Introduction
Suspicious domain activity seldom reveals itself through overt alerts; instead, it often conceals behind patterns embedded in registrar behaviors—bulk registrations, atypical domain transfers, or subtle WHOIS inconsistencies—that silently indicate coordinated abuse campaigns. For engineers responsible for DNS security, domain reputation, or abuse detection, these registrar-level signals represent critical operational fingerprints capable of distinguishing benign mass registrations from emerging threats.
The central challenge lies in reliably detecting these signals at scale without being overwhelmed by noise or elevated false positive rates. Changes in registrar reputation, anomalous WHOIS updates, and domain transfer timing all serve as practical telemetry points. When aggregated and correlated with DNS records and IP address mappings, they enable proactive, infrastructure-informed defenses. This article rigorously dissects these registrar patterns, illustrating how their analysis exposes suspicious domains and outlines actionable heuristics that engineers can integrate into abuse monitoring pipelines to enhance detection fidelity.
Understanding Suspicious Domain Activity and Registrar Roles
Defining Suspicious Domain Activity in Cybersecurity Context
Suspicious domain activity in cybersecurity rarely manifests as isolated flags; it typically presents as subtle, coordinated behaviors designed to evade heuristic filters or straightforward signature-based detections. Attackers deliberately exploit registrar workflows, automation loopholes, and infrastructure nuances to obfuscate their activities. Bulk domain registrations, multi-account usage across registrars and resellers, and intricate WHOIS data manipulations serve as adversarial tactics to maintain stealth and operational resilience. Recognizing these systemic patterns requires moving beyond surface indicators toward comprehensive analyses that capture the underlying abuse campaigns.
For instance, attackers distribute bulk registrations across numerous registrar accounts to circumvent rate limits or anomaly detectors implemented by domain management platforms. Automation often masks high-volume domain portfolios through minor WHOIS variations—such as changes in registrant names, subtle contact detail shifts, or toggling privacy protections—which impair attribution and blacklist generation. These “burner” domains support phishing, malware, or spam campaigns by cycling through ephemeral ownership at scale.
Operational impacts are significant: phishing infrastructure gains persistence through rapid bulk registrations and renewals; fast flux networks dynamically shift IP mappings to evade IP and DNS blacklists; malware campaigns exploit distributed hosting and registrar features to resist takedowns. An illustrative case involves credential phishing clusters leveraging registrar-enabled bulk renewals alongside lax enforcement of domain locking, enabling domains to maintain lifecycles despite IP or DNS-based screening. For a detailed case study, see Unit 42’s analysis of suspicious domain registrations.
Beyond reactive measures, these registrar-driven abstractions serve as early-warning signals that allow proactive intervention. Analyzing registration timelines, account behaviors, and WHOIS data evolution enables security teams to enact DNS or network-layer controls—such as blocking specific registrars, applying stricter resolution policies, or flagging anomalous domain groups—thereby strengthening defenses before abuse manifests. Thus, relying solely on IP or DNS blacklists underestimates domain infrastructure abuse risk, which hinges on systemic registrar workflow exploitation and WHOIS data anomalies. Conceptualizing suspicious domain activity as a structural phenomenon governed by registrar-level patterns broadens defense horizons.
The Role of Domain Registrars as Gatekeepers and Signal Sources
Domain registrars operate as pivotal intermediaries in the domain name ecosystem, tasked with registration, transfer management, WHOIS data provisioning, DNS delegation, and enforcement of domain locking. Their operational touchpoints fundamentally influence domain lifecycle events—creation, modification, and retirement—shaping the attack surface exploited in domain-based abuse.
From a forensic engineering perspective, registrars act as insightful vantage points since threat actors often favor specific registrars or reseller chains, driven by pricing, identity verification rigor, or automation capabilities. These preferences manifest as distinctive behavioral patterns detectable in registrar metadata, which serve as reliable early indicators of suspicious domain activity.
