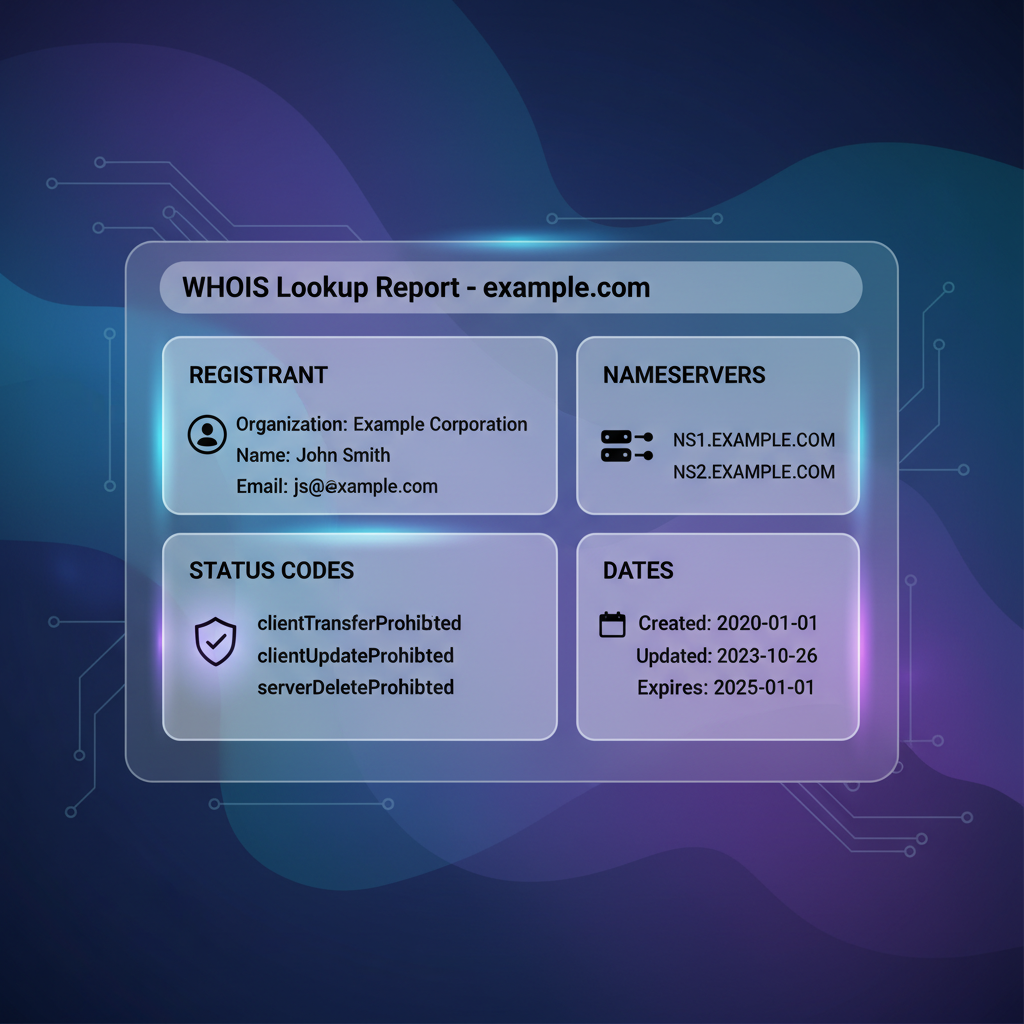
Is WHOIS Data Public? Privacy, GDPR, and Redacted Records Explained
Key Takeaways WHOIS is a foundational protocol for querying domain registration metadata, critical to domain lifecycle management, infrastructure...
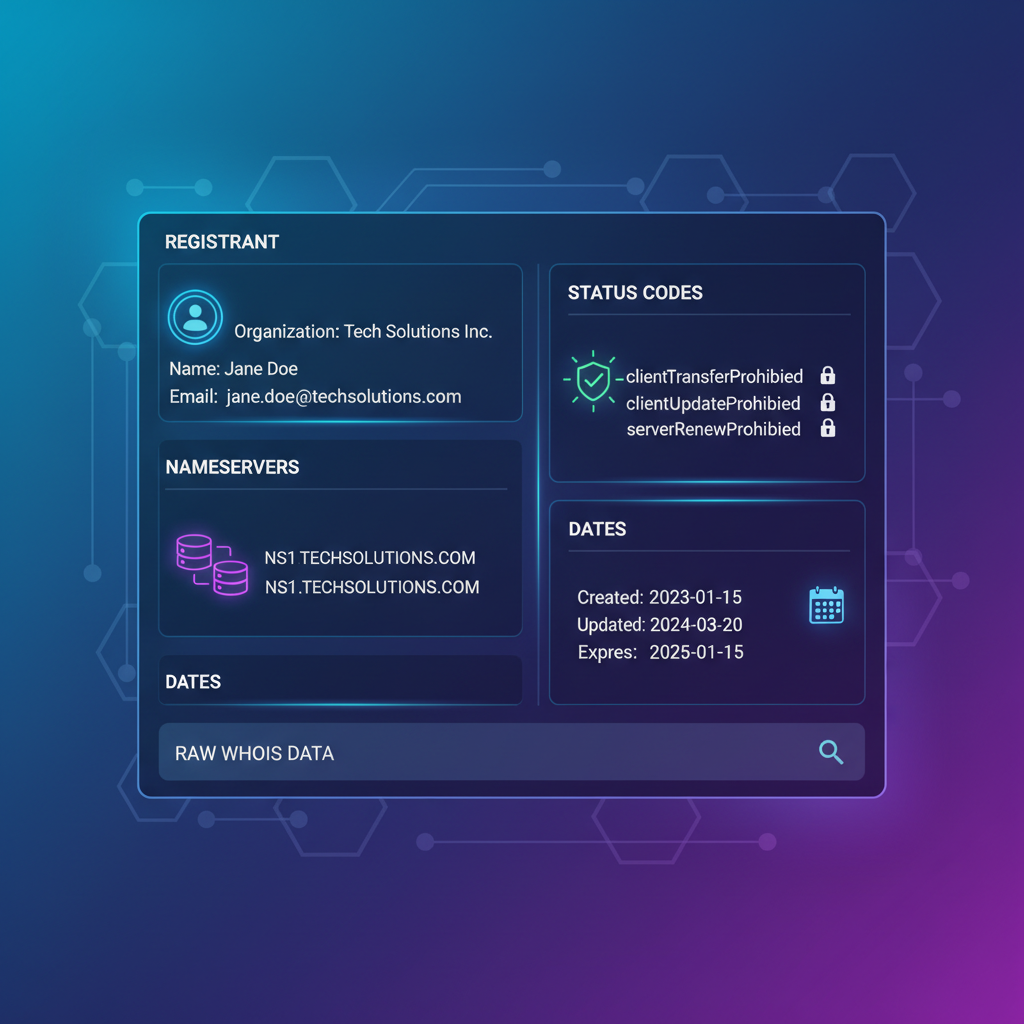
WHOIS vs RDAP: What’s the Difference and Why It Matters
