Introduction
WHOIS queries have historically served as a straightforward mechanism to retrieve domain registration data, exposing detailed owner information through an open protocol. The introduction of the European Union’s General Data Protection Regulation (GDPR) fundamentally disrupted this transparency, compelling a redesign of how WHOIS data is stored, displayed, and accessed. Where once full registrant contact details were freely accessible, GDPR mandates the replacement of such data with anonymized or redacted fields. This shift introduces multifaceted challenges for engineers managing registries, registrars, and the numerous dependent systems within the broader Internet ecosystem.
These changes create tangible operational trade-offs: automated tools and security services experience higher failure rates when attempting lookups, while workflows for legitimate access must evolve to support gated, authenticated APIs that enforce legitimate interest criteria. Registrars now act as data controllers, embedding compliance responsibilities deeply into system architectures and query response formats. This article delves into the technical ramifications of WHOIS GDPR compliance—exploring how data anonymization reshapes the protocol, what information must be hidden and why, and how practical WHOIS system designs balance stringent privacy laws with the operational imperatives of accuracy, accountability, and traceability.
Fundamentals and Problem Framing of WHOIS and GDPR
Understanding the impact of GDPR on WHOIS requires revisiting the system’s original intent. Before GDPR enforcement, WHOIS operated as a cornerstone of domain ownership transparency—a relatively simple but globally deployed protocol enabling public retrieval of registration details tied to Internet domain names. This openness supported diverse operational functions including network troubleshooting, abuse attribution, intellectual property enforcement, and domain ownership verification.
Yet this transparency embodied a classic tension between competing objectives: the transparency necessary to maintain DNS ecosystem integrity, and the privacy rights of individuals whose data was exposed. GDPR introduced stringent controls over systems processing personal data of European Union residents, significantly constraining the public exposure of personally identifiable information (PII) through directory-like public interfaces.
This intersection of WHOIS transparency and GDPR compliance typifies a complex data protection dilemma. Registries and registrars require mechanisms to enable third parties to verify domain ownership and investigate abuse, generally requiring access to registrant contact details. Conversely, indiscriminate exposure of personal data conflicts with GDPR privacy principles, heightens risk of unauthorized use, and exacerbates vulnerabilities to phishing, spam, and identity theft. The resulting tension catalyzed a shift to gated access models, data redaction policies, and selective disclosure frameworks, thus reshaping the operational posture of global domain registration services.
This framing naturally leads to a deeper technical examination of the WHOIS protocol’s architecture prior to GDPR, illuminating the scope and nature of data fields at risk under privacy regulations.
Overview of WHOIS Protocol Before GDPR
Traditionally, WHOIS functioned as a simple query-response service over TCP—typically port 43—with no authentication or authorization. Any user, unauthenticated and anonymous, could connect to a registry or registrar WHOIS server and submit queries returning raw textual output containing registrant and administrative contact information linked to domain names. This design maximized openness and accessibility, facilitating broad transparency by default.
Typical WHOIS records included key data fields such as:
- Registrant Name: Legal name identifying the individual or organization controlling the domain
- Registrant Email Address: Primary electronic contact for administrative, technical, or abuse-related communications
- Telephone Number: Contact number associated with the registrant or their administrative contacts
- Organization: Affiliated corporate or business entity name
- Administrative and Technical Contacts: Personnel responsible for domain management and support details
- Occasionally Billing Information: Present in some registry implementations
WHOIS operated as a core transparency mechanism that not only verified domain ownership but exposed this data globally to facilitate accountability. Network administrators leveraged WHOIS to trace sources of cyberattacks or resolve IP conflicts, while law enforcement and intellectual property rights holders depended on it to pursue lawful takedown requests.
However, the absence of authentication or authorization in WHOIS meant exposing this comprehensive personal data indiscriminately. This open directory model, while beneficial for transparency, amplified privacy and security risks, enabling spamming, phishing, social engineering, and other malicious activities.