Registrar behaviors warranting scrutiny include:
- Concentrated Bulk Domain Acquisitions Within Narrow Timeframes: Registrars exhibiting bursts of hundreds or thousands of low-quality domain registrations prompt suspicion. Such volume spikes often preface phishing or malware waves. For example, the .co TLD is frequently targeted due to commercial appeal and availability, with bulk “.co” registrations correlating with wholesale abuse.
- Rapid and Inconsistent WHOIS Record Changes: Legitimate registrants rarely alter WHOIS data rapidly or frequently. Suspicious domains often toggle registrant names, contact emails, or phone numbers within days or weeks, an evasion technique complicating ownership attribution and response.
- Erratic Use of WHOIS Privacy Services: Although common and legitimate, sporadic toggling of WHOIS privacy on/off flags attempts to obstruct transparency and accountability, hindering forensic investigation.
Registrar transfer behaviors add additional abuse signals:
- Hijacking or Rogue Transfers: Attackers exploit lax transfer protocols to seize domains involved in attacks or reputation laundering.
- High-frequency Transfer Activity: Domains rapidly rotated between registrars or resellers in compressed intervals reveal “hot potato” patterns characteristic of laundering and evasion strategies.
Registrar-enforced procedural controls like domain locking significantly mitigate abuse risks by preventing unauthorized transfers, but enforcement levels vary widely. The adoption of security enhancements—two-factor authentication (2FA) for registrants or widespread DNSSEC deployment—fortifies system integrity but introduces operational trade-offs in usability and onboarding velocity.
Correlating these registrar dynamics across domain lifecycle stages (registration, modification, transfer, deletion) empowers analysts to develop comprehensive abuse detection models involving:
- Bulk registration detection tuned to temporal and account coordination.
- WHOIS anomaly detectors tracking metadata inconsistencies and privacy toggling.
- Transfer pattern analytics highlighting irregular registrar churn.
Combined, these telemetry vectors yield a systemic view surpassing traditional IP or DNS-only approaches, essential for confronting sophisticated domain abuse. For operational best practices, see Microsoft’s Investigation guidance for domains and URLs associated with alerts.
Registrar Patterns Indicative of Coordinated Abuse Campaigns
Detecting Bulk Domain Registrations and Their Operational Characteristics
Bulk domain registrations are among the earliest and most telling indicators of suspicious domain activity, particularly when orchestrated through registrars that inadvertently facilitate automated, high-velocity acquisitions. Detection begins by analyzing registrar metadata and temporal registration patterns: domains registered within compressed time windows, sharing registrant credentials or resellers, often betray automated or bot-driven processes rather than legitimate manual sign-ups.
For example, specialized bulk domain availability checkers identify domain sets sharing registration timestamps within seconds or minutes, linked to common payment methods or accounts, marking clustered activity uncommon in legitimate operations. Corporate or marketing-driven registrations typically stagger procurement over days or weeks to manage DNS propagation and operational overhead, contrasting sharply with automated bursts.
Registrar policies like rate limiting, CAPTCHA enforcement, and identity proofing normally throttle bulk acquisitions. Attackers circumvent these by exploiting registrar APIs or reseller infrastructures, distributing registrations horizontally across accounts to avoid volume-based detection. The resulting operational signature—a temporally synchronized wave dispersed across multiple accounts—becomes a key fingerprint correlated with abuse campaigns. These patterns intersect with ICANN registrar abuse policies and are well documented in security research literature.
Registrars themselves build reputations based on enforcement rigor. Some hosts and resellers exhibit consistently lax controls, easily exploited by attackers seeking persistent infrastructure. Public abuse takedown feeds frequently highlight these registrars as hotbeds of malicious domain registrations. Sophisticated assailants deliberately exploit such registrars to maximize persistence and thwart rapid takedown.
Yet bulk registration detection requires nuanced context: legitimate multi-national enterprises, conference organizers, or domain investors perform high-volume registrations, typically accompanied by stable registrant metadata and phased rollout. Contrastingly, abuse patterns feature obfuscated registrants, volatile WHOIS data, and short domain lifespans. Correlating bulk registrations with WHOIS anomalies and transfer activity therefore reduces false positives significantly.