Key Takeaways A detailed understanding of these dimensions equips engineers to implement future-proof domain data services conforming to...
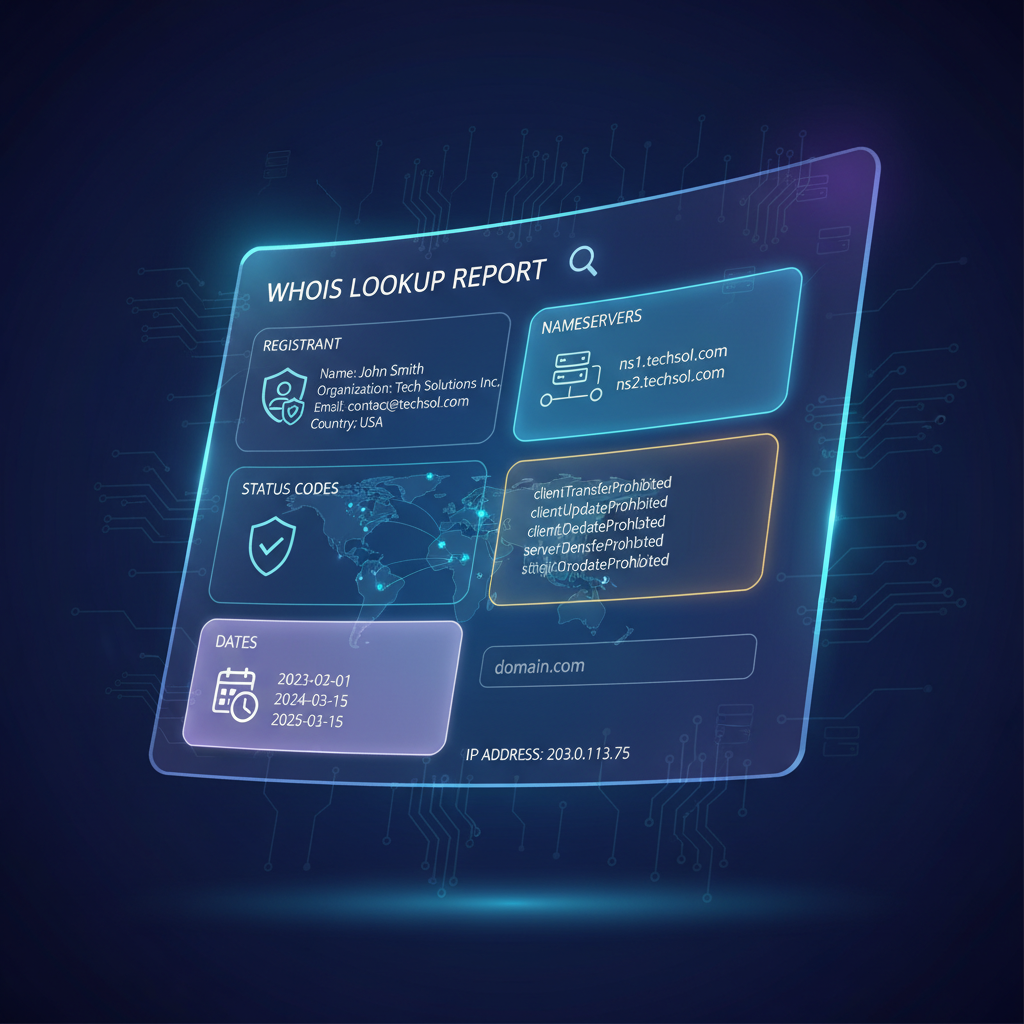
What Information Does a WHOIS Lookup Show? (Field-by-Field Breakdown)
Key Takeaways By dissecting WHOIS lookup fields with engineering rigor, teams can architect precise domain management tooling that...

