of contact. Transparency levels vary by privacy model, with some providers permitting data disclosure under authenticated abuse or legal requests, while others strictly mask information. See ICANN’s WHOIS Accuracy Program Specification for detailed policy context.
This operational architecture balances conflicting demands: user-centric identity concealment in public WHOIS versus registry and regulatory obligations for accurate, verifiable data. Understanding these foundational mechanics clarifies the downstream challenges that WHOIS privacy introduces for WHOIS consumers, security systems, and legal processes.
Challenges in Maintaining Data Reliability and Accessibility
The proliferation of privacy services significantly complicates WHOIS data reliability for systems depending on accurate domain ownership information. Automated WHOIS parsers and analytics pipelines confront a heterogeneous, partially redacted data landscape with multiple idiosyncratic formats and proxy conventions.
First, the diversity of formats and obfuscation strategies impairs deterministic parsing. While some providers use fixed proxy templates, others insert generic redaction tokens or partial masking, rendering consistent extraction of registrant details challenging. This fragmentation inflates error rates, increases the need for complex heuristics, and requires ongoing maintenance to accommodate new privacy patterns introduced by registrars or jurisdictional policy changes.
Second, query rate limiting and access restrictions by registrars and privacy services further degrade data acquisition reliability. To counter bulk WHOIS scraping—often exacerbated by attempts to overcome privacy masking—query thresholds per IP, API key, or account enforce prudent resource usage but simultaneously constrain legitimate high-volume uses such as security operations centers or domain portfolio audits. Systems must coordinate query instrumentation, implement backoff policies, and integrate cache layers to navigate these constraints.
Third, the regulatory environment demands mandated redactions under GDPR and similar frameworks. These redactions produce patchwork WHOIS datasets with anonymized or empty personal data fields, complicating ownership validation, abuse detection, and forensic attribution in cyber investigations. Without comprehensive registrant visibility, security teams resort to escalation procedures or registry cooperation to obtain accurate ownership information, introducing latency and procedural complexity.
These tensions highlight an enduring conflict between privacy and operational transparency. Procedurally, registrars mediate access via escrowed undisclosed WHOIS data, tiered APIs with authenticated access for vetted parties, and formal legal processes to balance privacy protections with legitimate information needs. However, these mechanisms are regionally fragmented and evolve continuously, requiring system engineers to architect for partial and conditional data visibility environments.
Registrar implementations vary, influencing the freshness, completeness, and trustworthiness of WHOIS data ingested by downstream applications. For instance, GoDaddy’s privacy services enable access to extended ownership data via abuse contacts or registrar liaison on authenticated requests, while Namecheap focuses on stringent anonymization with limited public detail. These operational divergences impact downstream data quality and consequently require adaptable tooling designs able to process varied privacy postures effectively.
Collectively, these challenges cascade through security monitoring, reputation inference, incident response, and compliance workflows, necessitating sophisticated data enrichment and contextualization architectures to compensate for opaque ownership records.
Impact on WHOIS-Dependent Applications and Mitigation Strategies
WHOIS data’s evolving privacy posture significantly alters the operational efficacy of systems reliant on domain registrant metadata. Cybersecurity platforms traditionally draw on WHOIS registrant profiles to attribute malicious infrastructure, identify threat actors, and correlate abusive domain patterns. The ubiquity of privacy proxies dilutes these signal strengths, compelling analysts and automated tooling to rely more heavily on auxiliary data sources or procedural escalations to establish ownership contexts.
Incident response teams face increased overhead, as limited WHOIS data necessitates cooperation with registrars or proxy services to obtain complete domain owner details, slowing mitigation efforts during active threats. These operational delays have direct implications on the effectiveness of responding to phishing, malware distribution, or botnet command-and-control takedowns.
Compliance operations, such as brand protection and domain verification, are similarly impacted. Automated enforcement mechanisms that check WHOIS accuracy and registrant legitimacy now must contend with obscured data, requiring integration with registrar APIs or legal channels to perform comprehensive validation. This adds integration complexity and potential failure modes, necessitating fallback and manual review processes.
Law enforcement agencies encounter analogous hurdles. Privacy regulations limit direct public access, enforcing reliance on tiered systems where registrars provide ownership data upon valid legal demand. While essential for privacy enforcement, these controlled access models introduce procedural latency that can hinder timely investigative responses and forensic analysis.