Case studies reveal clusters of domains registered overnight by a single account and deployed rapidly for abuse before transitioning to privacy registrars for evasion—observable through registrar metadata footprints. Understanding these signatures enables security teams to flag suspicious domains early in their lifecycle, enabling timely mitigation.
Analyzing Unusual Domain Transfer Activities as Abuse Indicators
Domain transfer monitoring introduces a dynamic layer of telemetry critical for dissecting suspicious domain behavior beyond initial registrations. Legitimate domain transfers usually occur over extended periods, corresponding with corporate mergers, infrastructure realignments, or rebranding efforts. Conversely, domains involved in abuse often experience rapid transfers—moving multiple times across different registrars within days or even hours—which deviates from normal lifecycle expectations.
Such rapid churn complicates defensive efforts by confusing attribution, invalidating blocklists, and exploiting policy variations across registrars. Attackers frequently migrate domains to privacy-oriented providers—popular examples being transfers from Squarespace to Cloudflare—that offer enhanced WHOIS obfuscation and robust DNS infrastructure impeding takedown operations. For technical context, refer to the Cloudflare Privacy & Security Overview.
Empirically, registrar pairs reveal laundering heuristics: domains often shift en masse from well-regulated registrars (e.g., GoDaddy) to less restrictive or privacy-focused registrars (e.g., Epik or OrangeWebsite) following bulk registration waves. This transfer momentum is a strong operational signal of obfuscation and illicit domain trafficking.
Privacy registrars attract malicious domains by masking true registrant identities and exerting minimal compliance controls. Correlating initial bulk registration metadata with subsequent transfers to these privacy-centric registrars strengthens evidence for coordinated abuse. Typical abuse workflows show rapid transfers from known weak-validation registrars to privacy providers within hours, indicating active laundering.
Nevertheless, legitimate transfers abound in business contexts, requiring detection heuristics to incorporate transfer velocity, volume thresholds, and registrar reputational scoring to differentiate benign from malicious churn. Enrichment of domain metadata, including registration times, transfer counts, and known registrar behavior profiles, supports accurate risk scoring.
Operationally, fusion of registrar pattern analysis with transfer logs enables earlier-warning capabilities. Analysts leveraging these comprehensive views uncover abuse campaigns maintaining elevated churn, thereby elevating detection coverage beyond static metadata-based systems.
Identifying Anomalies in WHOIS Records to Reveal Domain Abuse
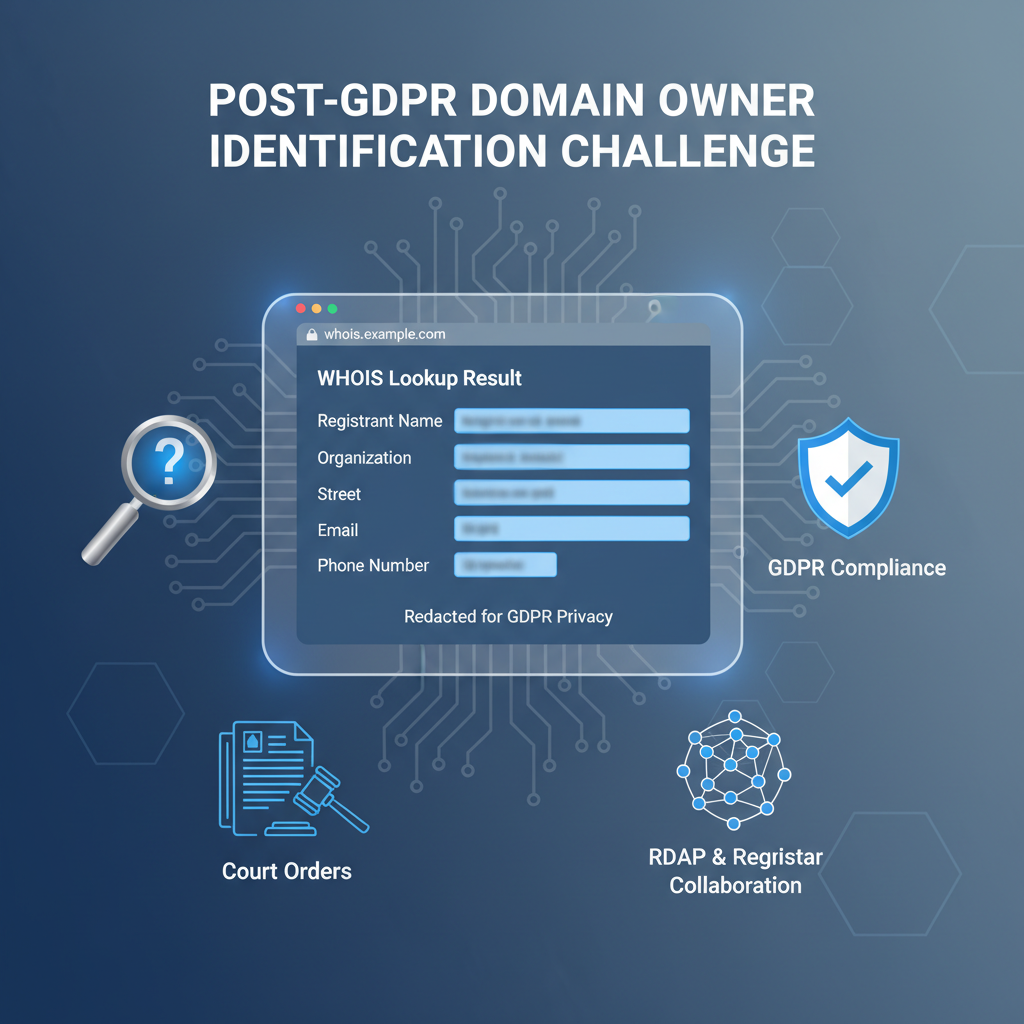