How WHOIS Works: From Domain Registration to Public Records
Key Takeaways WHOIS operates as a foundational yet intricate protocol ecosystem for domain registration metadata management, enabling controlled...

What Is WHOIS? A Complete Guide to Domain Ownership Data
Key Takeaways This guide provides an in-depth exploration of WHOIS data structures, protocol mechanics, privacy implications, and practical...

Advanced Strategies for Scaling Monorepos: Tools and Techniques for Managing Massive Codebases
Introduction to Monorepos and Their Benefits Monorepos, or monolithic repositories, have gained popularity as a compelling solution for...
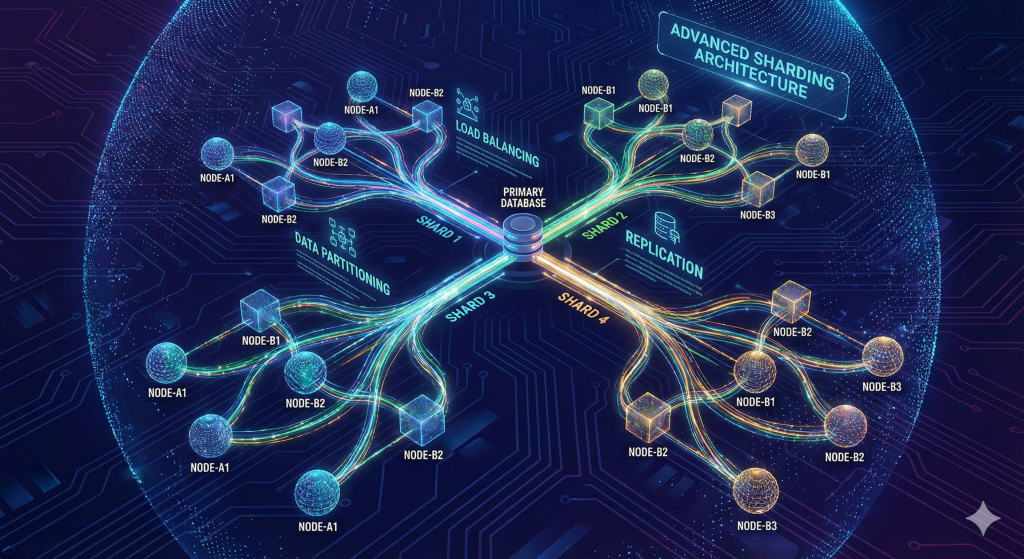
Mastering Advanced Database Sharding Techniques for Huge Applications: Database Sharding Patterns and Partitioning Strategies for Massive Scale
Introduction to Database Sharding In the era of massive, data-driven applications, ensuring that databases can scale seamlessly is...
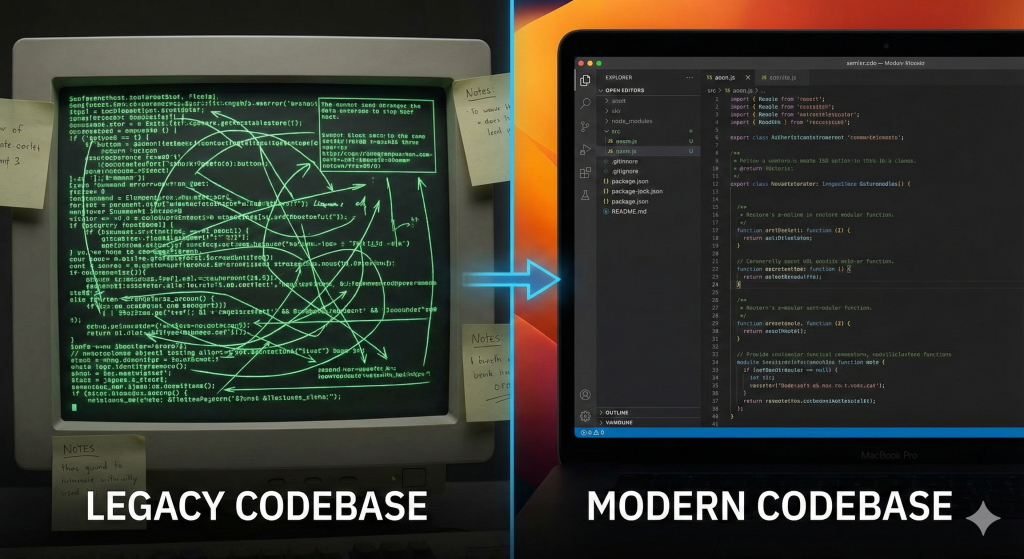
Refactoring Legacy Code: Advanced Strategies for Managing Technical Debt