To mitigate visibility gaps, system architects adopt multifaceted strategies:
- Establishing trusted data-sharing partnerships with registrars and privacy providers to gain authorized access to non-public registrant data within compliance boundaries.
- Employing behavioral and network telemetry analyses to infer domain threat context independent of registrant details.
- Combining multiple data sources—including passive DNS, SSL certificate transparency logs, reputation services, and WHOIS historical archives—to enrich domain intelligence despite contemporary WHOIS opacity.
These approaches require architecting data pipelines resilient to partial data availability, capable of probabilistic inference and capable of incorporating authenticated data access where feasible. For further reading on leveraging certificate transparency for domain tracking, see Cloudflare’s engineering insights.
Adapting to this evolving WHOIS privacy landscape demands ongoing attention to regulatory shifts, operational monitoring, and flexible tooling architectures to preserve domain visibility without eroding privacy commitments.
Legal Exceptions and Boundaries Around WHOIS Data Access
Conditions Allowing Access to Redacted or Private WHOIS Information
The transition from entirely public WHOIS data to a privacy-aware paradigm predicated on GDPR and related regulations introduces legally mandated exceptions to data redaction. While personal information is suppressed in public WHOIS outputs, entities with legally verifiable authority retain rights to access complete ownership data through robust procedural and technical controls.
Such entities commonly include law enforcement investigating cybercrime, anti-abuse teams handling trademark or intellectual property claims, judicial authorities issuing subpoenas, and contracted registrars fulfilling regulatory compliance. Access is provisioned through secure, authenticated portals or API endpoints fortified with multi-factor authentication, role-based access controls, and encrypted transport layers.
Every access event is meticulously logged in immutable audit trails providing evidentiary provenance, deterring misuse and enabling compliance reporting. Multijurisdictional operations require complex balancing of conflicting data privacy mandates, further complicated by registrar-registrant contracts embedding disclosure conditions aligned with local laws.
This necessity drives the implementation of tiered WHOIS architectures:
- Public interfaces show fully or partially redacted WHOIS records adhering to data minimization.
- Privileged internal systems or authorized external applications query comprehensive WHOIS datasets under strict access governance.
- Audit subsystems track identities, time stamps, and query scopes of all privileged lookups.
This segregation enforces compliance while preserving the functional transparency expected in domain governance. Consequently, post-GDPR WHOIS data is not universally public in all cases, but access pathways exist ensuring accountability via lawful and auditable release mechanisms. For further exploration, see analyses of WHOIS privacy and data protection post-GDPR.
Limitations on WHOIS Lookups and Compliance Requirements
Contemporary WHOIS lookup services operate under stringent technical and legal constraints shaped by privacy regulations, registry contracts, and anti-abuse mandates. Query rate limits imposed by registrars restrict the volume of WHOIS requests from individual IPs, API credentials, or accounts to prevent denial-of-service attacks and bulk data scraping that often fuels spam and fraud operations. Surpassing thresholds triggers mitigating actions such as throttling, temporary blocks, or CAPTCHA challenges, complicating high-throughput, low-latency lookup systems integrated into security or operational pipelines.
Additionally, providers embed legal terms governing WHOIS data usage that prohibit unauthorized redistribution, commercial exploitation, or derivative data harvesting absent registrant consent. Enforcement employs anomaly detection, automated usage pattern analysis, and access revocation to uphold compliance.
WHOIS services must also surface and respect registrants’ privacy preferences, reflecting redactions and privacy service masking in responses and displaying relevant notices where required by law. This mandates lookup implementations integrate registrant consent states and policy metadata dynamically.
From an engineering perspective, embedding compliance requires architectures incorporating:
- Real-time monitoring and alerting on query patterns, geolocations, and client behavior to mitigate abuses proactively.
- Enforcement of data minimization downstream, ensuring sanitized outputs where privacy demands dictate.
- Synchronization with registry metadata on consent and privacy policy states to ensure dynamic compliance.
These considerations transform WHOIS infrastructures from simple lookup engines into complex, policy-aware systems negotiating the nexus of transparency, privacy, security, and regulatory adherence. For authoritative guidance, consult ICANN’s WHOIS and Data Protection.
Operational trade-offs manifest in latency-compliance balances and openness-security control tensions, demanding carefully architected solutions ensuring lawful, secure, and performant WHOIS services. The question “Is WHOIS public?” inherently encapsulates layered, context-dependent access entitlements rather than unconditional openness.