WHOIS analysis remains a foundational technique for uncovering suspicious domain activity, providing critical identity and registration metadata insights despite rising challenges from privacy service adoption and GDPR-driven data redactions. WHOIS anomalies expose the inconsistent or deceptive registration strategies characteristic of coordinated abuse.
Common red flags include inconsistent registrant details across related domains, such as discrepancies in addresses, incongruent email patterns, and unnatural organizational name variations, which suggest fabricated or virtual identities. Rapid WHOIS data churn—where registrant contact details or proxy status toggle within days—signals dynamic domain ownership evasion. Widespread proxy or privacy registrations also serve as indicators, with abuse fingerprints discovered through frequent reuse of a narrow set of privacy anonymizers or repeated masked metadata attributes.
Technical detection employs continuous WHOIS telemetry to compare live records against historic baselines stored in domain intelligence platforms. Automated systems flag abrupt, material deviations—especially within clustered bulk registrations or domains exhibiting suspicious transfer behaviors. Correlations of WHOIS update timing with registration and transfer events establish a holistic, multidimensional view of domain lifecycle volatility. Domain intelligence architectures leverage standards such as the Domain Name System (DNS) WHOIS Protocol RFC 3912 and modern telemetry frameworks to continuously monitor WHOIS.
Limitations prevail: attackers increasingly employ strong privacy providers, indistinguishable proxy metadata, or registrars with lax validation, attenuating visibility. Consequently, WHOIS anomalies alone are insufficient; their integration with registrar behavioral signals and transfer analytics increases detection robustness, producing composite indicators less vulnerable to evasion.
Operationalizing WHOIS data ingestion faces challenges including API rate limits, heterogeneous data schemas (thick vs. thin registries), and variable update frequencies across registries. Data normalization pipelines and differencing algorithms are critical for reliable anomaly extraction. Real-time monitoring requires incremental snapshot updating and temporal alignment to surface fresh anomalies promptly.
Thus, WHOIS anomaly detection provides critical situational awareness, especially when embedded within layered frameworks that combine registrar, DNS, and network intelligence to characterize and mitigate domain abuse with operational confidence.
Together, registrar patterns, transfer analyses, and WHOIS anomaly detection form an indispensable triad of signals for reliably identifying suspicious domain activity at scale, empowering security teams to build agile, precision-oriented detection systems resilient to evolving attacker tactics.