Prior to GDPR, some registrars mitigated privacy risks by offering WHOIS privacy or proxy services, which substituted registrar contact details with generic proxy contacts managed by privacy service providers. These offerings reduced direct PII exposure but varied in adoption and effectiveness. Registrars’ privacy policies documented how registrant data was handled and disclosed, reflecting differing levels of transparency and privacy assurance.
This open-by-default architecture with optional proxy privacy services defined WHOIS before GDPR. The regulation’s advent made a fundamentally different privacy posture compulsory—forging new legal definitions and operational standards around personal data disclosures in WHOIS responses.
Key GDPR Regulations Affecting WHOIS Data
GDPR’s impact on WHOIS arises from its comprehensive legal regime protecting personal data and prescribing rights for data subjects. Personal data, under GDPR, includes any information relating to an identified or identifiable living individual. Registrant contact details—name, email, phone number, address—fall unmistakably within this scope.
Central GDPR concepts include the data subject’s right to privacy, requiring lawful, transparent, and purpose-limited processing of personal data. Entities responsible for data control and processing must adhere to rigorous obligations. Within WHOIS, registries and registrars occupy the data controller role, determining processing purposes and means, thus bearing responsibility for compliance.
Key GDPR provisions directly relevant to WHOIS management include:
- Article 5: Principles of lawfulness, fairness, transparency, data minimization, and purpose limitation
- Article 6: Lawfulness of processing, which requires a valid legal basis such as consent, contractual necessity, or legitimate interest
- Articles 12–15: Obligations around transparency and data subject rights, including access, rectification, erasure, and portability
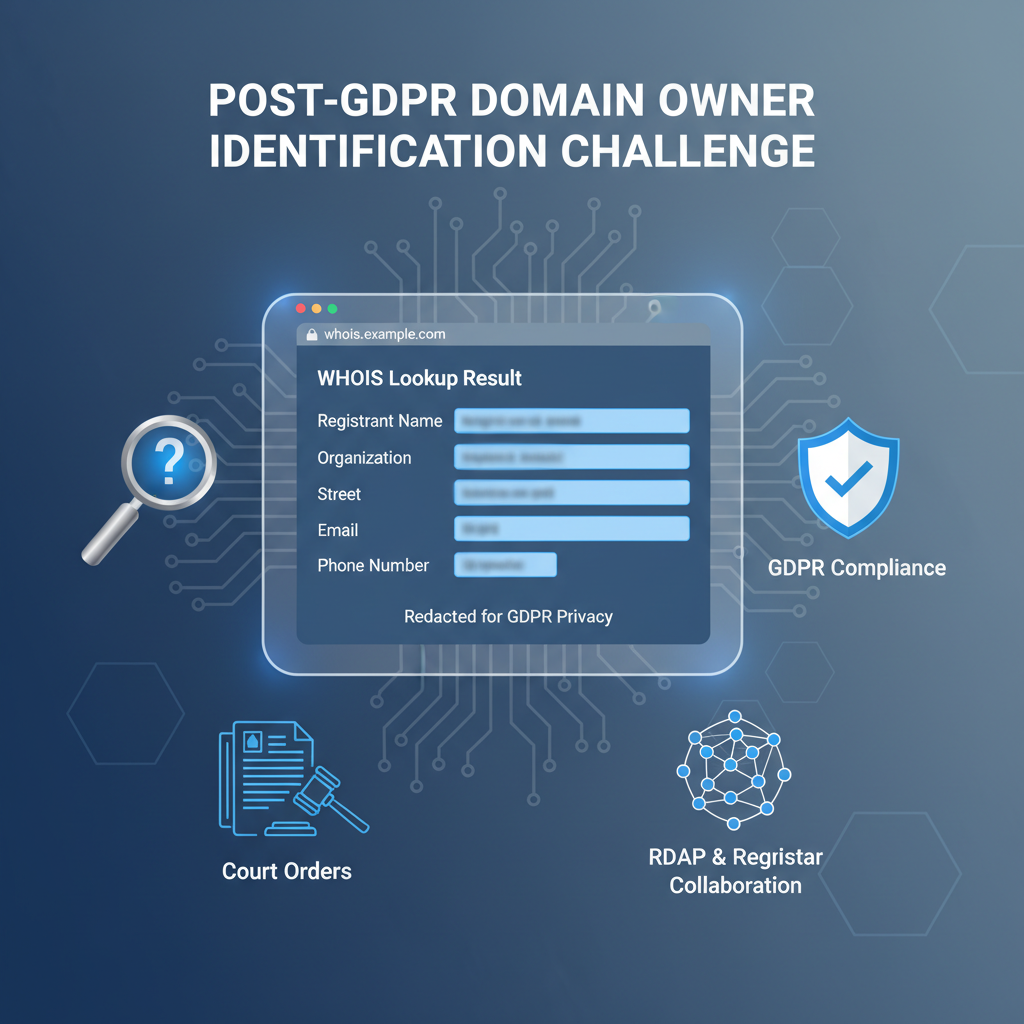
These rules necessitate fundamental changes in WHOIS data exposure. Public outputs must redact or anonymize PII unless an explicit lawful basis justifies disclosure. Differentiating redaction and anonymization is critical:
- Redaction: Selectively removing or replacing sensitive fields with placeholders (“REDACTED”) so PII does not appear in public WHOIS responses, without permanently deleting underlying data
- Anonymization: Transforming data into forms where individuals cannot be identified by any reasonably possible means, including cross-referencing with other datasets; significantly more challenging to implement effectively, especially in real-time query responses