With this legal and compliance grounding, the following section examines how WHOIS service designs operationalize these complex policy requirements through scalable, auditable technologies and streamlined processes.
Best Practices for Accessing and Utilizing WHOIS Data Under Privacy Constraints
Techniques for Building Resilient WHOIS Lookup Systems
The evolving regulatory regime surrounding WHOIS data, particularly GDPR’s influence, compels engineering teams to design lookup systems accommodating partial redactions, proxy masking, and variable data availability. Understanding that WHOIS lookups no longer guarantee comprehensive registrant data is foundational for resilient tooling.
Variations in field redaction between registrars, registry policies, and TLDs mean that some WHOIS servers suppress emails and phone numbers entirely, others partially redact, and a few obscure registrant names only. This creates heterogeneous datasets complicating automated parsing and cross-domain data correlation.
Multi-Source Data Aggregation
Robust WHOIS lookup architectures circumvent these limitations by aggregating data from multiple distinct sources:
- Diverse WHOIS servers: Querying multiple registrar or registry WHOIS endpoints to gather varying completeness levels, as different providers exhibit distinct redaction policies or data freshness.
- Registrar-specific APIs: Leveraging proprietary APIs that sometimes offer enhanced data fields and subscription-based access, albeit often rate-limited and privacy compliant.
- Regional Internet Registries (RIRs): Incorporating network assignment and infrastructure ownership data from ARIN, RIPE NCC, APNIC, etc., to correlate domains and IP assets with registrant information.
- Passive DNS and third-party intelligence: Enriching WHOIS data with DNS resolution histories, hosting metadata, and historical WHOIS snapshots from archival services.
Synthesis across these disparate sources enables the construction of more complete and reliable domain ownership profiles. Though not circumventing redactions, such aggregation improves coverage and attribution confidence. For instance, RIR datasets may reveal registrant infrastructure contacts filtered out in WHOIS but crucial for security investigations as detailed in ARIN WHOIS documentation.
Caching, Query Batching, and Rate Limit Management
Managing query performance and operational stability requires sophisticated caching strategies to minimize redundant WHOIS requests. Cache layers storing recent query results reduce bandwidth and avoid triggering registrar query limits, critical for large-scale domain portfolio monitoring or security analysis pipelines.
Utilizing bulk or batched WHOIS APIs where available (as many registrars now offer) optimizes throughput versus sequential single-domain queries over port 43. Batching reduces overhead, query volume, and latency, enabling scalable system designs.
Robust error handling includes retry policies with exponential backoff for transient network issues or server unavailability, circuit breakers to prevent cascading failures during sustained downtime, and comprehensive logging enabling rapid diagnostics of data gaps or anomalous query failures. These engineering best practices align with patterns enumerated in Martin Fowler’s reliability design literature.
Protocols vs. Modern API Endpoints
Legacy WHOIS protocol remains widely supported, facilitating broad compatibility with minimal dependency. However, unstructured, free-text responses complicate parsing and reliable data extraction, especially in the face of privacy-induced redactions.
Modern RESTful APIs offered by registrars incorporate structured JSON responses with authentication and query filtering capabilities. While promising richer integration and scalability, these APIs still honor privacy redactions, mandating tooling to cope with incomplete data. Additionally, they introduce operational concerns such as managing API keys, quotas, and potential vendor lock-in.
Architects must weigh trade-offs: simplicity and universality with legacy protocols versus enhanced control and structured data at the expense of complexity and dependency. Supporting hybrid models enables flexible, progressive system adoption strategies.
Continuous Regulatory Monitoring
Privacy regulations continue evolving, as do ICANN policy interpretations and regional data protection practices. Consequently, WHOIS data completeness and display modes shift continually, necessitating that WHOIS tooling teams incorporate regulatory monitoring into development and operational lifecycles.
Evolving requirements influence data redaction scope, consent mechanisms, and lawful disclosure pathways. Systems must be agile enough to update data processing pipelines, query filtering, and user notifications accordingly, ensuring ongoing compliance and audit readiness.
Collectively, these engineering strategies form the foundation for reliable, legal, and performant WHOIS lookup architectures that gracefully accommodate partial data and privacy protection layers.