Balancing Sensitivity and Precision in Registrar Behavior Monitoring
Monitoring registrar behavior for suspicious domain activity entails managing the trade-off between high sensitivity—capturing all potential abuse—and precision—minimizing false positive alerts stemming from benign actions. Bulk domain registrations exemplify this complexity: spikes may reflect either coordinated abuse or legitimate activity such as brand protection campaigns, marketing launches, or portfolio management by legitimate investors.
Discrimination demands nuanced contextual analysis. Legitimate registrants present distinct lifecycle patterns and metadata distributions, often characterized by geographic diversity, varying contact information, and temporally distributed registrations rather than ultra-condensed bursts. Consistency in registrant WHOIS metadata (stable organization names, verified email addresses) further differentiates benign cases from attacker-driven volatility.
Detection precision improves substantially by correlating registrar data with network-level intelligence. For example, aligning bulk registrations with rapid domain-to-IP mappings pointing to suspicious infrastructure—such as fast-flux networks, command-and-control (C2) servers, or malware delivery hosts—enhances confidence in flagging malicious vectors. Efficient “domain-to-IP” resolution services integrated into registrar monitoring offer valuable operational context, enabling analysts to stack evidence prior to alert escalation. For technical background on fast-flux detection, see Cloudflare’s overview of fast-flux service networks.
Operational challenges arise from registrar policy dynamics: promotional pricing or domain giveaways induce abnormal but benign registration spikes. Similarly, evolving WHOIS visibility—affected by GDPR and privacy service adoption—injects noise into baselines for registrant traits, complicating anomaly detection. Adaptive thresholding and per-registrar historical baselining address these challenges by calibrating expectations and reducing false positives.
Misconceptions within the community about equating all registrar bulk activity with abuse exacerbate resource drains. Robust detection models incorporate features beyond volume, including timing patterns, registrar-specific historical behavior, and detailed WHOIS metadata fingerprints. Machine-learning classifiers trained on diverse datasets, encompassing legitimate bulk registrants and known threat actors, improve precision whilst preserving recall.
Large-scale platforms fusing registrar signals with DNS query patterns and IP reputation have documented 25-30% improvements in threat detection accuracy compared to volume-only approaches, alongside notable reductions in false alarms. These quantitative gains underscore the operational necessity of balancing sensitivity and precision through multi-dimensional, context-rich analysis.
Understanding and addressing these nuanced factors prepares systems to handle adversaries’ increasingly sophisticated evasion workflows and registrar variability challenges.
Limitations Due to Evasive Tactics and Registrar Cooperation Variability
As registrar-pattern-based detection matures, attackers have introduced evasive tactics that weaken attribution and signal clarity, compounded by variable registrar cooperation and regulatory constraints.
Foremost among evasions is pervasive WHOIS privacy and proxy use. Attackers mask registrant identities behind privacy layers, replacing transparent metadata with generic or obfuscated data, blunting anomaly detection reliant on WHOIS consistency. Engineering countermeasures involve integrating alternative metadata sources—such as passive DNS caches, external data brokers, or cross-regional intelligence—to infer obscured relationships.
Multi-registrar distribution further hinders detection. Attackers distribute domains across multiple registrars to avoid triggering bulk registration thresholds. Additionally, domain shuffling through rapid transfers—e.g., moving domains from Squarespace to Cloudflare—creates temporal discontinuities and data inconsistencies, complicating ownership chain reconstruction. These transfers often suffer propagation delays, causing lagged WHOIS updates and complicating timestamp-based correlation.
Domain lock mechanisms, designed to prevent unauthorized transfers, ironically provide persistence advantages to attackers by obstructing rapid takedown or seizure attempts. Delayed domain transfers further obscure chronological behavior, necessitating design of temporal uncertainty models and heuristic domain lifecycle analyses to mitigate data propagation lags.
Registrar policies themselves vary widely: some enforce stringent WHOIS validation and publication; others permit automated registrations with limited verification, amplifying opacity. This heterogeneity demands registrar-specific heuristics, adaptive normalization, and policy-aware access to comply with differing jurisdictions and privacy regulations. Refer to ICANN’s WHOIS and GDPR FAQ for regulatory guidance.