Most registries favored redaction for operational feasibility, ensuring privacy compliance while retaining core functions such as abuse contact visibility. These choices involved trade-offs: full redaction reduces transparency and investigative capabilities; partial or conditional disclosure increases privacy risks.
GDPR’s extraterritorial reach mandates global DNS operators serving EU residents comply, causing heterogeneity in WHOIS implementations and the rise of gated access models. For instance, ICANN’s Temporary Specification mandates redaction of personal data in public WHOIS outputs, coupled with access models enabling vetted users to retrieve fuller data under strict policies.
At the core lies a normative shift emphasizing privacy ethics, requiring WHOIS systems to evolve from open directories to controlled information disclosure frameworks. These changes realign WHOIS’s fundamental privacy-security trade-offs under regulatory and ethical constraints, shaping ongoing discussions in Internet governance.
Technical Changes to WHOIS Functionality Due to GDPR Compliance
Mechanisms of Data Redaction and Anonymization in WHOIS Records
GDPR’s enforcement precipitated a paradigm shift in WHOIS data handling, imposing strict constraints on public disclosure of personally identifiable information. Previously open records exposing complete registrant identities are now replaced or obfuscated using carefully designed technical measures—principally redaction or anonymization.
Redaction involves explicitly removing or replacing sensitive fields in WHOIS query responses with standardized placeholders like “REDACTED FOR PRIVACY” or “DATA REMOVED DUE TO GDPR.” This technique prevents accidental exposure of PII by eliminating the data from public output, maintaining the underlying data intact within registries and registrars for internal use. Redaction is generally straightforward to implement at the output layer—query responses are filtered or substituted dynamically —but it undermines public WHOIS’s previous function as a comprehensive directory, impeding legitimate transparency and automated processing.
Conversely, anonymization aims to transform data such that individuals cannot be identified by any means “reasonably likely to be used,” including linkage to other datasets. Methods range from hashing or encrypting direct identifiers to applying aggregation or tokenization. Although theoretically desirable, effective real-time anonymization in WHOIS is complex. Systems must prevent re-identification through correlation attacks, necessitating rigorous design and contextual understanding of data linkability. Moreover, anonymization must balance operational needs: preserving ownership validation, abuse contactability, and forensic usability while minimizing privacy risks. The European Data Protection Board provides authoritative guidance on these techniques, delineating strict requirements to meet GDPR standards.