Introduction to Legacy Code and Technical Debt In the ever-evolving landscape of software development, managing legacy code and...
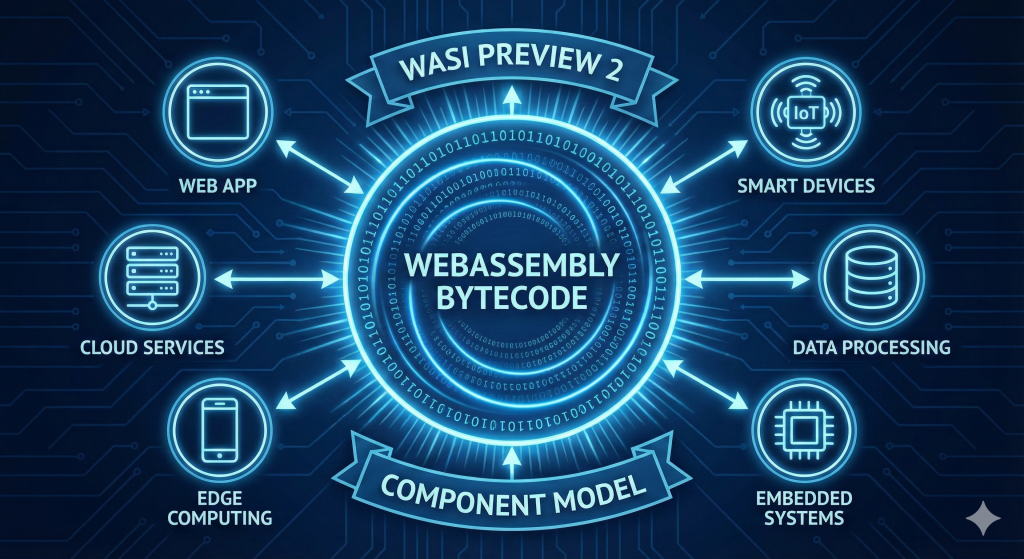
WASI Preview 2 and the WebAssembly Component Model: Practical Differences and Real-World Applications
Introduction to WebAssembly and Its Evolution WebAssembly (Wasm) has undergone a tremendous evolution since its inception. Initially designed...
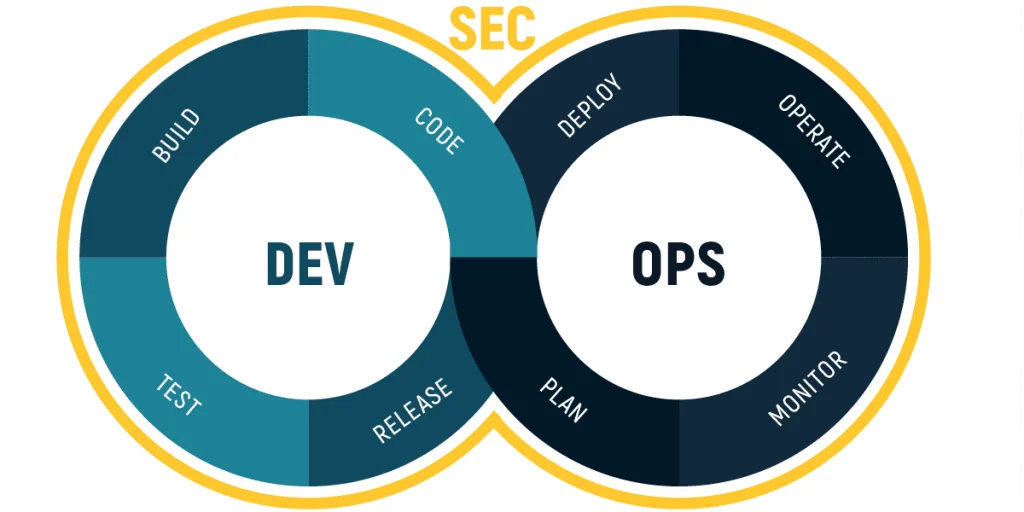
Implementing DevSecOps for Secure Software Development
Introduction to DevSecOps DevSecOps is transforming the way organizations develop and deploy applications by integrating security at every...
Concurrency Patterns in Go: Enhancing Performance and Scalability
Introduction to Go’s Concurrency Model Go’s built-in concurrency model is a game-changer for developers building high-performance, scalable applications....
Modular Monolith vs Microservices: When to Consolidate Your Architecture
Introduction to Software Architecture Paradigms In today’s rapidly evolving software landscape, architects and developers continuously face pivotal decisions...