Real-world edge cases—such as legitimate but complex domain repurposing or chained redirections—introduce ambiguity in registrar-derived signals. For example, legitimate “nextcloud” deployments routed through untrusted domains may superficially resemble suspect behavior, indicating limits in using registrar data for conclusive attribution.
Therefore, robust detection architectures treat registrar analytics as one facet within layered defense stacks, integrating registrar data with passive DNS observations, forwarding and redirect analyses, domain name system port inspections, and network traffic metadata. This fusion enhances resilience against evasion and increases accuracy.
Collaboration with registrars to enhance WHOIS transparency and accelerate abuse response remains difficult, impeded by privacy laws and jurisdictional variability, underscoring the need for multi-stakeholder models and trust frameworks.
Acknowledging these constraints is essential for engineering scalable, effective suspicious domain detection solutions. The interplay of attacker sophistication, registrar variability, and technical complexity mandates continuous innovation and operational flexibility to sustain defense efficacy in the evolving domain abuse landscape.
Operationalizing Registrar Pattern Detection in Abuse Monitoring Systems
Developing Practical Heuristics for Registrar Pattern Alerts
To detect suspicious domain activity via registrar analysis, engineers must craft heuristic rules that coherently combine multiple registrar-centric signals for precise, actionable alerts. This multi-factor approach overcomes the shortcomings of isolated indicators.
Registration volume analysis remains foundational. Tracking domain registration counts per registrar within defined temporal windows—hourly, daily, or event-driven intervals—provides early warning of suspicious bulk campaigns. Characterizing bursts is essential: sharp, dense spikes often indicate automated bot activity, whereas steadier elevated registration rates may reflect semi-coordinated abuse. Effective heuristics incorporate adaptive baselines modeling normal registrar throughput to mitigate spurious alerts.
Volume data alone lacks context. WHOIS anomaly detection supplies essential corroboration. Irregularities encompassing heavy use of privacy services, conflicting registrant details across domains registered concurrently or in short succession, and rapid, repeated WHOIS updates (e.g., registrant name/email rotation) significantly elevate suspicion. Achieving reliable WHOIS parsing necessitates flexible normalization techniques that reconcile heterogeneous registry schemas, thick/thin records, and privacy-related masking, especially under regulatory influences such as GDPR and CCPA. Refer to the ICANN WHOIS Accuracy Specification for standardization guidance.
Transfer timing and pattern analytics add critical operational dimension. Rapid transfers involving registrars with histories of lenient enforcement often signify laundering or evasive behavior. Tracking “transfer chains”—multiple sequential registrar hops within narrow timeframes—helps identify obfuscation. Incorporating velocity and flagged registrar lists into heuristics refines alert accuracy.
Compound heuristics utilize threshold combinations; for instance, triggering alerts when a registrar logs over X registrations in N hours concurrently with Z% of those domains exhibiting WHOIS anomalies or excessive transfers. Confidence scoring based on weighted signal fusion prioritizes alerts for investigation. While machine learning can enhance these models, interpretability and threshold-based logic remain vital for operational transparency.
Scaling heuristic execution in streaming or near-real-time batch pipelines is critical to handle high domain registration throughput. Automated triage pre-filters high-confidence signals, while adaptive feedback loops incorporating analyst input enable dynamic tuning to maintain precision. Complementary tooling—such as bulk domain availability checkers and enriched domain management platforms—supports longitudinal pattern analysis and retrospective investigations.
In practice, heuristic fusion outperforms single-factor signals, balancing recall and false-positive mitigation. Challenges remain in noisy WHOIS data, incomplete transfer records, and adaptive attacker mimicry. Nonetheless, a robust heuristic layer forms the operational foundation for registrar-centric detection.
Next, integrating registrar heuristics with other Internet telemetry amplifies detection effectiveness.