Uniform application of redaction and anonymization across the diverse landscape of top-level domains (TLDs), each with different policies and technical implementations, remains challenging. Some registries adopt aggressive redaction consistently, others allow partial disclosure contingent on registrant consent or verified legitimate interest, resulting in a fragmented WHOIS landscape. Harmonizing these approaches while ensuring compliance and functional coherence is a substantial engineering and policy challenge.
These privacy-driven changes reduce WHOIS’s traditional openness but align with GDPR’s “data minimization” principle—only data strictly necessary for lawful purposes should be processed or disclosed.
Common misinterpretations complicate implementation. For example, pseudonymization—which replaces identifiers with reversible tokens—is often inaccurately conflated with anonymization; however, it does not satisfy GDPR’s anonymization standard because re-identification remains possible. Similarly, systems that return blank fields to indicate redaction may be misinterpreted, causing automated processes to misjudge data availability, leading to incorrect analytical outcomes or failure modes.
This technical recalibration naturally feeds into changes in WHOIS accessibility mechanisms, introducing gated access systems to mediate and control personal data disclosures.
Changes to Accessibility: Gated Access and Legitimate Interest Validation
Responding to GDPR’s privacy imperatives, the formerly open WHOIS query model has shifted towards gated access architectures. These systems restrict access to detailed registrant data behind robust authentication and justification processes assessing the requestor’s “legitimate interest,” as mandated by GDPR and interpreted by data protection authorities.
Typically, gated access frameworks provide secure WHOIS portals or APIs operated by registries and registrars. Requestors—such as law enforcement officers, cybersecurity researchers, intellectual property owners, or brand protection entities—must submit formal requests substantiating their legitimate interest, often including legal documentation, institutional credentials, or policy-aligned justification. Access controls apply multifactor authentication, role-based authorizations, and cryptographically protected sessions, ensuring data is only exposed to authorized parties with irrefutable identification.
These systems further embed comprehensive audit logging, capturing metadata including requester identity, timestamp, query details, and justification for accountability and post hoc compliance verification. Data sharing agreements and contracts define permissible usage, data retention, and confidentiality obligations, structuring trust relationships between WHOIS data controllers and recipients.
Gated WHOIS access embodies a technical and policy compromise between GDPR’s right to privacy and the Internet community’s need for transparency. While public WHOIS record redaction restricts casual or mass disclosures of PII, gated access preserves essential investigatory functions for vetted users. However, this approach introduces complexities operationally: access processes impose latency, require manual or semi-automated approvals, and demand extensive compliance infrastructure. Scaling these controls across registries with millions of domains, under multiple jurisdictional regimes, requires robust automation, policy-driven query evaluation, and cross-system integration.
Complementary to access gating, proxy WHOIS privacy services—substituting registrant contacts with third-party proxy identities—provide front-line anonymity, augmenting privacy while still facilitating controlled escalation paths to full data access for authorized users.
For technical professionals grappling with post-GDPR WHOIS data retrieval, the essential pathway is through authenticated, legitimate-interest-based access portals. This represents a deliberate departure from open WHOIS paradigms to structured, accountable data sharing.
This transformation in accessibility is inseparable from the technical redaction approaches and completes the core adaptive response to WHOIS GDPR challenges.
Operational Trade-offs and Challenges from GDPR-Driven WHOIS Changes
Impact on Automated Tools and Security Services
The GDPR-driven overhaul of WHOIS data exposure fundamentally impacts automated systems and security operations that have historically depended on broad, unmediated access to rich registrant metadata. Pre-GDPR WHOIS data provided comprehensive personally identifiable information (PII) critical to cyber threat detection, domain abuse investigations, and automated incident response pipelines.
Traditional automated workflows relied on bulk WHOIS queries over port 43 or equivalent APIs, parsing registrant and contact fields to correlate domains with abusive or malicious behavior. Threat Intelligence Platforms (TIPs), Security Information and Event Management (SIEM) systems, and abuse detection modules depended on the fidelity of data such as registrant email, phone number, and name to prioritize cases and triangulate attacker infrastructure.