Evaluating Privacy Risks and Trade-Offs for Domain Management
Understanding domain whois privacy services from the registrant perspective highlights the operational trade-offs between privacy protection and openness within domain management processes.
How Domain WHOIS Privacy Services Work
Privacy services replace actual registrant contact data displayed in WHOIS records with proxy or forwarding information, concealing the registrant’s identity. For example, “Jane Doe, [email protected]” might be replaced with “Privacy Service, [email protected]” in all public WHOIS queries.
This substantially lowers exposure to unsolicited contact vectors such as spam, phishing, harassment, or identity theft. However, the obfuscation complicates direct transparency and trust assessments derived from ownership records.
Security and Operational Implications
While protecting registrant privacy, privacy proxies obstruct cybersecurity and abuse workflows reliant on WHOIS ownership visibility:
- Impeding attribution and investigation of malicious domains.
- Limiting threat intelligence enrichment fidelity.
- Affecting domain reputation scoring and user trust heuristics.
These challenges necessitate additional investigation access paths, such as escalation through privacy providers’ abuse contacts or formal legal requests. For IP infringement or abuse mitigation, visible ownership data expedites accountability and resolution.
Compliance and Legal Nuances
Despite public redactions, registrars maintain accurate registrant information unavailable in public WHOIS, disclosed only under legally authorized conditions such as subpoenas, law enforcement demands, or intellectual property enforcement. This ensures privacy does not equate to absolute anonymity.
Domain privacy providers must clarify these limitations to customers, balancing marketing messaging with realistic privacy promises and operational transparency regarding exceptional disclosures.
Debating “Is WHOIS Privacy Worth It?” From Domain Manager Perspectives
Privacy services reduce public data exposure but also:
- Introduce risk vectors if proxy services are unreliable or mishandle communications.
- Impact automated monitoring and brand protection systems reliant on registrant visibility.
- Add cost and operational dependence on third parties managing proxy infrastructure.
Evaluating these trade-offs requires domain owners to model threat profiles, operational requirements, and compliance obligations. High-profile or sensitive domains often prioritize privacy despite complexities, while infrastructure or trust-sensitive domains may prefer transparent WHOIS records.
Practical Recommendations for Domain Owners
- Comprehensive threat and exposure risk modeling aligned with domain function and profile.
- Legal compliance assessment regarding personal data display requirements.
- Operational impact analysis on abuse reporting, domain monitoring, and incident response workflows.
- Consideration of hybrid privacy approaches offering configurable masking levels or temporal privacy to balance transparency and confidentiality.
Ultimately, “Is WHOIS public?” in the domain management context is a spectrum shaped by regulatory, technical, and strategic factors. Domain owners must deliberately align privacy service use with operational goals while anticipating impacts on transparency and trust.
Combined with resilient engineering approaches to partial data, these domain management insights complete the framework for engaging WHOIS data in today’s privacy-conscious internet ecosystem.
Conclusion
WHOIS data accessibility embodies a continuous balancing act between historical transparency imperatives and modern privacy mandates like GDPR. While WHOIS remains an essential infrastructure service underpinning domain ownership verification and ecosystem accountability, it increasingly operates under selective redaction, proxy registration, and tiered access paradigms safeguarding personally identifiable information. These complexities, while critical for legal compliance and individual privacy protection, complicate security analytics, incident response workflows, and domain management processes that rely on reliable, granular ownership data.
Addressing these challenges requires multifaceted strategies—blending data aggregation from multiple WHOIS sources, intelligent caching and rate limit management, collaboration with registrars and privacy providers, and procedural frameworks enabling lawful access under stringent controls. Forward-looking system architectures must accommodate partial and heterogeneous data visibility, support flexible access models, and integrate continuous regulatory monitoring to ensure evolving compliancy.
As privacy regulations proliferate and WHOIS ecosystem participants expand globally, questions around WHOIS data transparency will intensify amid growing ecosystem scale and complexity. Engineers and architects face not just a static design problem but an evolving operational challenge: how to build WHOIS-related systems that remain resilient, auditable, and trustworthy in an environment where the boundaries of access and privacy continually shift.
Rather than viewing WHOIS as purely public or private, the sophisticated design question emerges—how can systems transparently represent and enforce the varying degrees of WHOIS data access and privacy, making these trade-offs explicit, manageable, and testable within large-scale, distributed domain management and security infrastructures?