Enhancing Detection Accuracy by Linking Registrar Data to DNS and Network Signals
Elevating registrar pattern detection by integrating DNS and network telemetry delivers multi-layered insights into suspicious domain activity, mitigating false positives and enabling richer contextual understanding of domain abuse.
A principal integration vector is DNS record correlation. Monitoring DNS resource record evolution (A, CNAME, MX, TXT) for registrar-flagged domains helps substantiate or refute abuse hypotheses. For example, bulk-registered domains resolving rapidly to limited IP ranges—often associated with bulletproof hosting or VPN exit nodes—strengthen suspicion. Abrupt mass DNS changes, such as synchronous CNAME redirections to phishing infrastructure, further indicate operational coordination. Historical DNS trail analysis enables evaluators to dissect domain footprint evolution and actor tactics.
Mapping flagged domains to resolved IP addresses exposes clustering and infrastructure relationships. IP ranges linked to lax hosting providers or known malicious operations reveal supply chains enabling abuse. Integration with threat feeds scoring IP reputations adds further signal refinement.
Engineering scalable data pipelines demands normalization and timestamp alignment across registrar logs, WHOIS snapshots, DNS zone change histories, and network reputation feeds. Deduplication ensures concurrency when overlapping events surface from multiple data sources. Streaming architectures using message brokers (e.g., Kafka) paired with real-time processing frameworks (e.g., Apache Flink, Spark Streaming) balance latency and throughput demands. Consistent normalization across registrar IDs, WHOIS fields, DNS types, and IP geolocations underpins unified models enabling multi-dimensional correlation with fast query capabilities. See Apache Flink documentation for streaming architecture patterns applicable to security telemetry.
Coordinator registration campaigns exhibit complex technical hallmarks discoverable only via cross-layer correlation: synchronized registration bursts with uniform WHOIS proxy usage, sequential domain transfers funneling into bulletproof hosting IP ranges, and mass DNS record shifts within tight windows form composite operational fingerprints distinct from legitimate high-volume registration. Disjointed analyses of registrar or DNS data alone often fail to detect such intricate abuse workflows.
These integrations introduce operational trade-offs. Comprehensive correlation is resource-intensive and may increase alert latency. Organizations commonly implement tiered processing: initial heuristics produce broad rapid alerts, deeper asynchronous correlation applies to prioritized subsets, optimizing analyst resource allocation.
Illustrative use cases include ad fraud operations: tens of thousands of bulk-registered domains at a mid-tier registrar flagged via volume heuristics, whose DNS mappings revealed resolution to known hostile bulletproof host IPs. Integrated telemetry enabled targeted interventions minimizing collateral impact, unattainable through registrar or DNS analysis in isolation.
Conclusively, effective suspicious domain detection requires fusion of registrar, DNS, and network signals, establishing a multi-dimensional attacker behavior model with actionable outputs that accelerate response cycles.
Embedding Registrar Pattern Detection in Abuse Response and Threat Intelligence
Registrar pattern detection achieves its highest operational value when embedded within integrated abuse response and threat intelligence ecosystems, facilitating streamlined mitigation workflows and enriching investigation capabilities.
One approach involves feeding heuristic-generated registrar pattern alerts into Security Information and Event Management (SIEM) systems or threat intelligence platforms as enriched events or contextual indicators. These signals augment analytic pipelines by correlating with internal telemetry and external feeds, expediting detection of domain abuse impacting enterprise environments. Real-time ingestion enables automated blocking, alerting, or registrar-level escalation workflows based on preconfigured policies.
Complementary domain investigation tooling enhances analyst productivity. Tools that aggregate domain forwarding data, historical DNS records, registrant attribute timelines, and lock status enable contextual enrichment, aiding attribution and uncovering attack chain relationships. For example, exploring historical DNS changes elucidates redirection infrastructures and domain dependencies, while registrar status audits help detect registrar change patterns indicating laundering or hijacking.
Operational case studies validate impact: enterprises employing automated heuristics combined with DNS enrichment and SIEM integration reported a 35% reduction in analyst investigation time alongside accelerated abuse escalations to registrar abuse teams. Resulting enforcement—including targeted blocking and coordinated takedown efforts—curtailed attacker domain lifecycle significantly.