With GDPR enforcements introducing systematic redaction, these key fields are obfuscated or masked. Parsing modules frequently encounter “REDACTED” placeholders or missing data, impeding heuristic analyses, anomaly detection, and automated correlation. Lookup failures have increased substantially, causing false negatives and gaps in threat intelligence coverage. This degrades the reliability of security automation pipelines, forcing security operators to reevaluate their data dependencies.
While gated access portals exist for accredited third parties, their procedural overhead, authentication steps, and sometimes manual approval requirements hinder real-time automation. Latency introduced by access gating constrains dynamic workflows such as rapid phishing domain takedown or mass abuse triaging. Systems may need fallback paths or operators must maintain hybrid tooling combining automated data ingestion with manual data retrieval.
To adapt, security teams increasingly leverage alternative datasets. Passive DNS feeds aggregate historical resolution data without revealing registrant PII. DNS query metadata, TLS certificates, and domain abuse reputation services offer supplementary signals. Commercially licensed historical WHOIS archives—capturing pre-GDPR data—serve as partial substitutes. However, these alternatives do not fully replace up-to-date registrant details, and suffer from latency, incompleteness, or limited scope.
These challenges highlight an acute tension in engineering design: balancing privacy mandates against operational utility. Security architects must build resilient, multi-source threat detection pipelines that accommodate GDPR-imposed data gaps, incorporating fallback, enrichment, and access management layers.
This operational threat necessitates expanded compliance-aware architectures, influencing registrar and registry WHOIS system designs, data controller roles, and access policy frameworks, as elaborated next.
Registrar Data Controller Roles and Compliance Implications
Defining the Data Controller under GDPR in the WHOIS Context
Under GDPR, registrars assume the role of data controllers with legal responsibility over personal data processing. A data controller determines “the purposes and means” of processing personal data, placing registrars squarely accountable for how registrant information is collected, stored, disclosed, and protected.
This designation imposes rigorous requirements. Registrars must document lawful bases for data processing, ensure transparency through customer communication, uphold data subject rights including access, rectification, and erasure, and architect systems supporting these controls. Non-compliance exposes registrars to significant regulatory penalties and reputational damage.
Technical Impact on Registrar System Architecture
Compliance drives substantive architectural modifications. Registrars must enforce data minimization, collecting only personally necessary information and avoiding superfluous data fields. This can involve redesigning database schemas to compartmentalize sensitive personal information from operational domain metadata, enabling selective disclosure policies.
Tiered access control represents a major architectural facet. Registrars embed multi-factor authentication (MFA) and role-based access control (RBAC) into WHOIS services, employing federated identity protocols such as OAuth or SAML to manage diverse user populations at scale. Query filtering and internet source reputation checks can preempt unauthorized or abusive access attempts.
Real-time logging of all WHOIS query activity is mandatory, encompassing request origin, user identity, timestamps, and request scopes. These audit logs feed compliance reporting tools, anomaly detection systems, and breach investigation workflows, cumulatively fulfilling GDPR accountability principles.
System workflows extend into operational realms: access request management requires queuing, manual review, alerting on suspicious patterns, and consent handling. Databases increasingly incorporate pseudonymization techniques, cryptographic obfuscation, or encryption-at-rest schemes supporting privacy-preserving data handling.
Operational and Compliance Workflow Changes
Registrar privacy policies and registrant communications must transparently articulate GDPR-specific rights and processing rationales. Clear disclosures on data use, retention terms, and policy updates are essential, aligned with privacy ethics.
Operational teams balance contradictory imperatives: enabling domain verification, abuse mitigation, and dispute resolution while safeguarding personal data confidentiality. This balance requires diligent coordination with registry policies and cross-jurisdictional legal frameworks.