Generative AI for Testing: Using GPT to Generate Tests and Find Bugs
Introduction to Generative AI in Software Testing The evolution of software testing has reached a new milestone with...
Implementing Continuous Integration and Deployment Pipelines for Microservices
Introduction to CI/CD in Microservices In today’s fast-paced software development landscape, Continuous Integration and Continuous Deployment (CI/CD) have...
Aligning Software Engineering Education with Industry Demands: Ensuring Future-Ready Graduates
Introduction: The Growing Divide Between Academia and Industry In today’s rapidly evolving technological landscape, there is an ever-growing...

Why should always run ‘composer install’ in production?
Most PHP developers today rely on Composer, a widely used dependency manager that simplifies managing application dependencies. However,...

Optimizing Docker Strategies for Deploying Multiple Ollama Models
Introduction to Ollama Models and Their Deployment Challenges The rapid advancements in AI and machine learning have essentially...

Building an MCP Server in Go: A Comprehensive Guide
Introduction to MCP and Its Benefits The Model Context Protocol (MCP) is an open standard introduced by Anthropic...

Integrating Bun.js Test Runner in Monorepos: Challenges and Solutions
Introduction to Bun’s Test Runner and Monorepos Monorepos have become a popular approach for managing multiple related projects...

Automating API Key Rotation in Serverless Applications: A Security Essential
Introduction: The Importance of API Key Rotation in Serverless Applications In the dynamic landscape of serverless applications [https://blog.whoisjsonapi.com/embracing-serverless-computing-a-comprehensive-guide-to-design-architectures-and-best-practices/],...