Complex cases involving multi-registrar forwarding or chained redirection require sophisticated response workflows. Attackers leverage layered forwarding setups to obscure ownership and complicate detection. Response tooling integrating domain namespace diagrams and forwarding trees offers critical context to distinguish benign intermediaries from malicious endpoints, minimizing false positives and focus maintenance.
Embedding registrar heuristic alerts in comprehensive response ecosystems elevates security posture by accelerating detection, enhancing triage precision, and enabling surgical mitigation prior to operational impact. Coupled with domain forwarding visualization and investigative tooling, it fosters overall domain abuse defense maturity, measurable in reduced time-to-detection and operational risk exposure.
Operationalizing registrar pattern detection embodies a cornerstone of modern layered defense—melding heuristics, telemetry fusion, and response integration to counter increasingly sophisticated domain abuse tactics effectively.
Key Takeaways
Suspicious domain activity frequently originates from nuanced registrar behaviors, bulk registration surges, and WHOIS metadata anomalies. For engineers tasked with DNS infrastructure security or abuse detection system design, mastering these patterns is imperative to architect resilient, proactive defenses that preempt domain-based threats.
- Registrar behavior as abuse vector indicators: Unexpected spikes in registrations or reliance on registrars with weak controls reflect trade-offs between cost, anonymity, and abuse risk, shaping detection heuristics calibrated to registrar reputation.
- Bulk registration detection refines abuse signal precision: Identifying temporally clustered domain sets sharing WHOIS or payment attributes enhances detection but demands scalable heuristics optimized to minimize false positives.
- WHOIS anomalies reveal coordinated registration campaigns: Patterns of inconsistent, incomplete, or templated WHOIS data expose automated abuse attempts, underscoring the need for structured anomaly detection over mere content inspection.
- Registrar transfer patterns uncover domain hijacking and obfuscation: Monitoring rapid or bulk transfers, such as from Squarespace to Cloudflare or GoDaddy, exposes laundering efforts, reinforcing the value of integrating transfer logs into abuse workflows.
- Domain-to-IP mapping correlation aids threat attribution: Resolving suspicious domains to IPs and analyzing host infrastructure differentiates benign bulk registrations from malicious campaign assets.
- Domain locking presents a critical defensive control: Registrar lock status monitoring prevents unauthorized transfers and surfaces hijacking attempts, adding operational insight.
- DNS record and port analysis identify malicious infrastructure: Examining DNS resource records and port exposure across large domain sets reveals templated configurations characteristic of abuse campaigns.
- Balancing privacy and observability in WHOIS data: GDPR and privacy service adoption obfuscate registrant data, compelling adaptive heuristics cognizant of regulatory constraints.
These insights form the foundation for engineering high-fidelity domain reputation intelligence and incident response workflows, enabling security teams to outpace increasingly evasive adversaries.
Conclusion
Effectively detecting and mitigating suspicious domain activity demands a comprehensive, multi-dimensional understanding of registrar behaviors, transfer dynamics, and WHOIS anomalies augmented by DNS and network telemetry. Transitioning from simplistic volume-based triggers to nuanced heuristic models enriched by cross-layer data significantly improves detection accuracy, reducing false positives and accelerating response.
This layered approach counters advanced attacker tactics—such as domain shuffling, privacy masking, and registrar erosion—while accommodating registrar heterogeneity and evolving regulatory landscapes. Embedding these signals within integrated threat intelligence and abuse response systems facilitates rapid triage and containment, crucial for maintaining the integrity of the Internet’s naming system.
Looking forward, as domain infrastructures scale and attackers adopt increasingly distributed and automated methods, engineering systems capable of adaptive, real-time behavioral analysis anchored in registrar-level signals will be essential. The challenge lies not only in detection but in designing observability, validation, and response frameworks adaptable to dynamic attacker techniques, system growth, and regulatory flux. The decisive question becomes: how can security architectures evolve to make registrar pattern detection transparent, explainable, and operationally robust beneath growing complexity and scale?