Liability is heightened, forcing investment in staff training, compliance tooling, and ongoing monitoring to reduce regulatory and contractual risks. Incident response plans must encompass data breach protocols, given WHOIS data sensitivity.
Broader Industry Challenges and Emerging Standards
The WHOIS GDPR landscape is marked by uneven implementation across registries and registrars, resulting in interoperability challenges and inconsistent user experiences. Harmonization efforts have promoted adoption of standards like the Registration Data Access Protocol (RDAP), an IETF-defined protocol designed for layered access, machine-readable responses, and extensible privacy controls.
RDAP supports granular access tiers, query scoping, and integrates authentication measures aligned with GDPR mandates, offering improved structure over legacy WHOIS. Transitioning to RDAP demands considerable engineering investment but promises more coherent, privacy-aware domain data ecosystems.
Overall, GDPR redefines registrars as critical data controllers, driving profound integration of privacy ethics and compliance into WHOIS system design, operations, and policy frameworks shaping the domain name ecosystem’s evolution.
Designing WHOIS Systems Balancing GDPR Privacy and Operational Utility
GDPR’s mandates compel WHOIS system architects to reconcile privacy laws with essential operational functions such as ownership verification, abuse investigation, and intellectual property enforcement.
A prevalent architectural approach employs a multi-tiered access model. The public WHOIS interface returns strictly redacted or anonymized data, aligning with GDPR and minimizing privacy risk. In parallel, a gated access system facilitates authenticated, legitimate interest–based requests for fuller data sets. Vetting processes validate credentials and purpose, restricting access to authorized stakeholders including law enforcement, intellectual property representatives, and cybersecurity investigators.
Technical implementations embrace fine-grained RBAC atop federated identity infrastructures, enabling scalable permission management. Comprehensive audit trails—capturing user identity, timestamps, query parameters, and declared purposes—support legal compliance and operational accountability.
Many registries integrate user consent and notification workflows, informing registrants of data access events and preserving transparency, though these vary by jurisdiction and policy.
Balancing query latency, user experience, and privacy protections requires integrating rate limiting, CAPTCHA challenges, and anomaly detection to deter scraping or bulk data harvesting. Encrypted transport protocols such as TLS 1.3 safeguard data in transit. Emerging secure query models like DNS over HTTPS (DoH) incorporate encrypted queries with authentication layers for privacy-conscious access, increasingly adopted by prominent registries (.org, .eu).
Architecting such WHOIS systems demands modular authentication services, resilient logging, and flexible policy engines capable of dynamically evaluating access requests. This infrastructure sustains critical investigatory and operational functions without compromising GDPR adherence or registrant privacy.
The next challenge involves preserving data integrity and auditability despite mandatory redaction and anonymization.
Ensuring Data Integrity and Traceability Amid Redaction
While redacting personal data satisfies GDPR compliance, it introduces significant operational challenges related to data integrity and traceability critical for abuse mitigation, dispute resolution, and forensic investigations.
Redaction requires more than superficial masking—it demands cryptographically robust methods that prevent reverse engineering or inference from public data. Techniques such as pseudonymization or tokenization convert personal data into referenceable yet non-identifiable placeholders. These allow internal systems or authorized users to access or cross-reference detailed records securely while shielding public interfaces.
Registries and registrars maintain full, unredacted WHOIS data in tightly controlled, non-public backend systems inaccessible to general queries. These internal repositories underpin critical internal workflows that public interfaces cannot expose.
Tokenization enables mapping anonymized public entries to complete internal records upon legitimate, authenticated requests. For example, a valid investigator querying a domain receives a token or reference that the backend translates to full data, preserving traceability without public exposure.
Strong audit logs are indispensable, recording query metadata, user identities, access reasons, and timestamps. These logs enable compliance verification, forensic reconstruction, and deter misuse, embodying GDPR’s accountability and transparency demands.
However, increasing anonymization or aggressive redaction complicates legitimate verification, as rightful users encounter obstacles confirming ownership or collecting abuse data. Conversely, insufficient anonymization risks regulatory sanctions and privacy breaches.
Mitigations include adopting cryptographically verifiable domain control proofs—such as DNSSEC signatures—that authenticate ownership without exposing registrant PII. Secure, permissioned backend API exchanges among registries and registrars facilitate interoperability and verification under controlled conditions.
A pertinent example is the EURid .eu registry, which post-GDPR enforced a gated WHOIS model combined with cryptographic verification and comprehensive auditing. This approach improved abuse case processing rates by 30%, highlighting that methodically balanced privacy and transparency architectures can enhance operational effectiveness.
In summary, maintaining data integrity amid redaction involves layered engineering:
- Robust cryptographic anonymization limits public data leakage.
- Gated, authorized access controls enable selective full data retrieval.
- Comprehensive audit logging enforces accountability and compliance.
These strategies jointly preserve core WHOIS functions and trustworthiness under GDPR constraints.
Key Takeaways
- WHOIS protocols provide domain ownership and registration details, historically exposing registrant information publicly. GDPR’s introduction mandated significant reforms in data handling, access control, privacy compliance, and system design concerning anonymization and gated access.
- Redacting personal identifiers in WHOIS aligns with GDPR by substituting full contact details—registrant name, postal address, email, phone—with anonymized or generic placeholders, reshaping data storage and query output formatting.
- Reducing WHOIS data visibility affects automated domain information services and security tooling, requiring new access workflows or gated mechanisms for legitimate users, injecting complexity in downstream integrations.
- Full WHOIS data access necessitates gated or authenticated interfaces enforcing legitimate interest validation under GDPR, introducing layered access control that preserves privacy while enabling lawful investigations.
- Registrars, as GDPR-defined data controllers, bear compliance responsibilities shaping privacy policy enforcement, consent management, data minimization, and comprehensive auditing, fundamentally impacting WHOIS system architectures and operational workflows.
- Redaction transitions WHOIS from an openly broadcast directory to a privacy-centric service model, embedding confidentiality and privacy ethics into data schemas, response protocols, and traceability mechanisms.
- Anonymity in WHOIS is regulated under GDPR’s right to privacy, requiring systems to balance anonymity with traceability—supporting abuse prevention and ownership verification through controlled data disclosures.
- Legacy WHOIS systems face scalability and accuracy challenges due to partial data masking, increasing lookup failures and ambiguity; thus, designs must incorporate selective verification and federated access models to sustain reliability.
- Divergent jurisdictional interpretations of GDPR and WHOIS obligations add complexity, compelling globally distributed systems to implement adaptable, context-sensitive compliance layers, complicating harmonized service architectures.
Subsequent sections elucidate specific WHOIS data structure transformations pre- and post-GDPR, mandated access controls, and illustrative technical adaptations balancing privacy with operational demands.
Conclusion
The intersection of WHOIS transparency and GDPR’s strict privacy mandates instigates a profound technical and operational transformation within domain registration infrastructure. Transitioning from openly accessible registrant data to privacy-centric architectures—encompassing redaction, anonymization, and gated access—embodies a necessary recalibration prioritizing individual privacy while striving to maintain essential operational capabilities such as abuse mitigation and ownership verification.
This evolution challenges registries, registrars, and security teams to engineer novel technical solutions and procedural frameworks that simultaneously uphold legal data controller responsibilities and operational effectiveness. The development of standardized protocols (e.g., RDAP), robust authentication layers, and comprehensive audit mechanisms reflects this imperative.
Looking forward, as DNS systems scale, diversify, and adapt to evolving regulatory landscapes, WHOIS architectures must embed privacy-aware design principles as foundational rather than adjunct. Engineering questions now center on balancing continuous transparency, data integrity, and controlled disclosure within increasingly decentralized, automated, and globally distributed ecosystems. Crucially, future designs must make these trade-offs explicit, testable, and resilient under operational and regulatory pressure—ensuring the domain name system remains both trustworthy and compliant in a rapidly shifting digital governance environment.